Home-based Threat Intelligence
Those of you who read my articles will recall that in my post titled “Escape from Imprisonment“, I enthusiastically discussed the advantages of using a router packed with security features. As I mentioned in the article, I had started using the dnscrypt-proxy tool to encrypt DNS traffic (Dns over HTTPS – DoH).
In today’s world where thermostats are getting smarter, smart TVs are equipped with cameras, and electric water heaters and irons are being turned into spy devices, insecure Internet of Things (IoT) devices connected to our home network pose a great risk to our security and privacy. As I was thinking about how to detect systems in our home network that have been hacked, infected, or contain backdoors, I remembered that thanks to the dnscrypt-proxy tool, I could also record DNS requests made by all systems, devices, and gadgets connected to the home network.
At the point where I could record DNS requests, I realized I could detect malicious systems in my home network by querying the domain names and IP addresses found in these DNS requests through cyber threat intelligence services like Open Threat Exchange (OTX) and Critical Stack. Without wasting time, I started thinking about the list of requirements to bring this idea to life.
First, I decided to install the syslog-ng package on the Ubuntu operating system running on my Mini-PC, which is always at hand and always comes to my aid in such situations. After installing the package, I configured it to record incoming DNS requests in the date.log file under the /var/log/dns-sys/sender’s-ip-address directory and saved this configuration in the /etc/syslog-ng/conf.d/dns-sys.conf file.
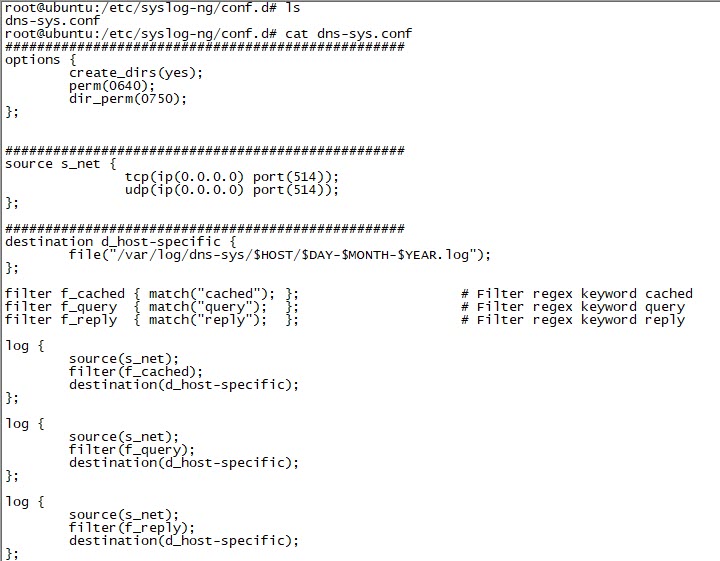
In the next step, to make the dnscrypt-proxy tool log DNS requests to the router’s syslog, I added the line ‘log-queries’ to the /jffs/configs/dnsmasq.conf.add file. Then, to make the router display these requests on its syslog page, I set the ‘Default message log level‘ and ‘Log only messages more urgent than‘ values to ‘debug‘, and to redirect these messages to the syslog-ng application running on Ubuntu, I defined the ‘Remote Log Server‘ value as the IP address of Ubuntu.
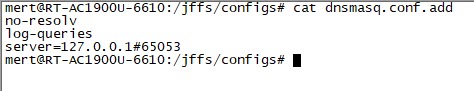
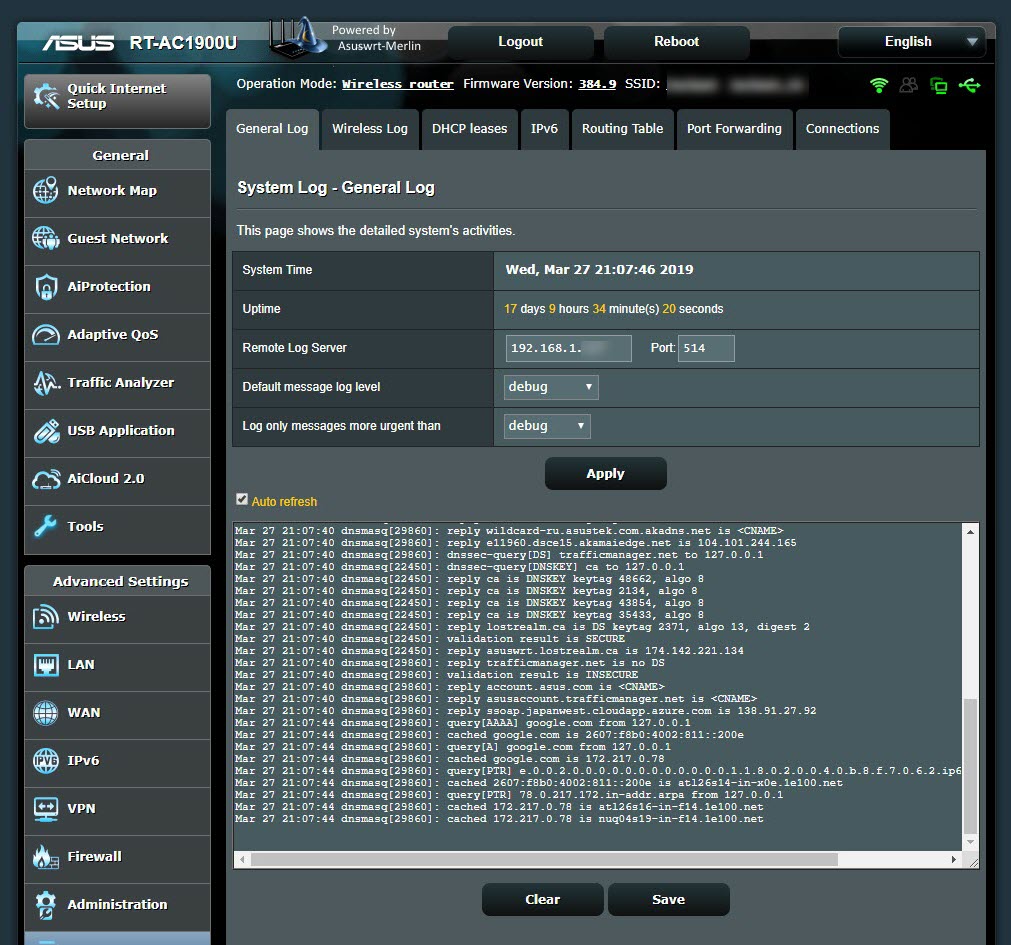
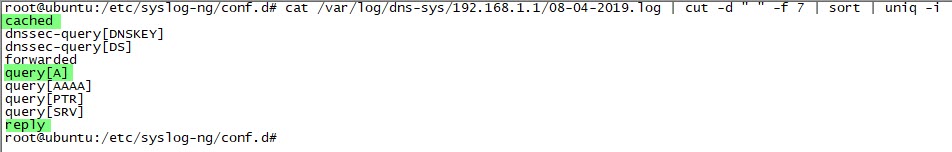
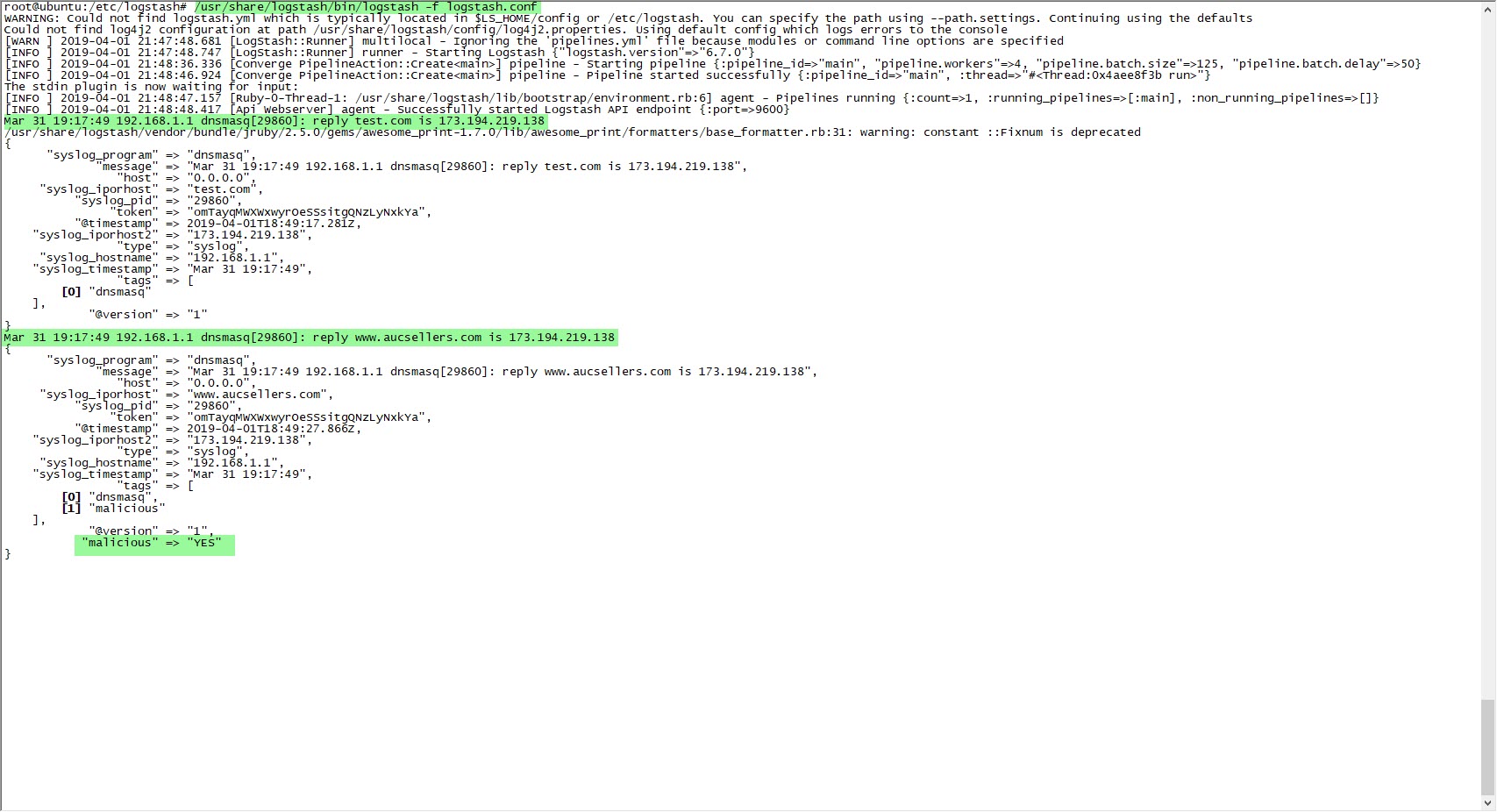
I started examining the syslog-ng records one by one and looking into which types of records I needed to focus on for threat intelligence. After learning that I could use the query[A], cached, and reply information in the records, I thought I could send these records to Security Onion, which integrates with OTX. After installing and running Security Onion’s 16.04.5.6 operating system, I noticed that the logstash service (so-logstash) wasn’t working at all. Despite my struggle, I was unsuccessful and started researching alternative methods.
When I shared a message on Twitter about needing to install ELK, I received messages suggesting that I could use cloud and ready-made ELK systems. As I was considering whether to install ELK on Ubuntu or use a cloud system, I learned that Logstash, which has Grok filter and Translate filter plugins, was tailor-made for this job.
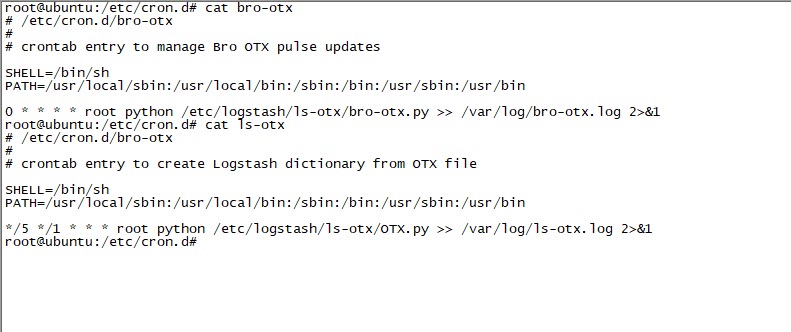
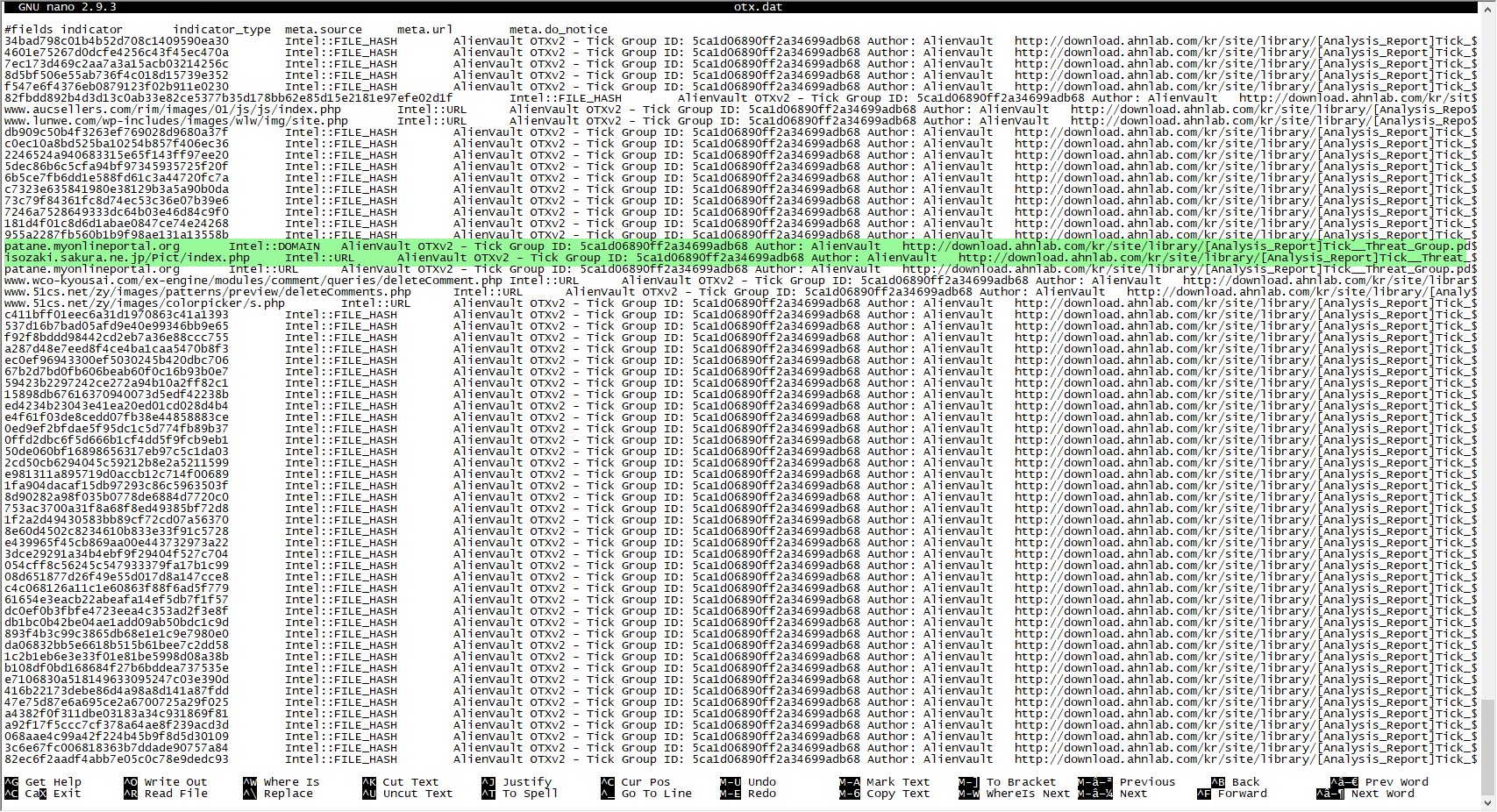
I started modifying the securityonion-otx script file, which was developed for Security Onion – OTX integration, according to my needs. I set the bro-otx file to save threat intelligence information from OTX to the /etc/logstash/ls-otx/otx.dat file every hour. I also configured the OTX.py file to extract only domain name information from the malicious URL and DOMAIN entries in the otx.dat file and save it as the /etc/logstash/translate/OTX.yaml file to be read by the Translate filter at the 5th minute of every hour.
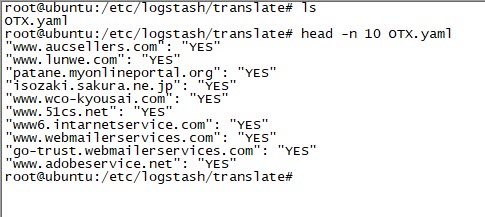
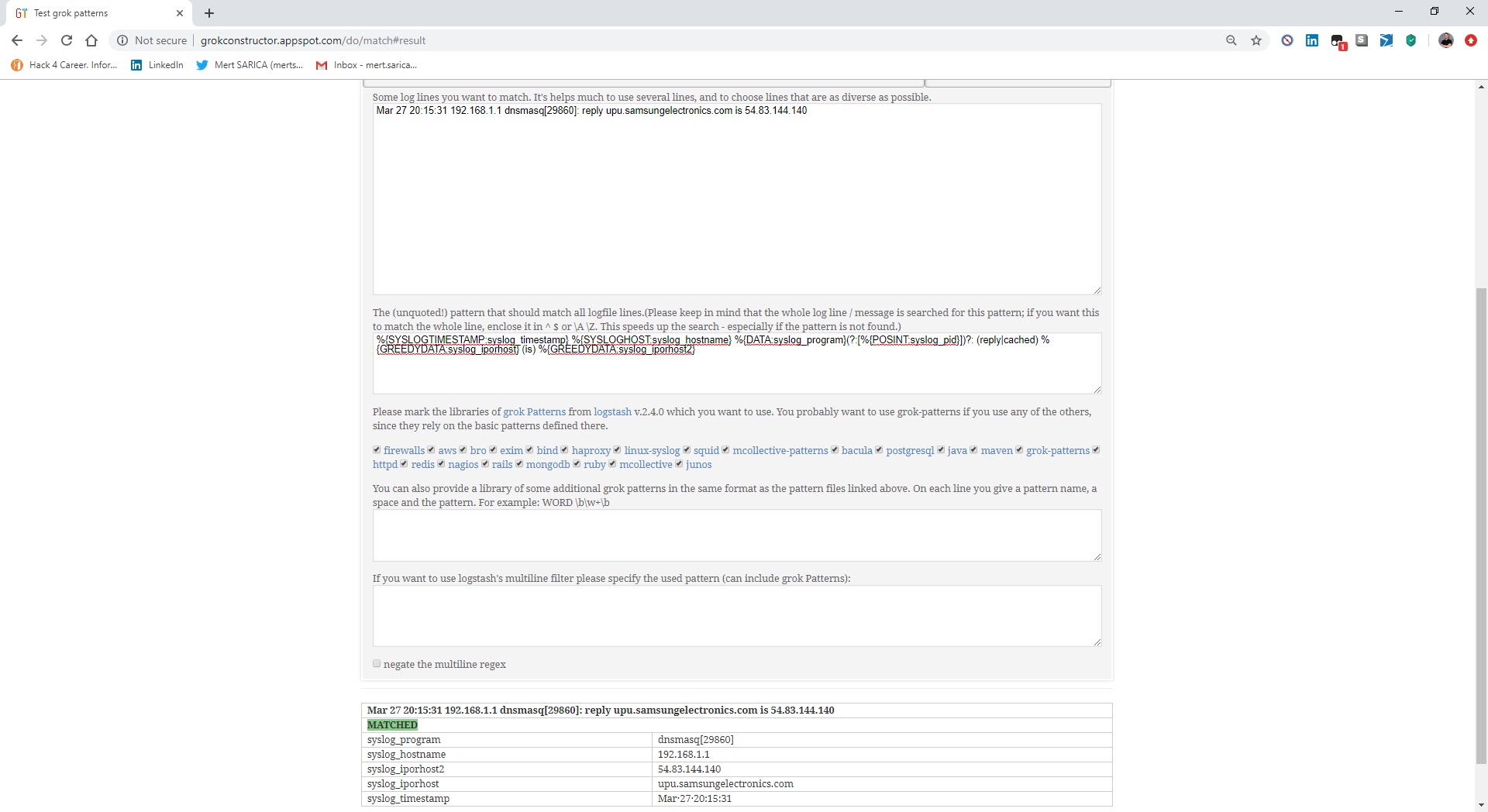
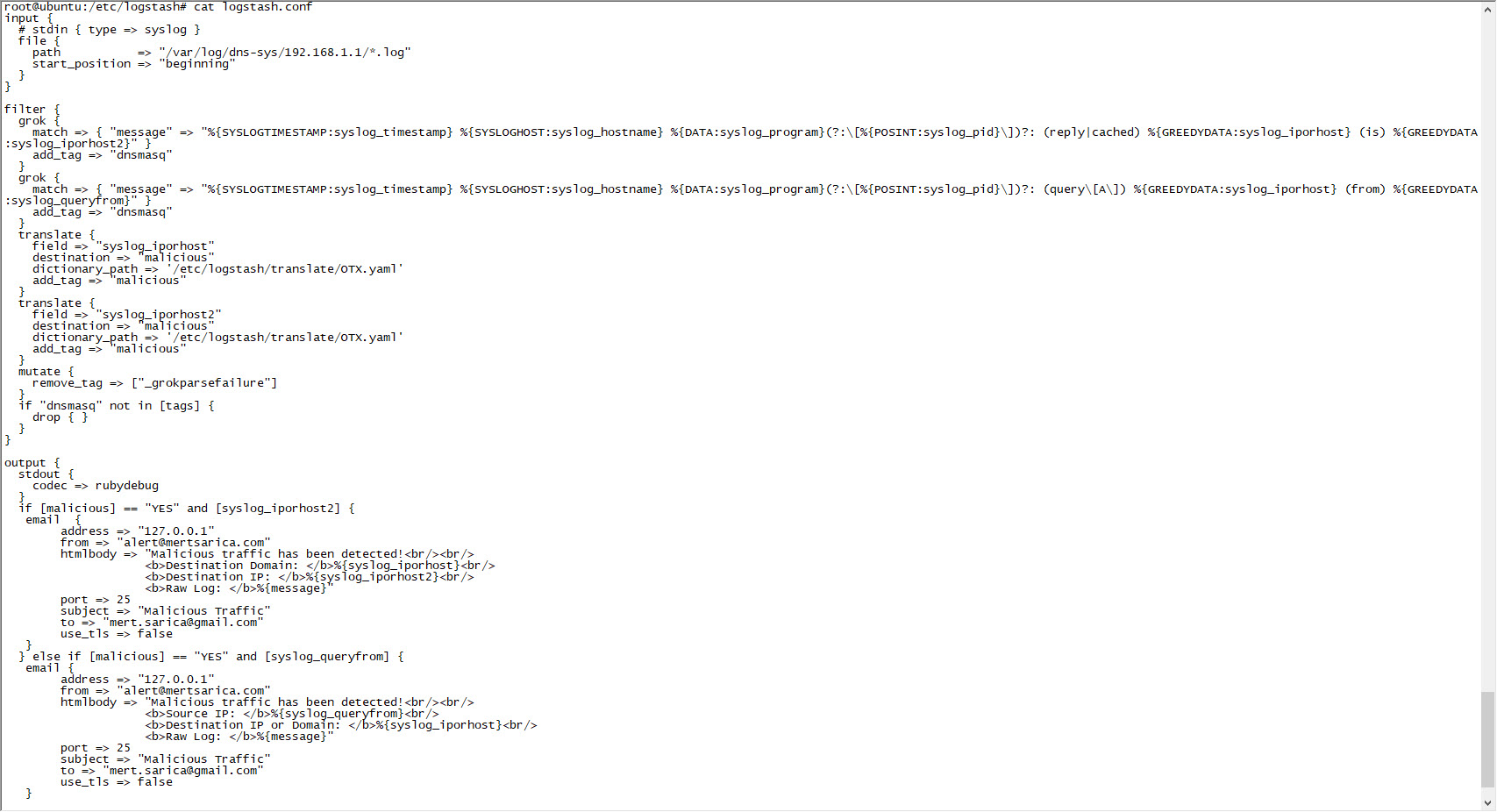
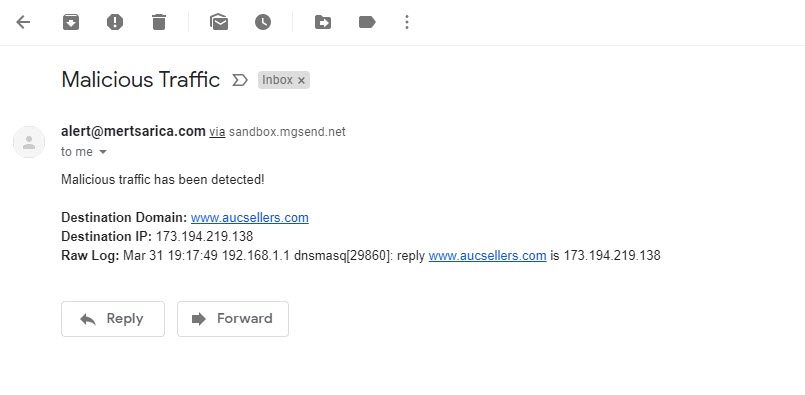
In the configuration file of Logstash (logstash.conf), I defined the rules to read DNS records logged by syslog-ng with the Grok filter and to send an alert via email if any of the IP addresses or domain names in these records match with those in the OTX.yaml file using the Translate filter. Then I restarted Logstash and made an nslookup for the address www[.]aucsellers[.]com listed in the OTX.yaml file. With this, the alert was successfully generated and sent to me by email, and I had successfully implemented the home-based threat intelligence service. :)
Hope to see you in the following articles.