Phishing Cloaking Techniques
CONTENTS
Introduction
Those of you who have read my blog post titled Investment Scammers have seen how scammers try to lure innocent people into their traps through fake ads on social media and networks. Just as in that article, websites play a critical role in fraud attempts and are essential for the operations of scammers.
In most cases, scammers manage to bring their victims to these websites through persuasion. From there, they steal the victims’ information and then proceed to the next stage of their operation—contacting the victims via calls or messaging platforms like WhatsApp and Telegram. As one might expect, in this final stage, their aim is to trick victims into making money transfers and thus achieve their malicious goals.
Of course, the more experienced among these scammers are aware that companies fighting against cybercrime, such as SOCRadar and Netcraft, as well as national entities like USOM, scan and report these fraudulent websites and then have suspicious/malicious ones taken down. To bypass such scans, they take advantage of a technique called Cloaking, which has been used in the SEO world since 1996. In this article, I aimed to raise awareness by presenting the most common cloaking techniques and also introducing a tool I developed with artificial intelligence to easily bypass them.
Cloaking is when the content shown to search engines by a website differs from the content shown to users; this is a practice that violates search engine optimization (SEO) rules. In this method, where different content is served to users and search engines, the goal is to gain an advantage in search results.
Purpose and Method of Cloaking
Search Engine Optimization (SEO):
Cloaking is a technique used to ensure that a website ranks higher in search engine results.Different Content Delivery:
Search engine bots are made to believe that the website contains richer content filled with keywords relevant to search queries. However, real users are shown a different and usually less optimized version of the site.Malicious Use:
This method is used to trick the algorithms of search engines such as Google and to display spam or misleading content to users.
To conduct a security analysis on phishing sites that use cloaking techniques, I first needed access to their source code. Since obtaining these on demand is not practically possible, I once again turned to the help of SOCRadar, as I did in my previous articles. :)
Since the SOCRadar platform not only detects phishing sites but, when necessary, can also obtain their source code to trace back to the threat actors behind them, I decided to acquire the source code of 500 phishing sites targeting Turkish citizens and perform a security analysis on them.
Geographic Cloaking
First, I examined a website belonging to the threat actor I covered in my Investment Scammers blog post. This threat actor, who has continued their fraud operations non-stop for a year, registered the domain name navoisco[.]info on August 6, 2025 and started using the website for fraudulent purposes on August 13, 2025.
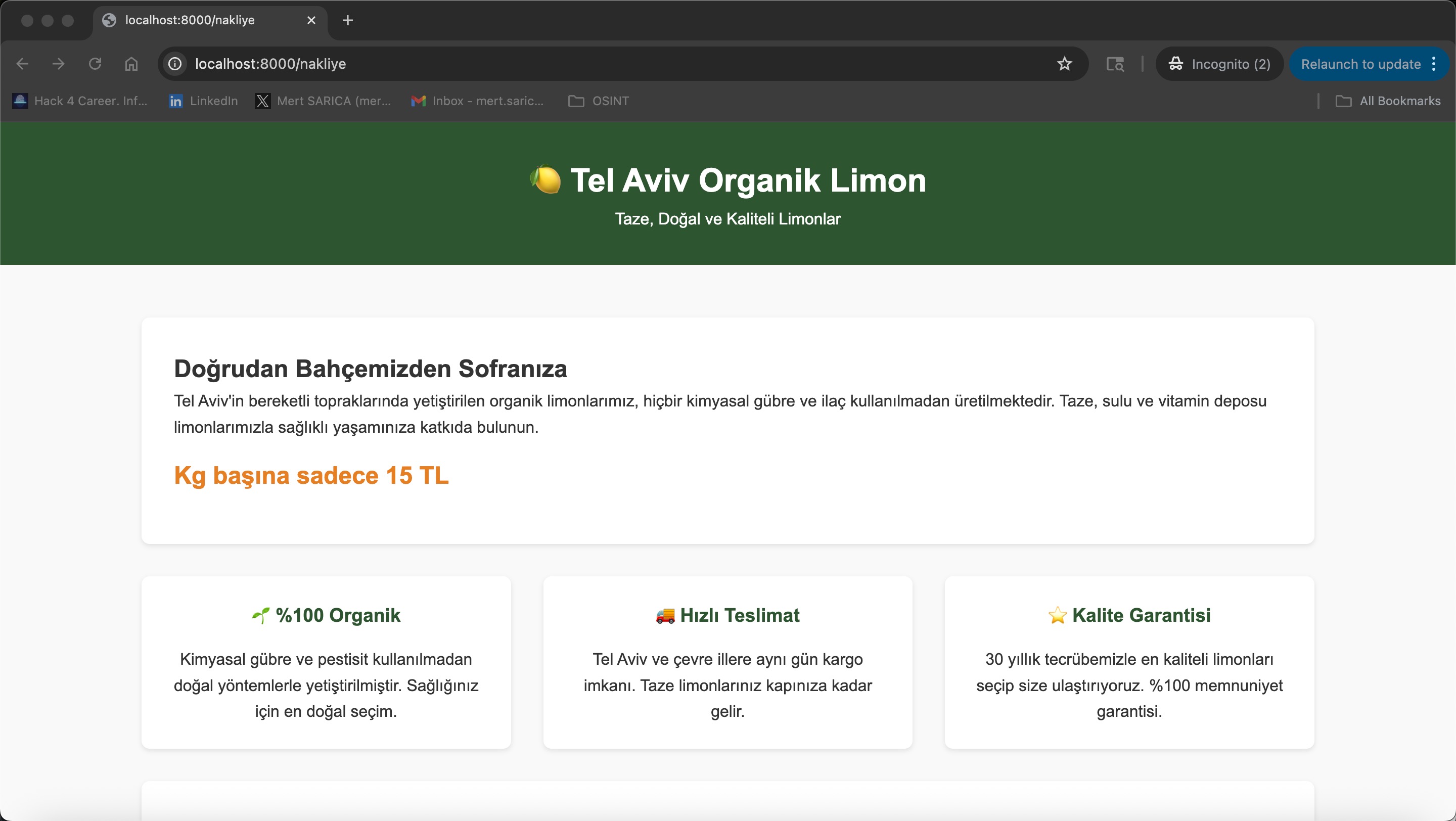
When you visited this website from abroad, you were presented with content selling surf products. However, when accessed from Turkey, it appeared as a fraudulent webpage exploiting the name of the defense company Baykar, in short using the Geographic Cloaking technique. When you searched for this address on the Google search engine, thanks to this cloaking method used by the scammers, it appeared in the records as a store selling surf products.
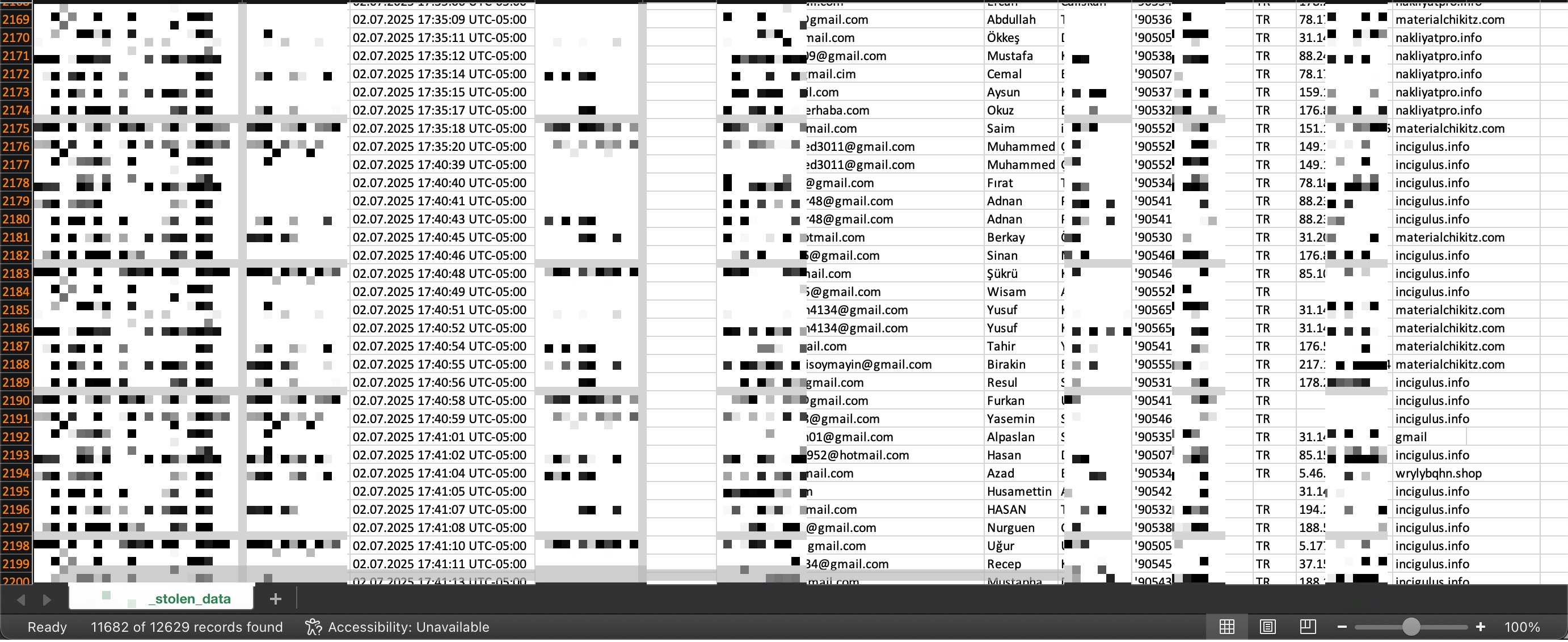
Note: I have been monitoring these threat actors for more than a year and concluded that they are Russian. They mainly carry out their operations through Ukrainian IP addresses (185.38.218.86, 185.237.75.100, 91.123.155.63). Since February 2025, they have launched 699 phishing websites, targeting approximately 9,000 Turkish citizens and stealing their personal information (name, surname, email address, phone number, IP address).
User-Agent Based Cloaking
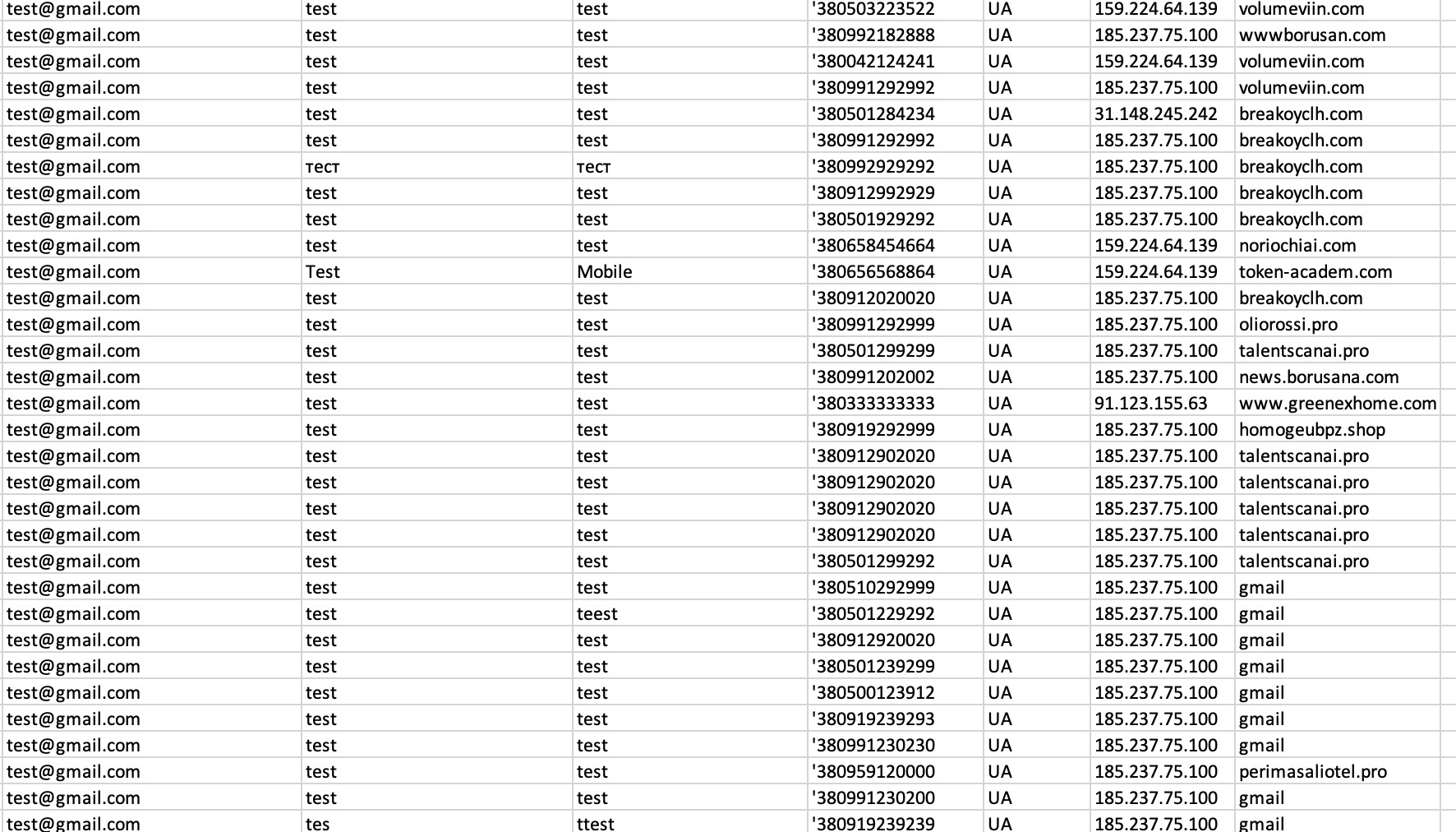
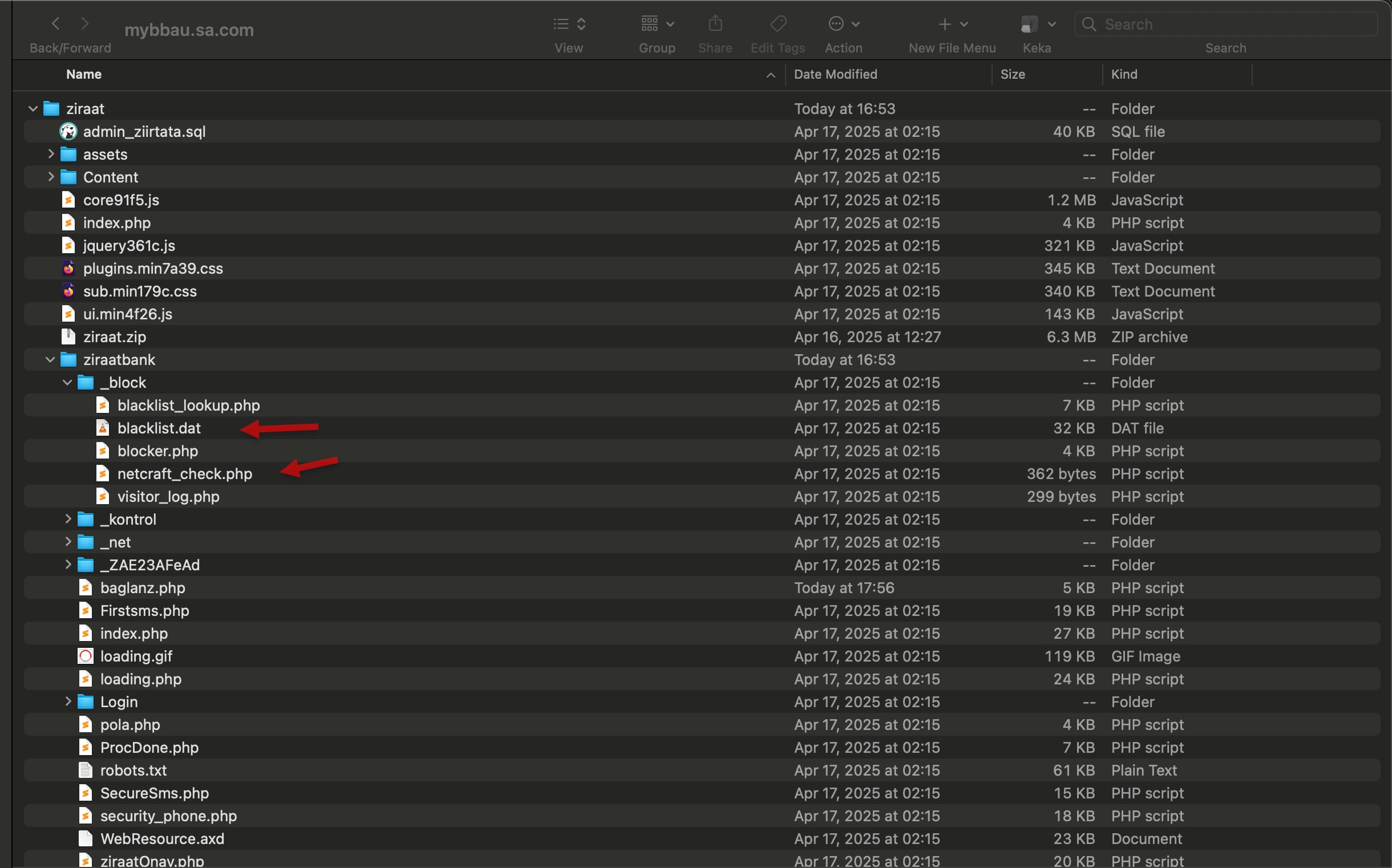
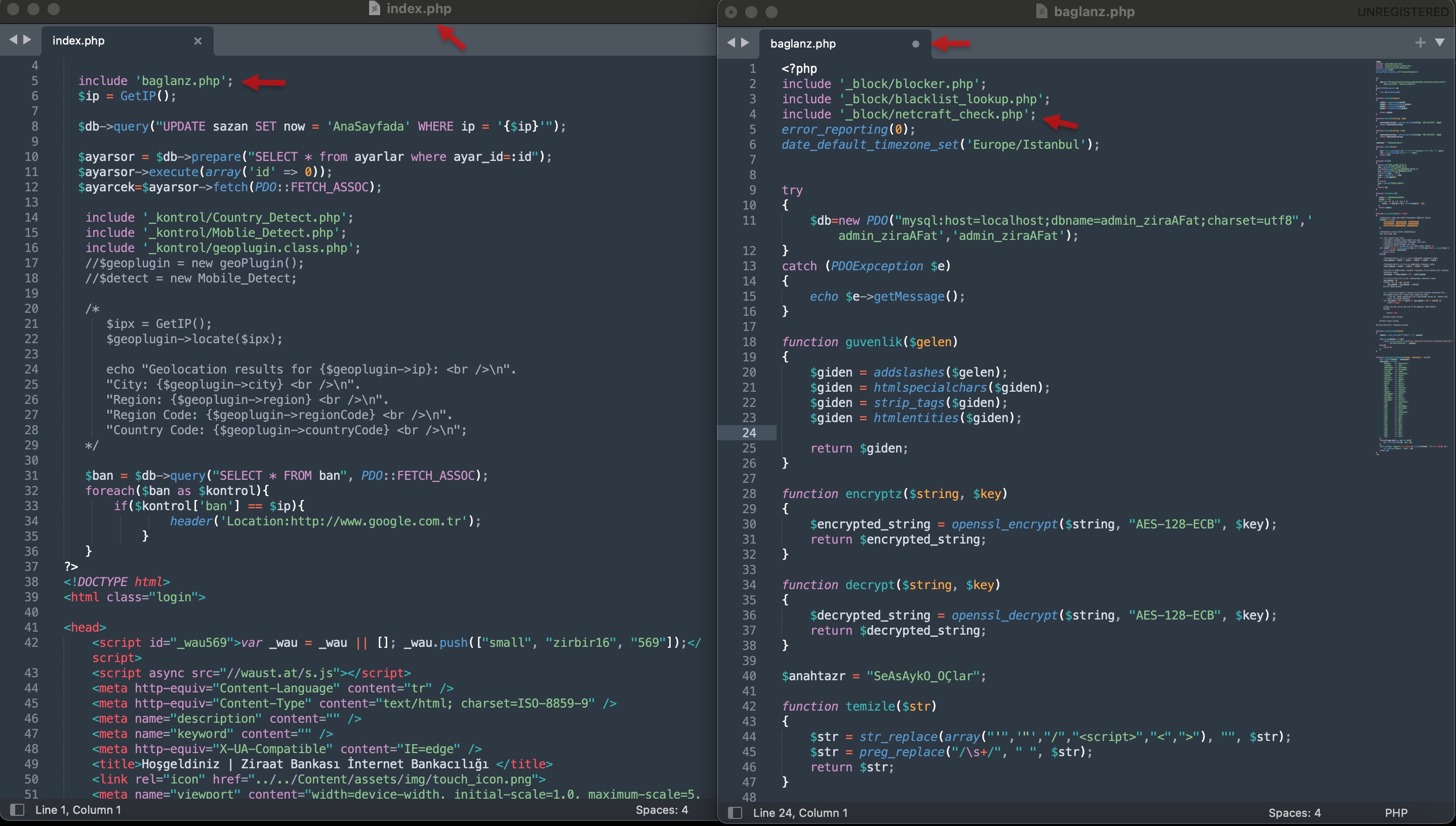
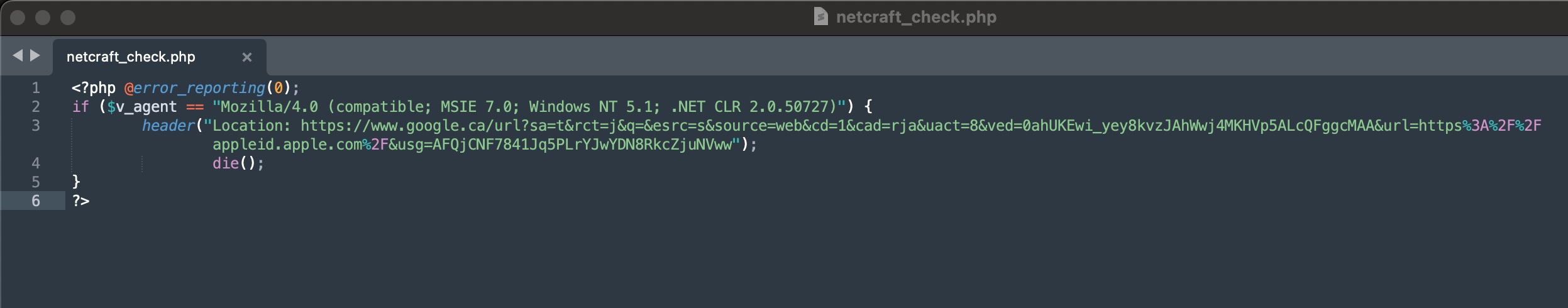
Secondly, on April 17, 2025, I began examining the source code of the phishing site mybbau[.]sa[.]com, which targeted Ziraat Bankası customers, and among the files, the one named netcraft_check.php caught my attention.
Netcraft is a UK-based cybersecurity and internet measurement company that has been operating since 1995. It is best known for its phishing and abuse reporting services and also provides hosting analysis and internet infrastructure statistics.
In this file, which was called from the index.php file located in the ziraatbank subfolder of the phishing site, there was a User-Agent string believed to be used by Netcraft to detect phishing sites. When a connection was made to the website with this string, the user’s browser was redirected via google.ca to the web address https://appleid.apple.com, thereby carrying out the cloaking process.
Blacklist-Based Cloaking
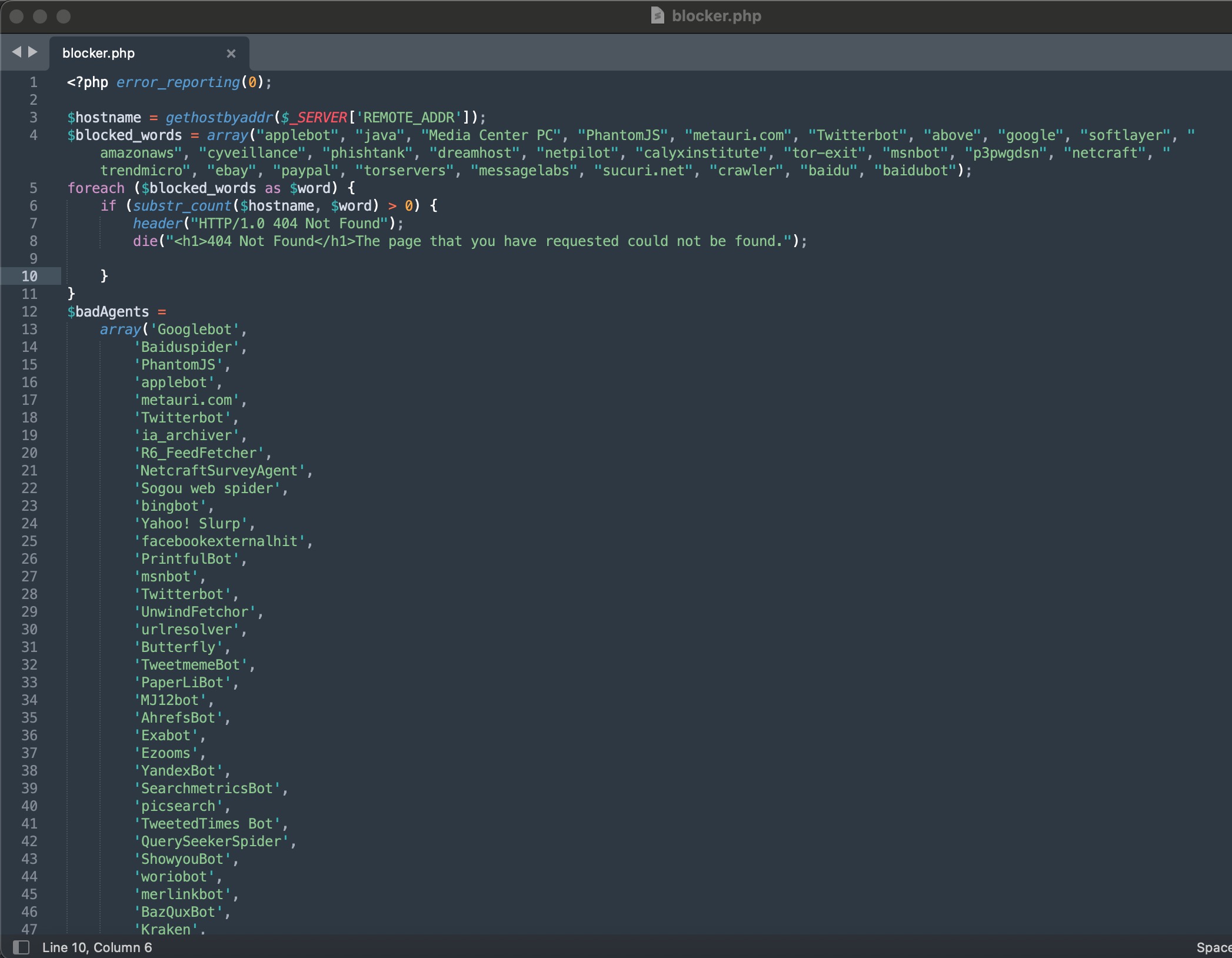
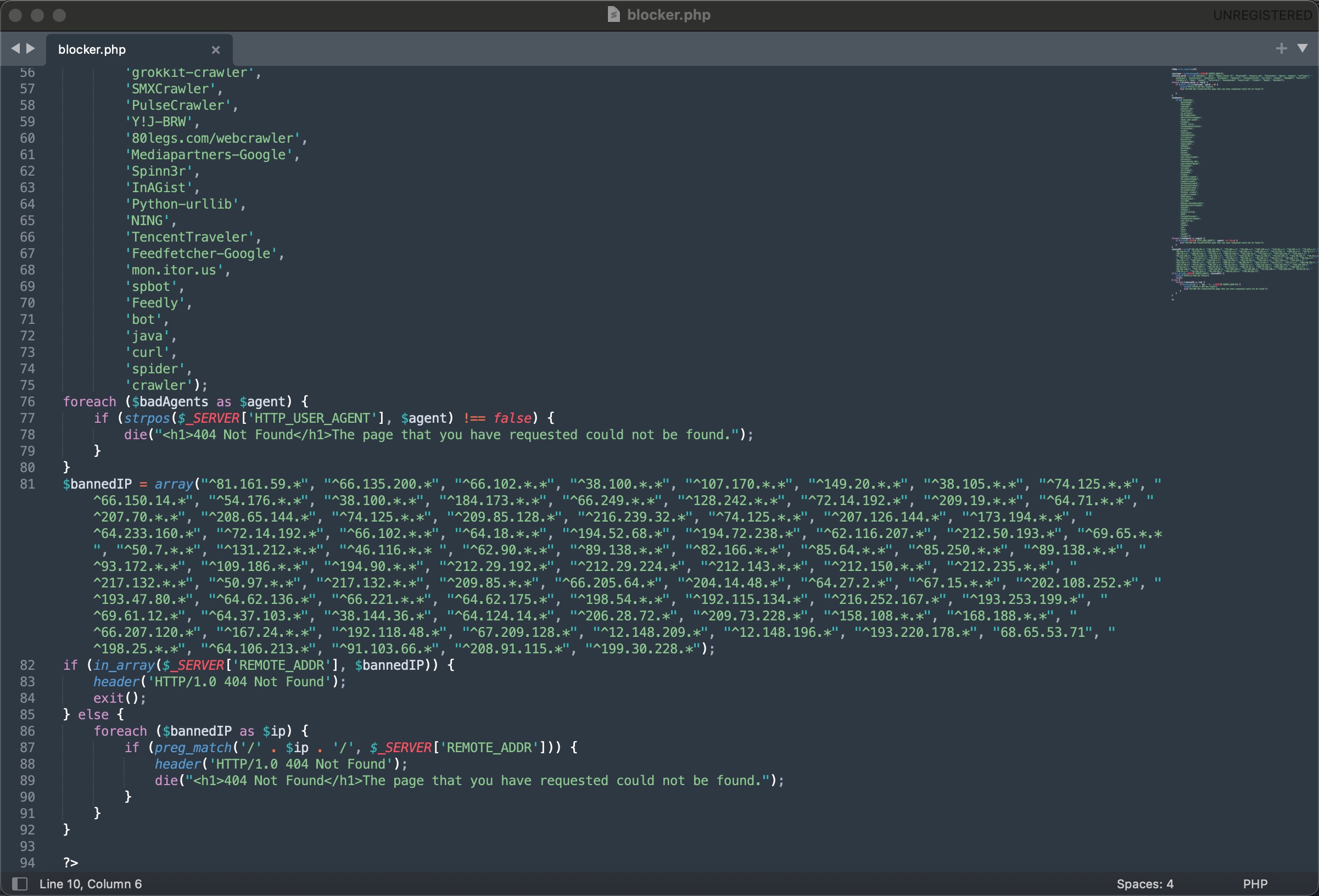
While looking through the files, the blocker.php file referenced in the index.php file caught my attention. When I examined this file, I saw that it performed blacklist checks against the IP address connecting to the website and its reverse DNS record. If one of these was detected, instead of displaying the site’s content, the server returned a 404 Not Found error, thereby carrying out the cloaking process.
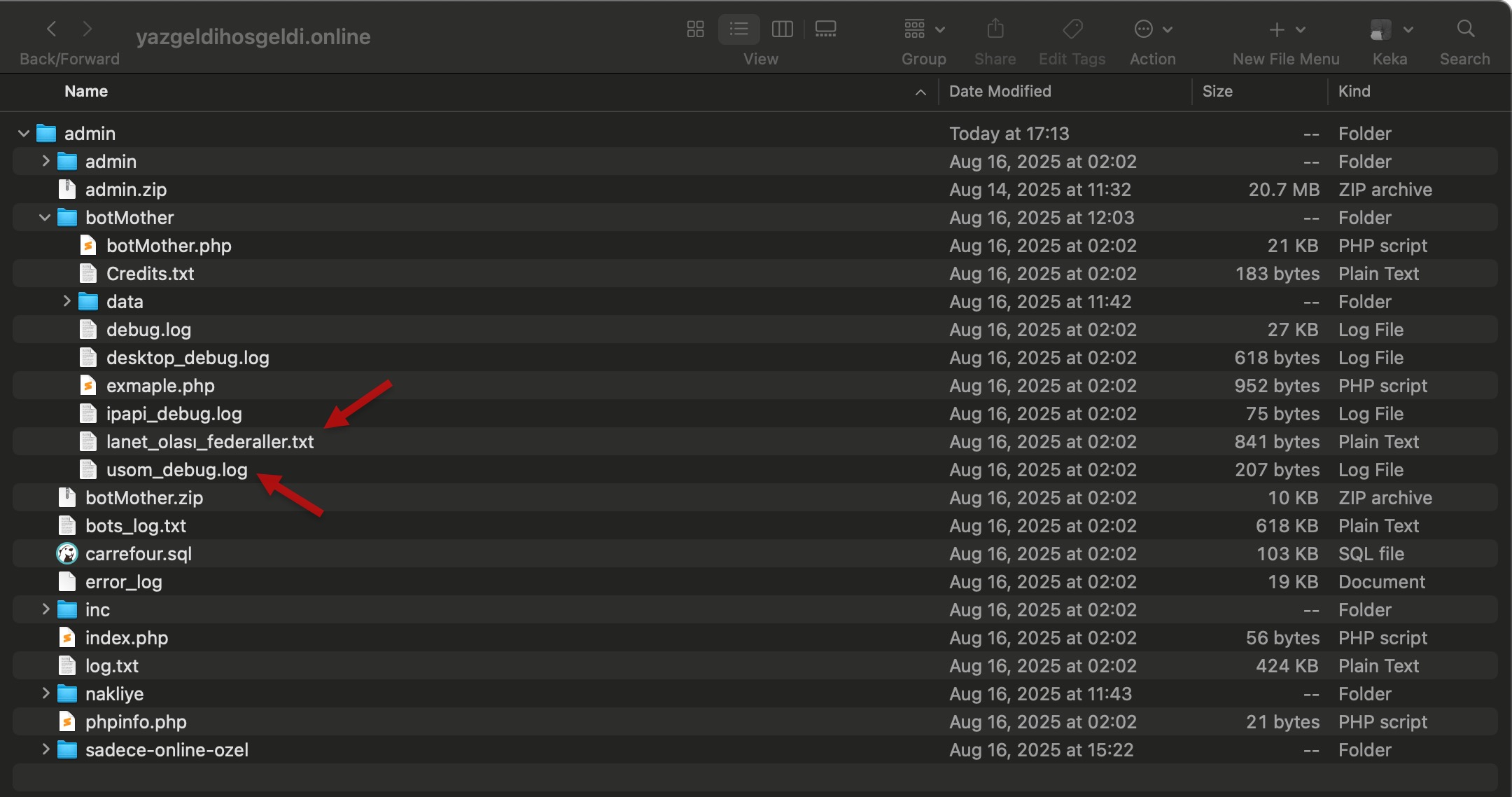
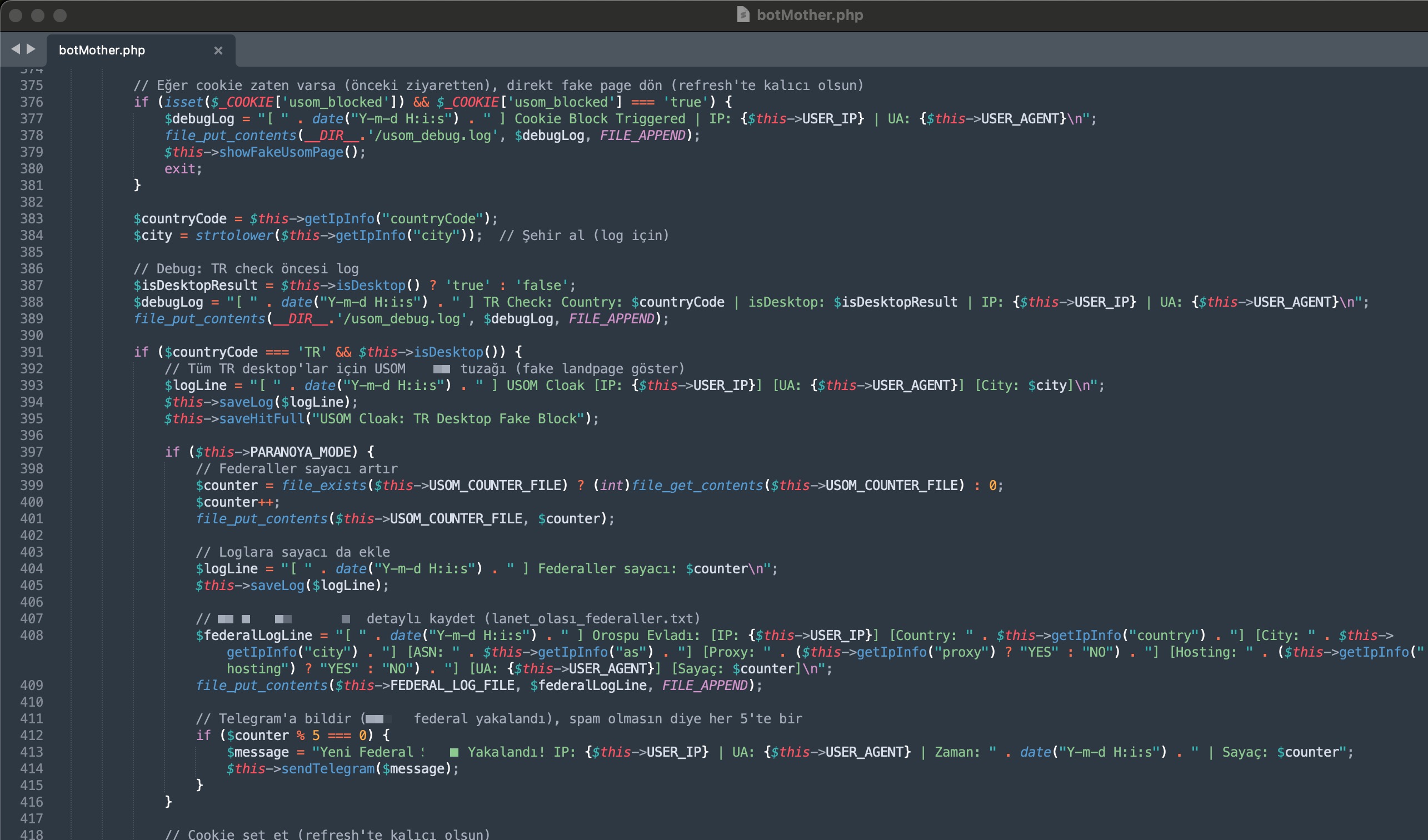
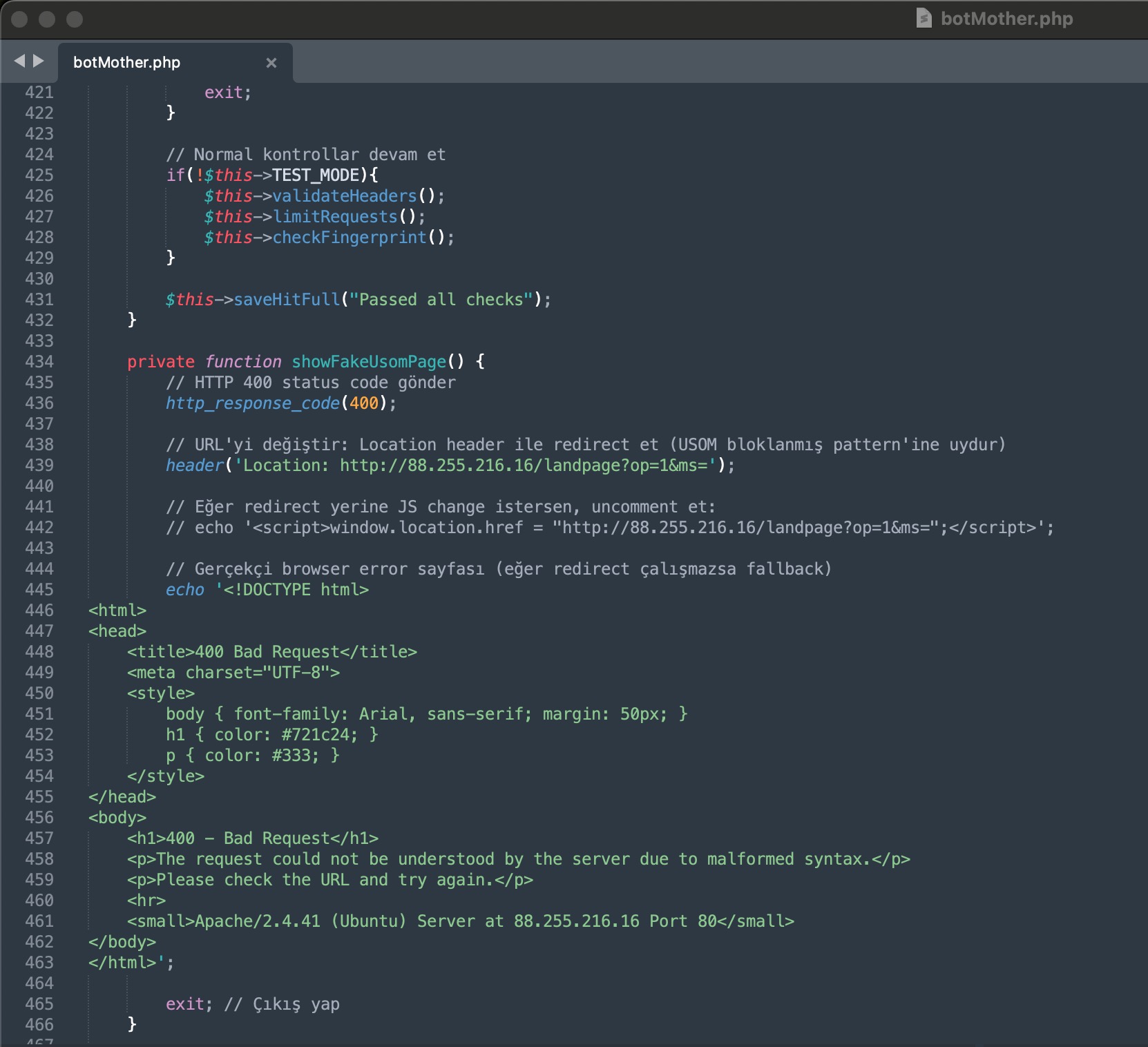
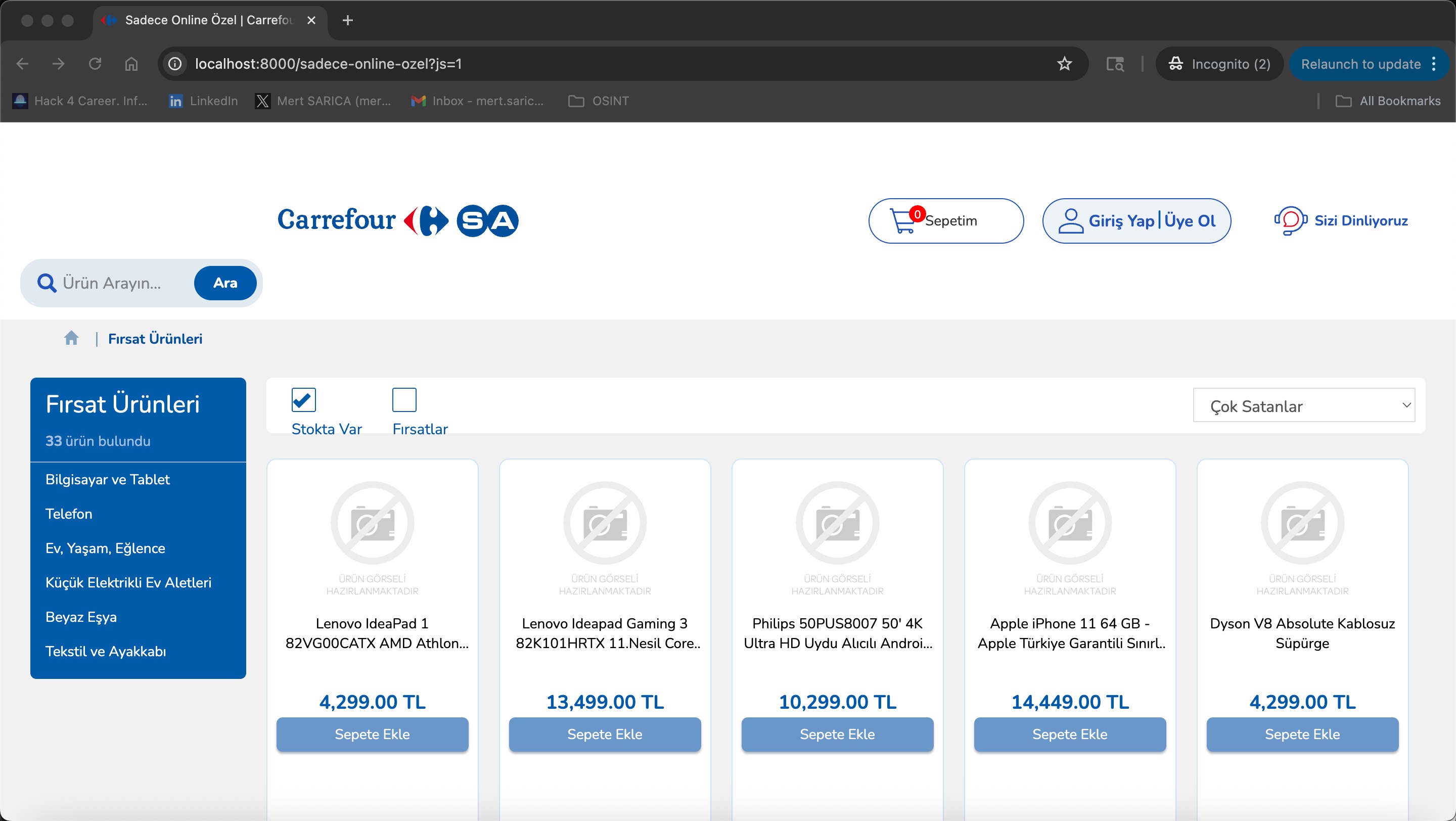
On August 16, 2025, when I looked at the source code of another phishing site created to target the CarrefourSA brand with the domain name yazgeldihosgeldi[.]online, this time I noticed the name USOM in one of the files. When I examined the botMother.php file located in the same folder, I saw that it contained various checks related to USOM. In one of the checks, people accessing the site from their computers who suspected the site were deceived and redirected to a fake USOM blocking page—in short, an attempt was made to prevent the site from being reported.
Abra Kadabra
Of course, since I had the source code of phishing sites obtained from SOCRadar, reaching the real content by bypassing cloaking techniques through static code analysis was quite easy. But what about a cybersecurity center analyst, threat intelligence analyst, or threat researcher who doesn’t have access to the source code and is tasked with evaluating a report—how could they access the real content of a phishing site that uses such cloaking techniques?
To answer this question, as in my previous articles, I once again turned to ChatGPT, this time asking it to write code that bypasses cloaking techniques. The result was a tool called Cloaker Probe.
Cloaker Probe: To access the real content of a website that uses cloaking techniques, this tool utilizes proxy support to connect from different countries, as well as a large set of User-Agent strings. It then searches the website content for suspicious keywords (login, password, credential, etc.) and, if detected, issues a warning (PHISH).
To test the tool on the source code of the mybbau[.]sa[.]com phishing site, I first navigated to the folder containing the source code and ran the command below to launch a local copy of the website on my network.
php -S localhost:8000
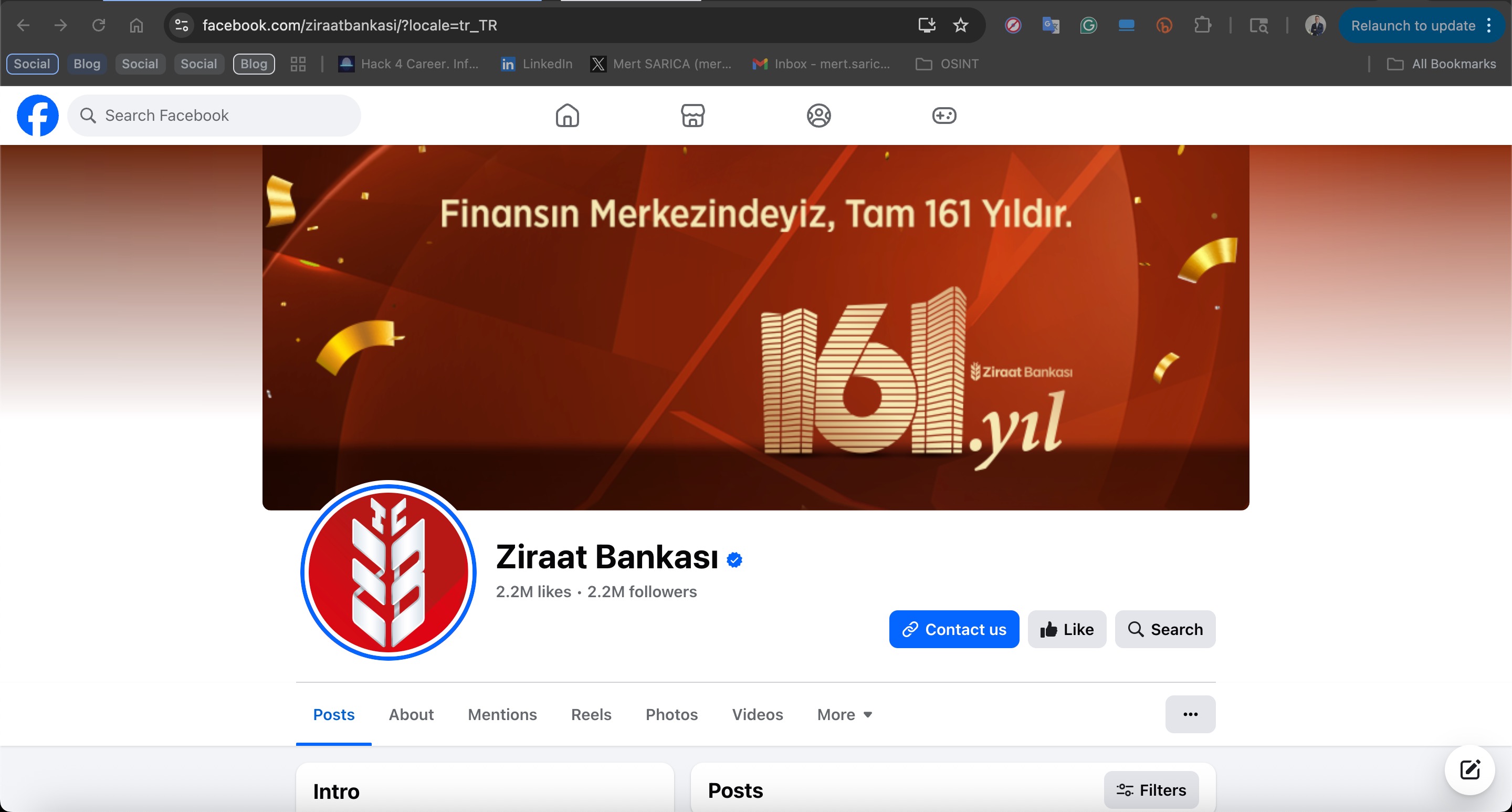
When I tried to access http://localhost:8000 via my web browser, instead of displaying the phishing site’s content from the main file (index.php), the cloaking technique redirected me to Ziraat Bank’s official Facebook page.
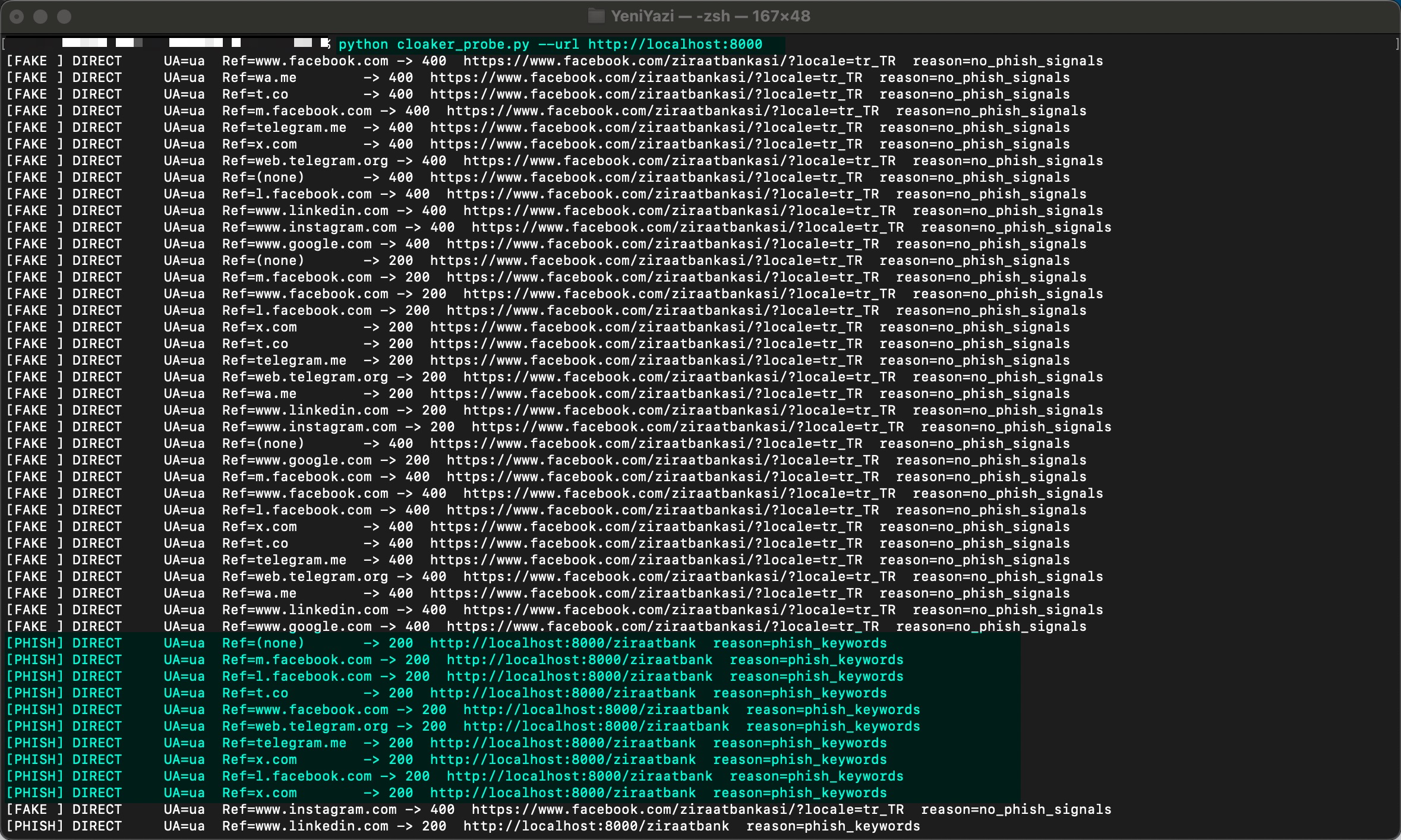
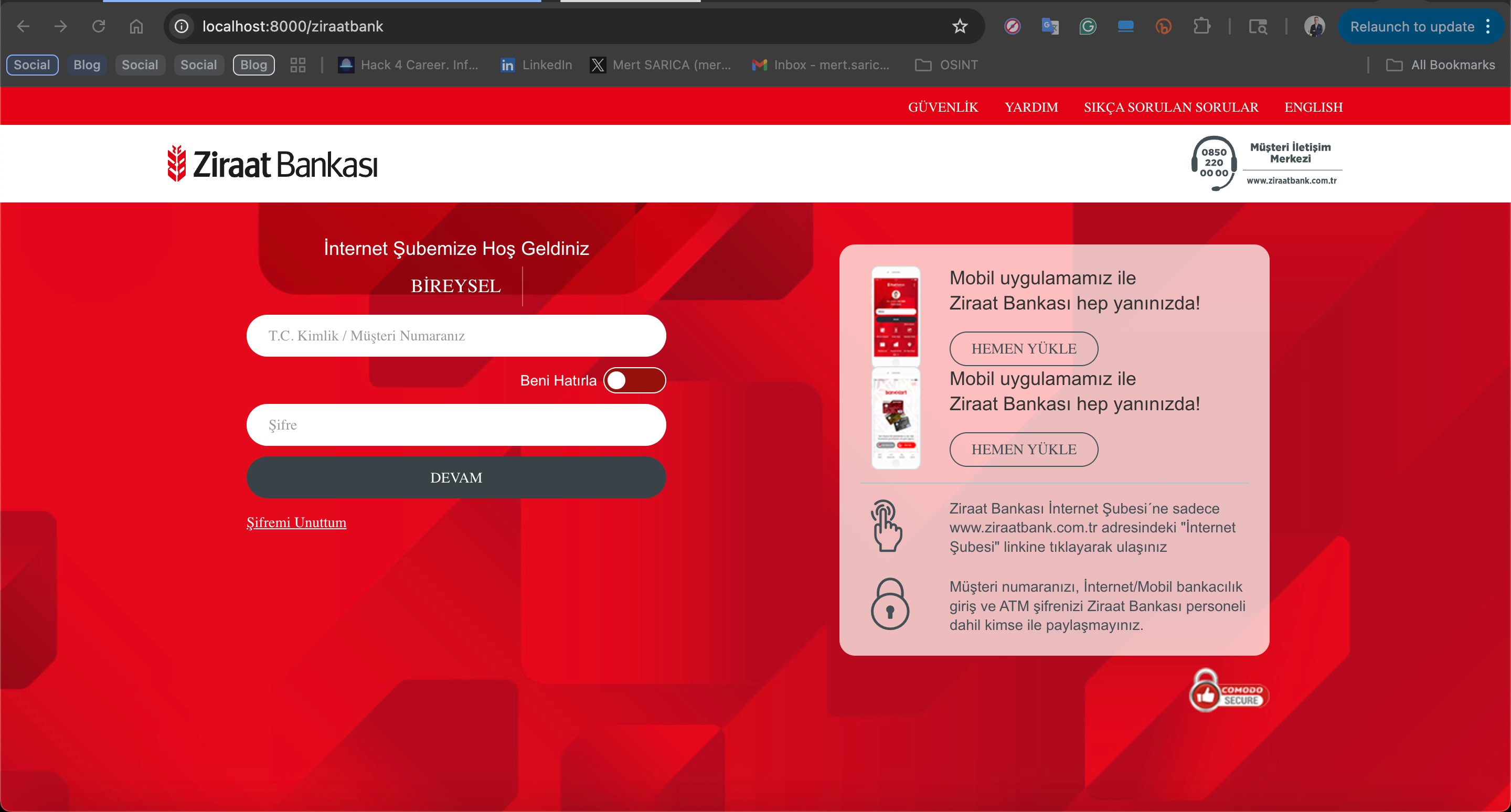
To bypass the cloaking technique, I immediately gave the Cloaker Probe tool a try by running the command python cloaker_probe.py –url http://localhost:8000, and within seconds I saw that the tool was able to successfully reach the phishing content and achieve its purpose.
Conclusion
In recent years, as fraudsters and threat actors have been using all kinds of tactics and techniques to lure victims into their traps, as end users we must be extremely cautious about the websites we visit and where we enter our information, never letting our guard down.
On the other hand, as SOC analysts, cyber threat intelligence analysts, and threat researchers, you can leverage artificial intelligence to develop new tools against the methods and tactics used by threat actors and fraudsters, helping you speed up and simplify your work.
Hope to see you in the following articles.