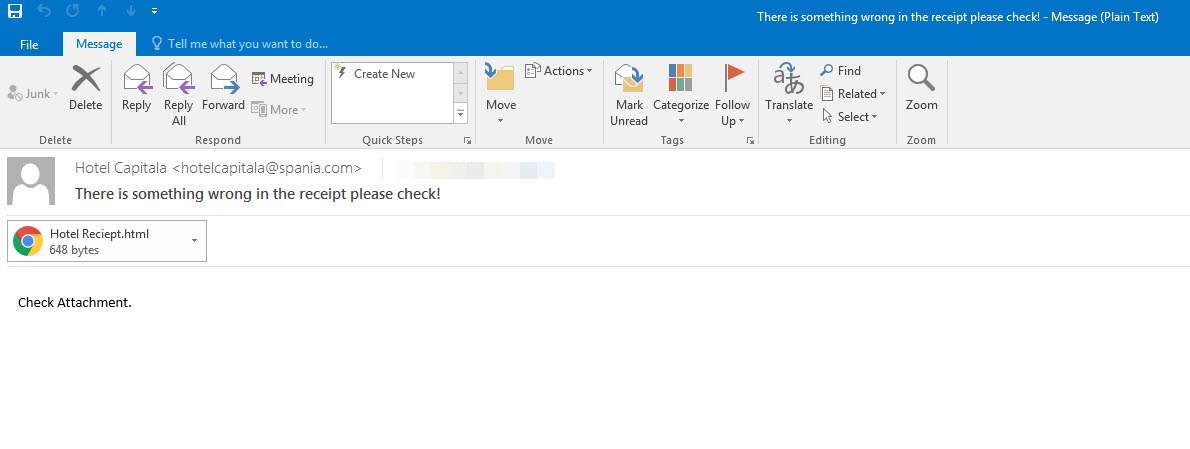
You Can Run, But You Can’t Hide
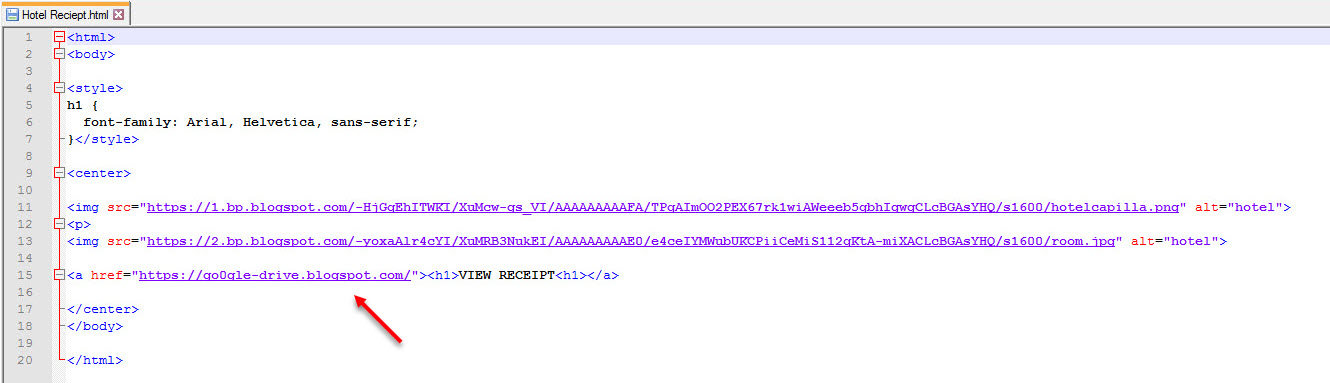
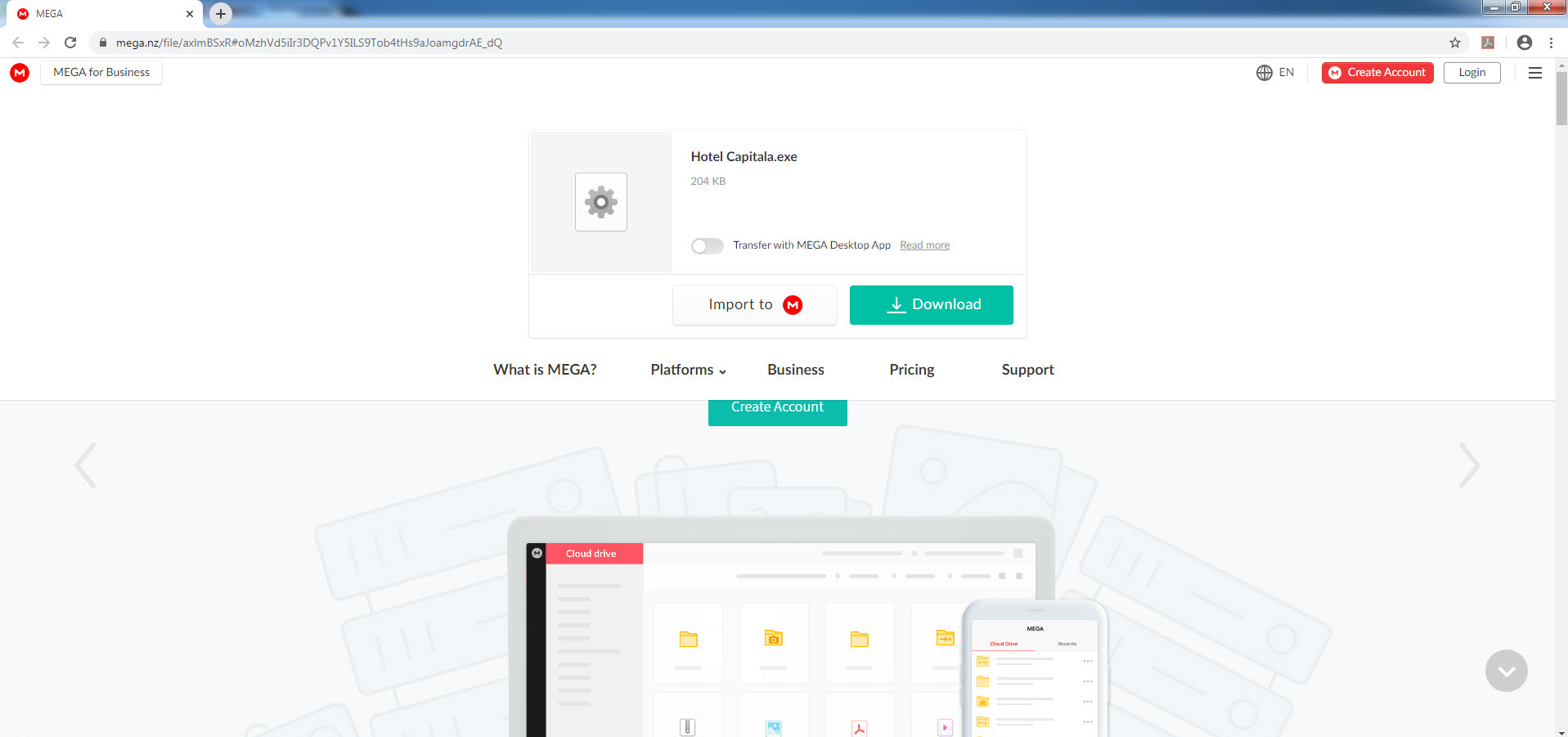
In the past, there was a threat actor, when the barbers were fleas, and the horses were jesters. This threat actor had sent an email to top-level employees of the institutions he targeted, with an HTML file attached. When this HTML file was opened, and the link address (https://go0gle-drive[.]blogspot[.]com) followed, the targeted person was directed to an address on the mega.nz file storage and sharing site (https://mega[.]nz/file/axlmBSxR). If this file was downloaded and run, the threat actor could remotely control the targeted system, making all kinds of mischief, including recording audio, video and keystrokes. According to legend, some network-based sand pool systems could not analyze the link address contained in this HTML file sent by the threat actor.
When an institution faces a scenario like the one described above, even if the attack attempt is not successful, it should still handle the matter with great care because this may be an indication of a precursor earthquake, and a sign of a bigger one to come. Therefore, it is important to investigate whether the attack was targeted (Spear Phishing), organized (APT), or just a part of a general campaign targeting a large number of users. It may not always be possible to find answers to these questions, but through analysis, an idea may be gained. In this writing, I will attempt to find answers to these questions.
Initially, through static analysis, I saw that the file was developed and packaged with C#. When I ran the file on a virtual system and analyzed it dynamically, I discovered that the malware accessed an address on the Pastebin site. When I visited this web address, I saw that the page contained an IP address (193.161.193.99) and a port.
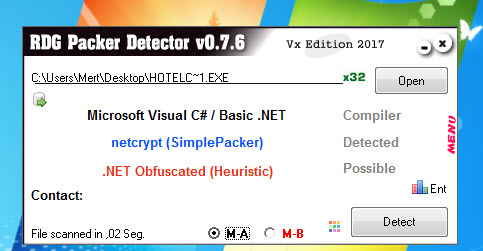
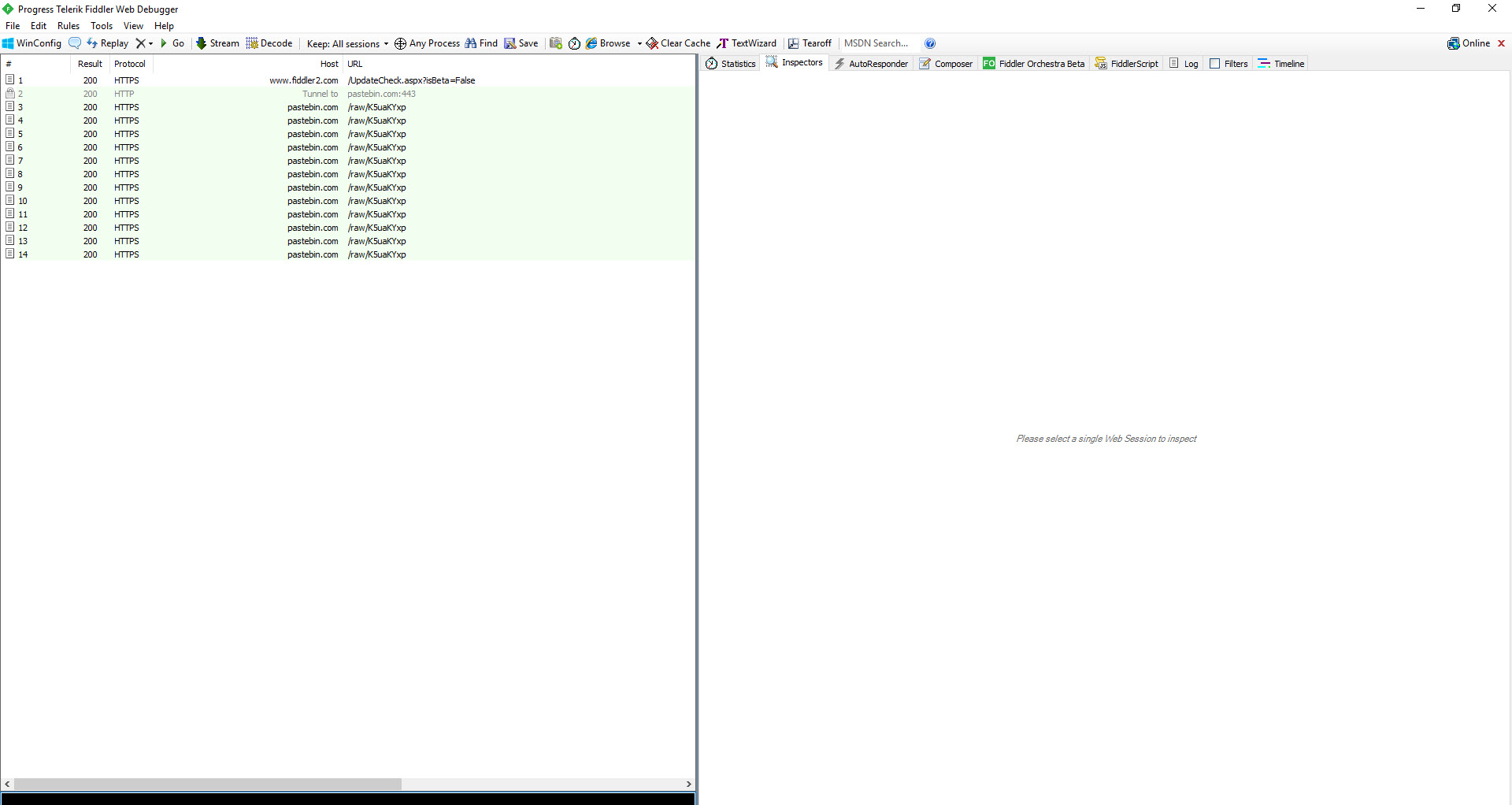
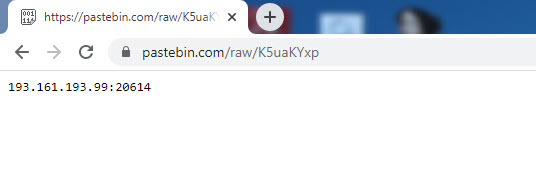
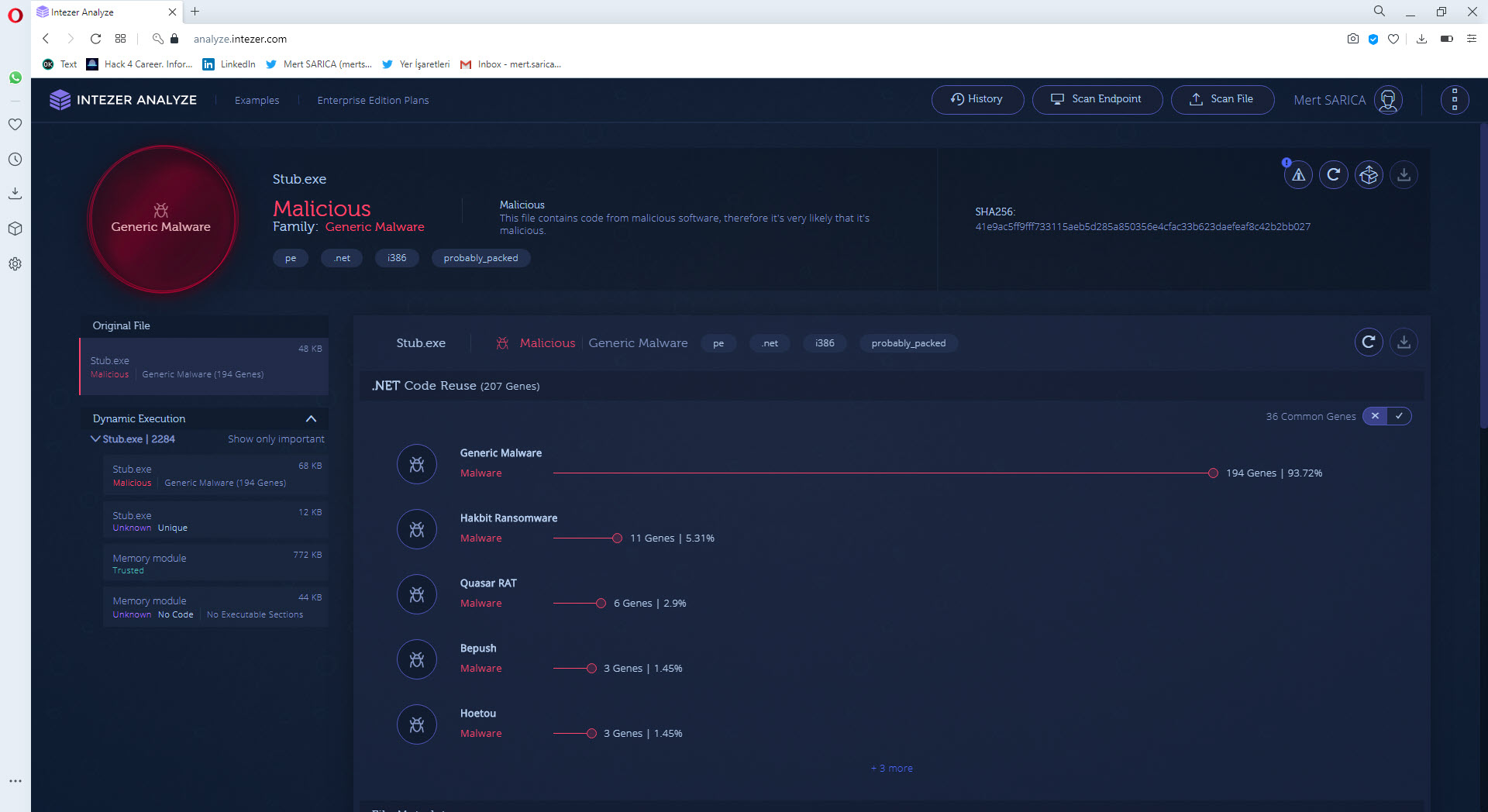
Especially in APT attacks, the malware used is often specially developed by the threat actors and compiled just before the attack, so when it is uploaded to VirusTotal, it is usually detected under a general signature name such as (Backdoor, Trojan, etc). In such cases, it may be possible to use services like Intezer to search for which other malware the code of this malware was used and make comparisons, and thus gain information about the threat actor.
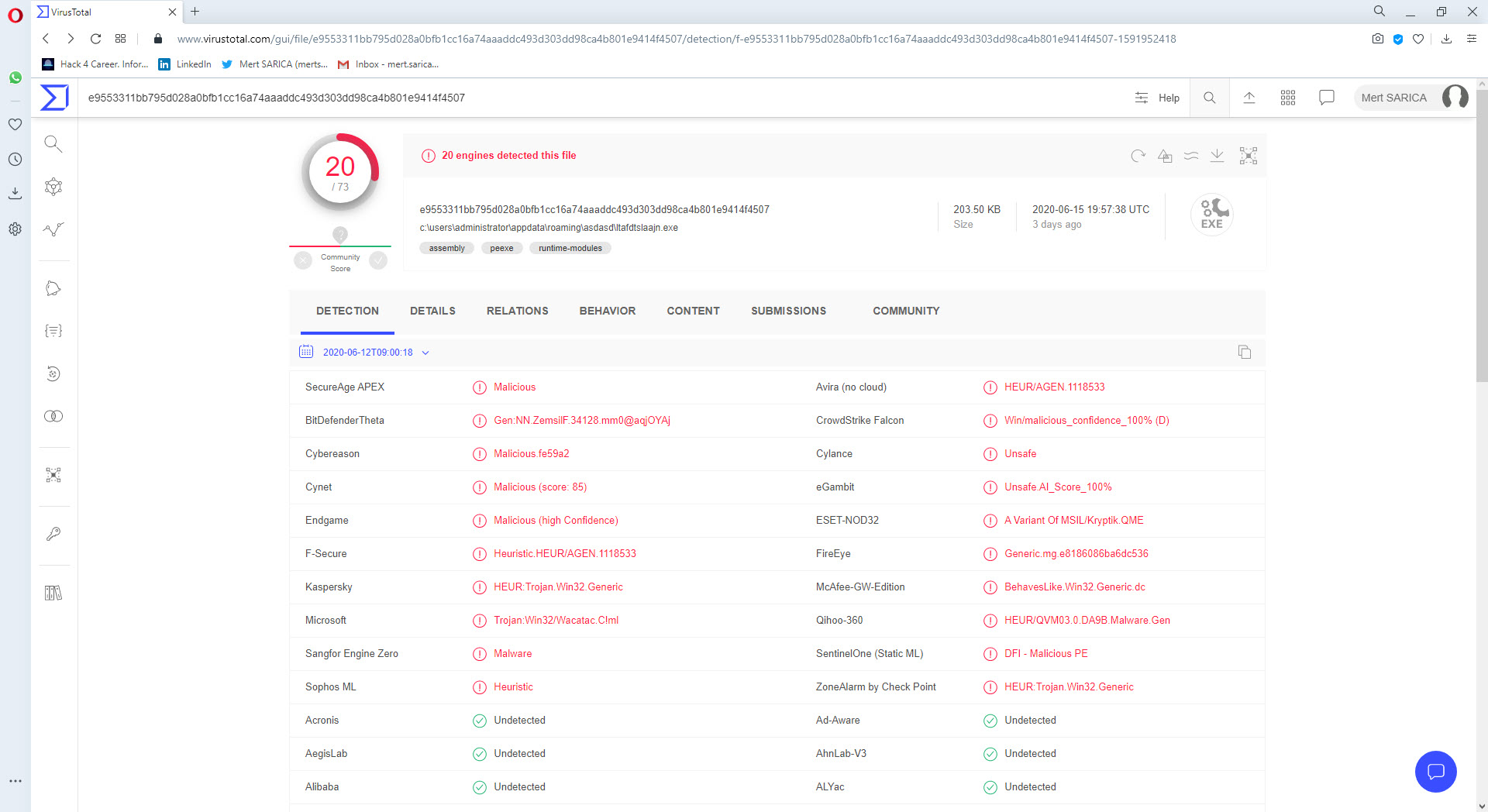
When I uploaded the malware to VirusTotal, I saw that it was not specifically matched with any other malware. When I searched on Intezer, unfortunately, I came up empty handed. (Generic Malware)
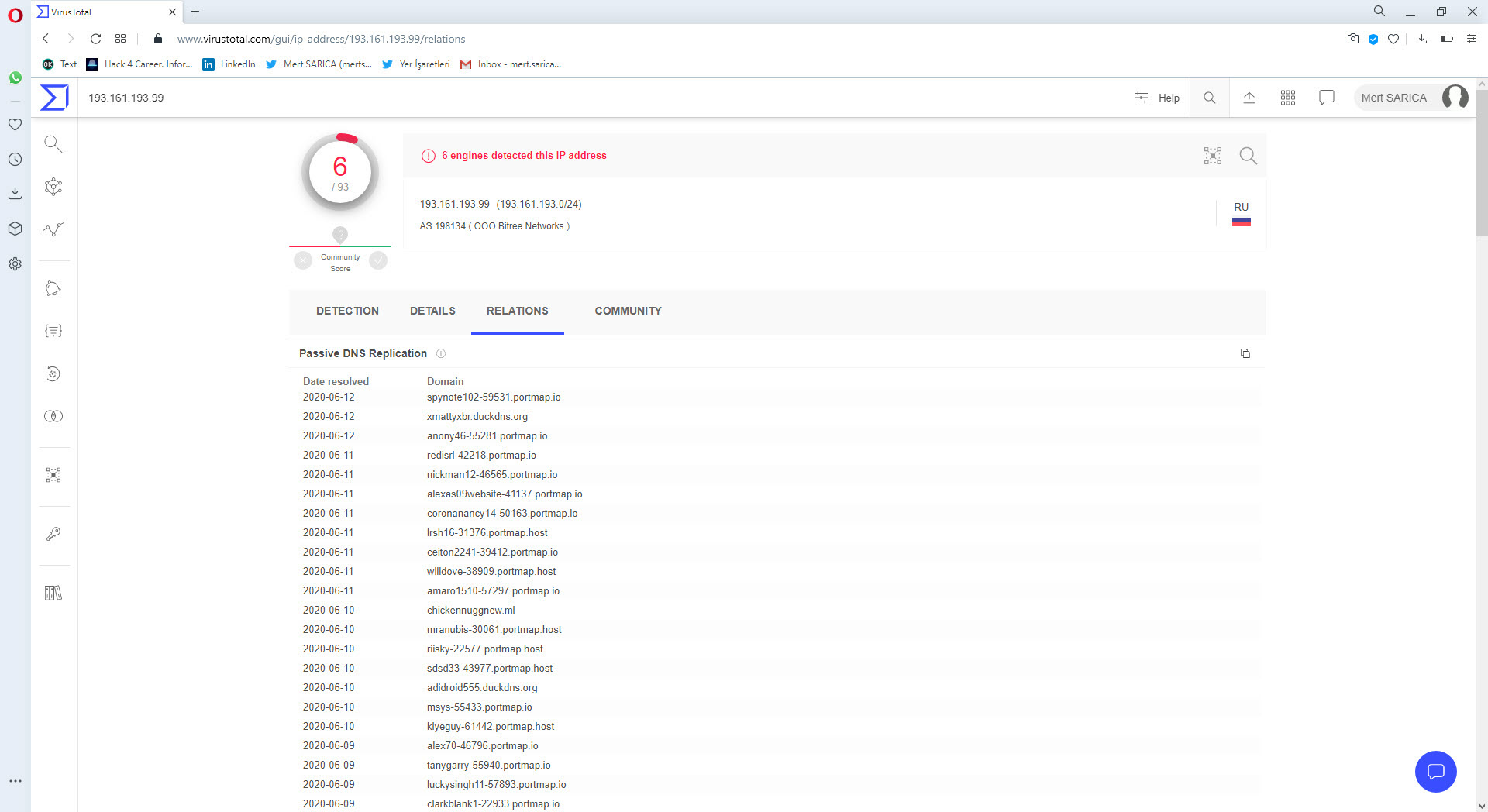
When I searched the IP address I obtained from the Pastebin.com page on VirusTotal, I found out that it belongs to the Portmap.io service which serves for redirecting ports.
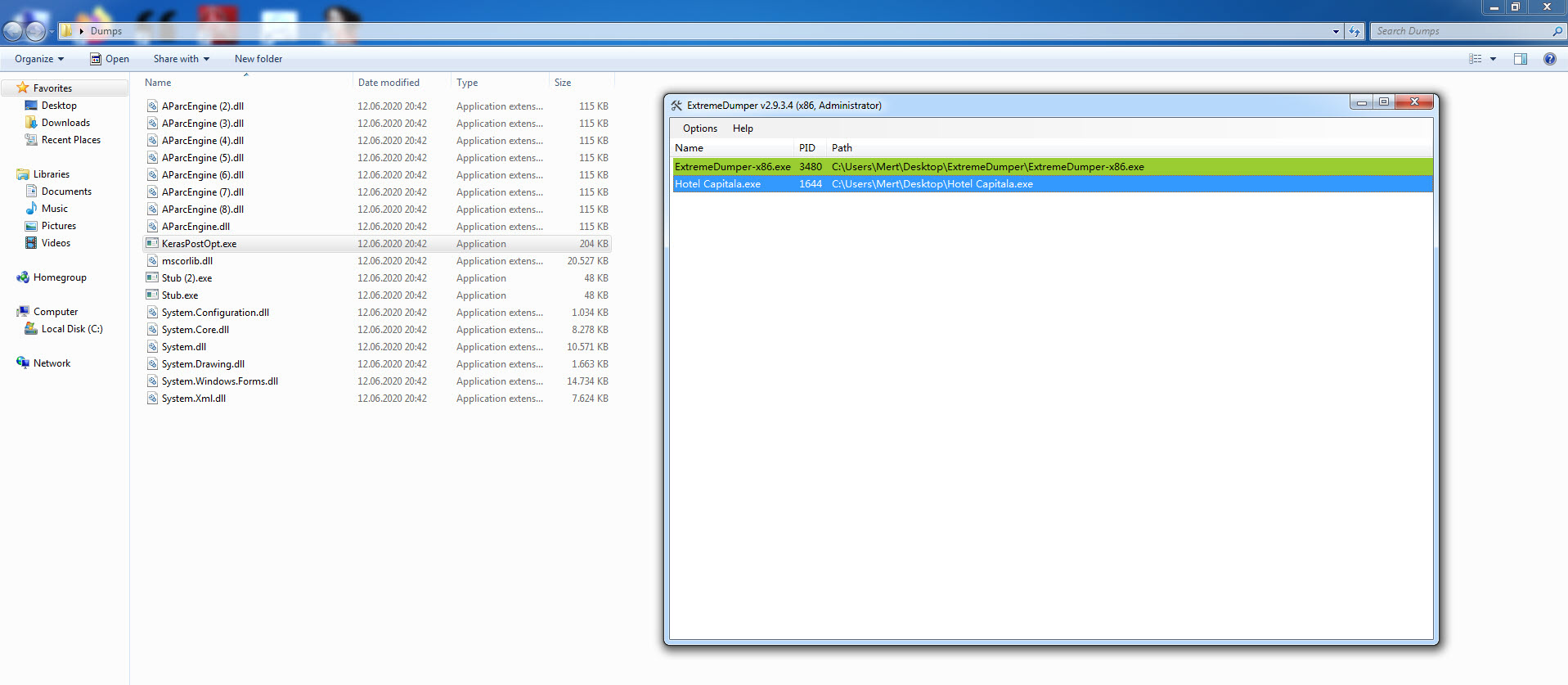
As I continued my research to find out what the malware developed by the threat actor who tries to hide himself as much as possible, I reached the stage of dynamic code analysis and the dnSpy debugger that I used in my article titled OPSEC came to my aid. Before starting debugging with dnSpy, in order to find the main module that the packaged software hides in memory, when I ran the ExtremeDumper tool, the mother of evils, Stub.exe, emerged.
As I analyzed the Stub.exe program step by step with dnSpy, at one point, I noticed that it was encrypted with AES and the decrypted value of 0.5.6B caught my attention. When I searched this value on Google with the keywords “rat 0.5.6B,” guess what came up? The open-source AsyncRAT! :)
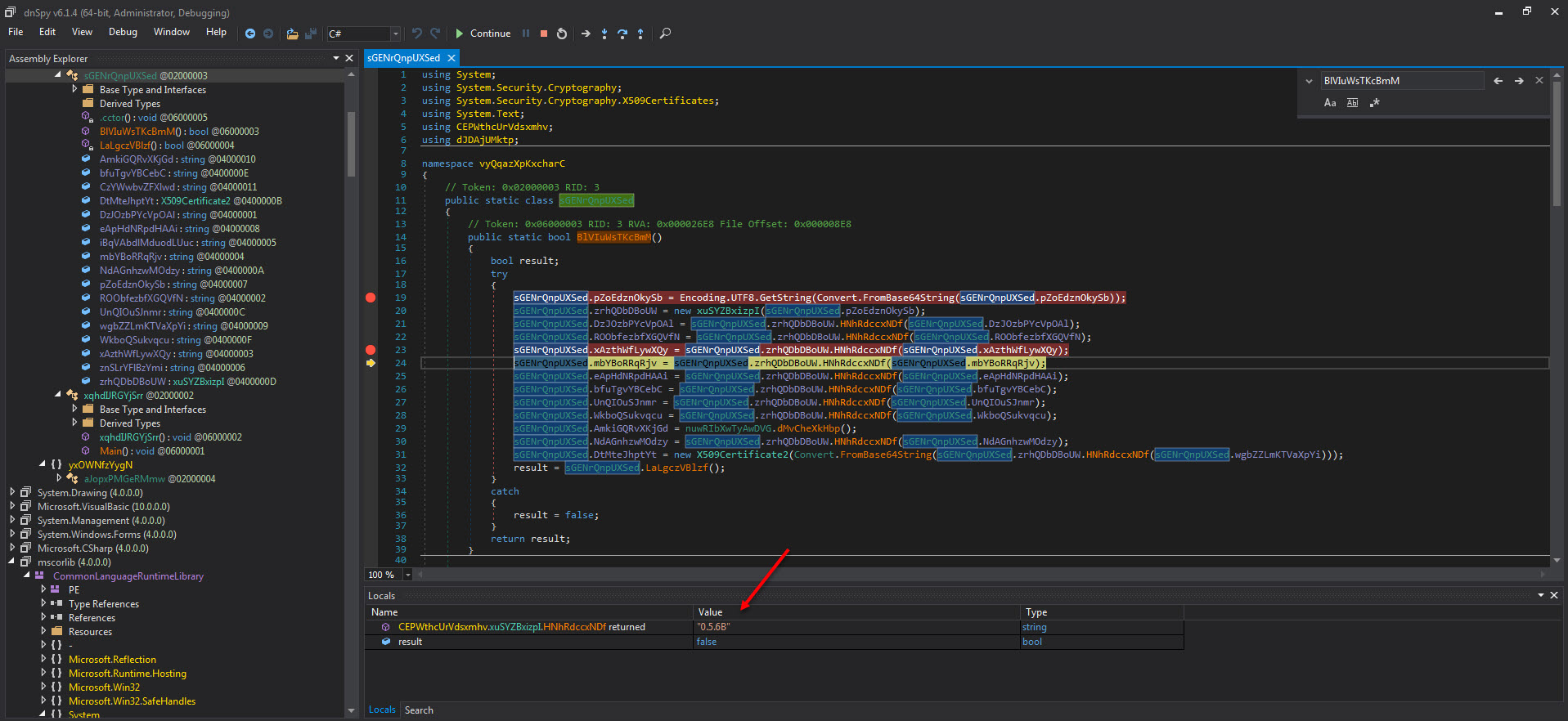
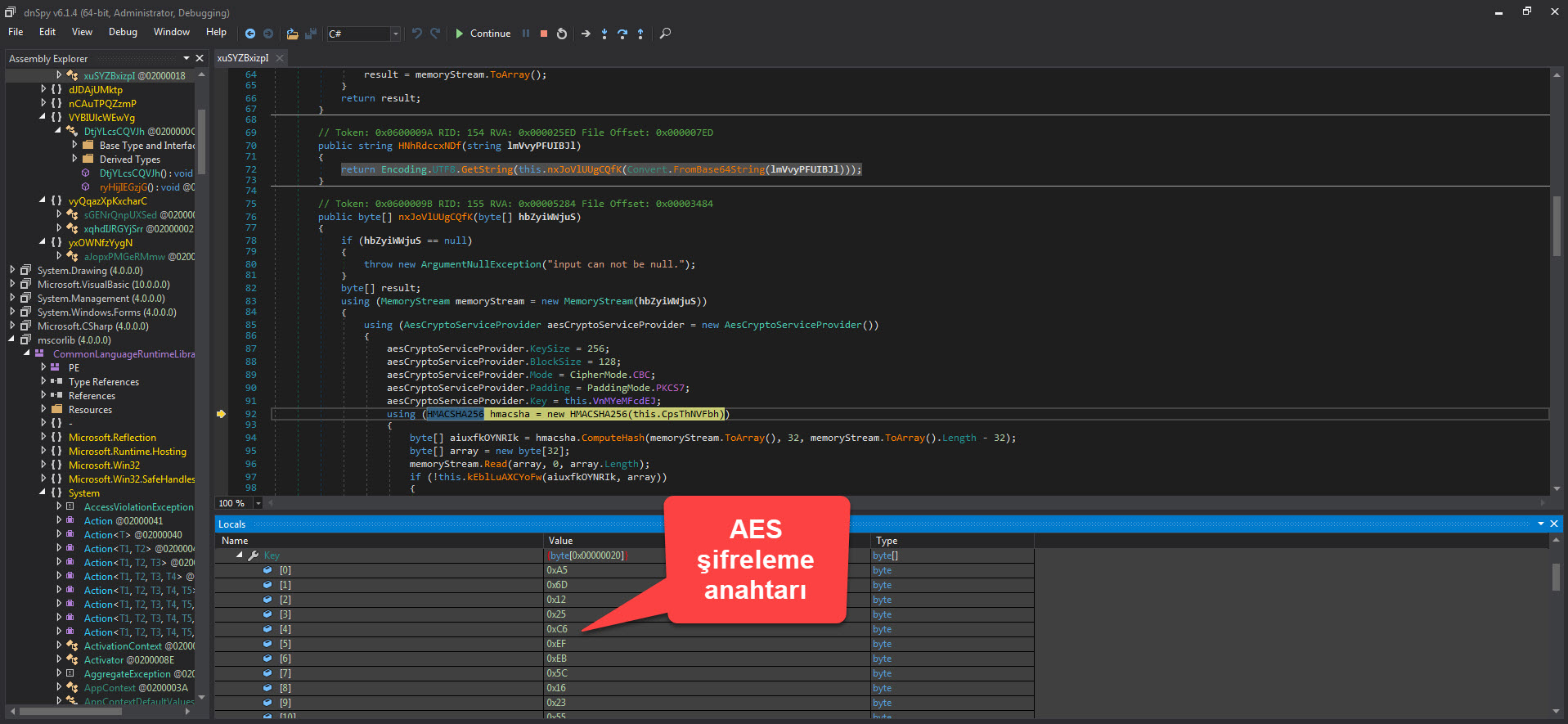
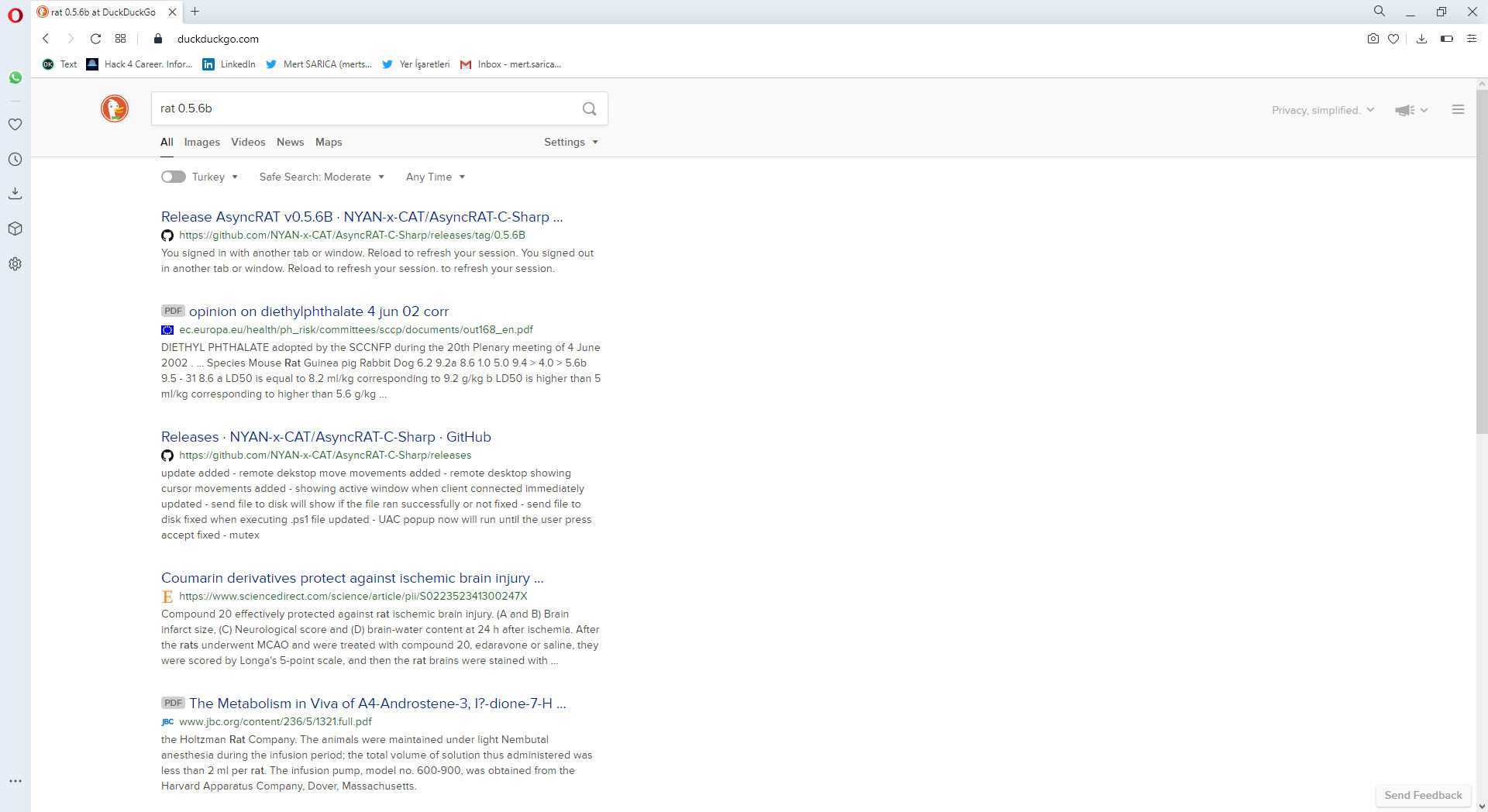
After examining this project in detail on GitHub, I was able to confirm that the malware I analyzed is AsyncRAT by inferring it from similar code blocks.
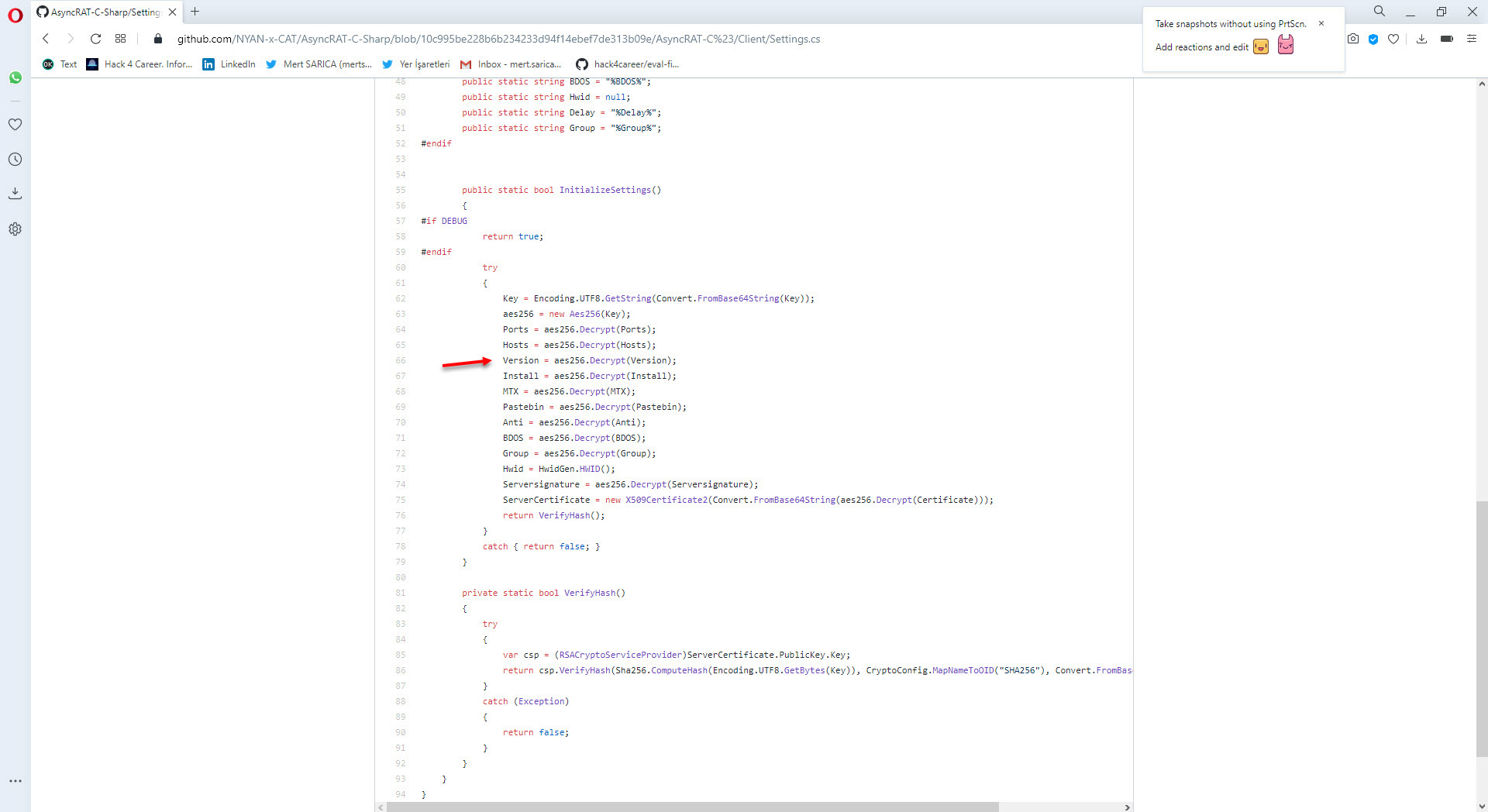
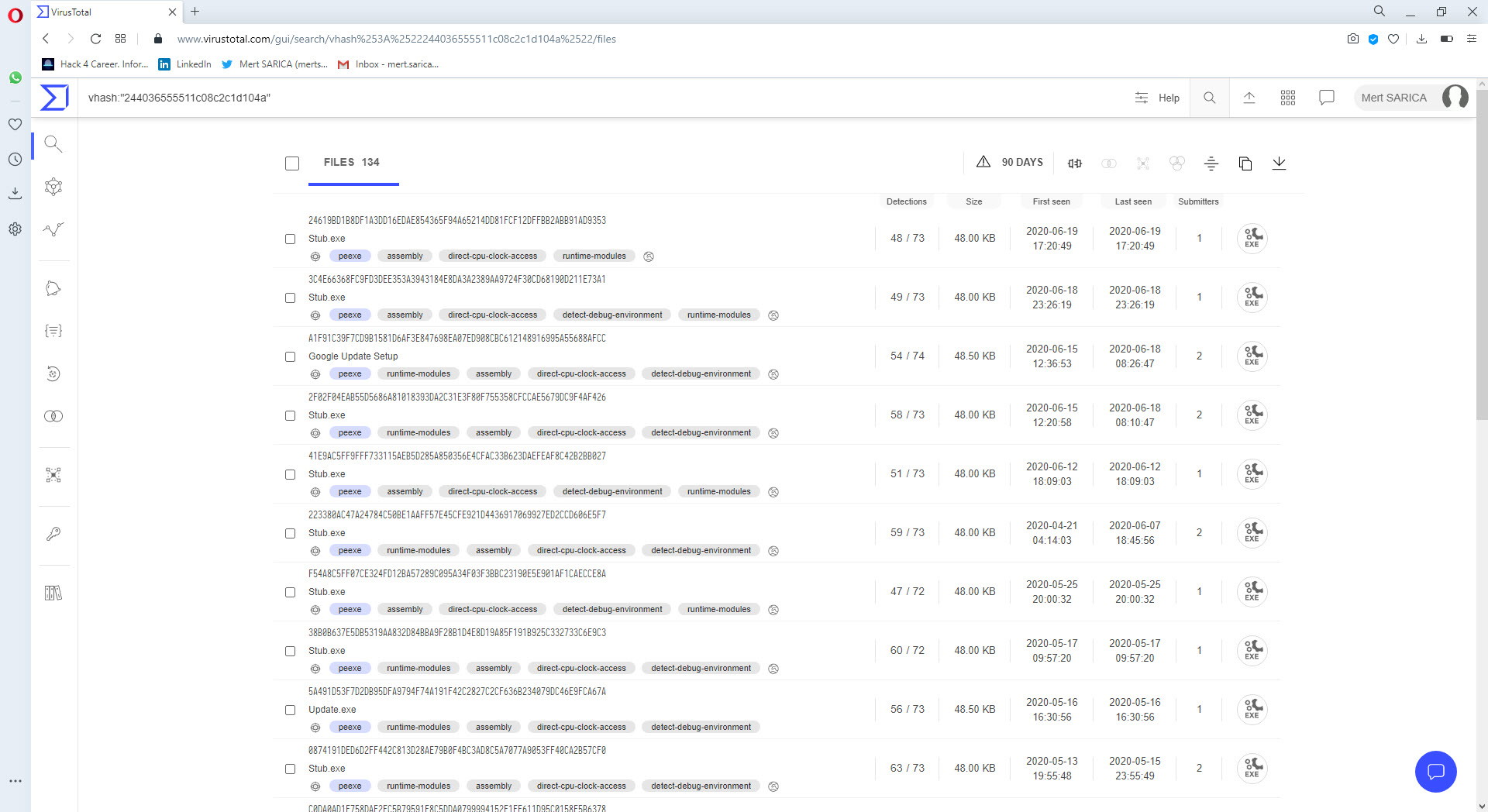
Finally, when I searched for similar Stub.exe files with vhash on VirusTotal, I encountered many examples. As I wondered whether all these examples had the Pastebin address from the malware I analyzed, or were part of a common campaign, either I would have to examine the analysis report of each of more than 50 examples or find a very short and practical way which is suitable for lazy people. :) After starting to think in a cunning way, the idea of preparing a tool in Python that analyzes all these examples statically, first finds the AES encryption key and then extracts the configuration information came to my mind.
Of course, since the variable names are randomly generated in each program, I had to first find the AES key by using a static variable. Since we know that programs developed with .Net are compiled into bytecode (CIL/MSIL), I started to search for static values on bytecode.
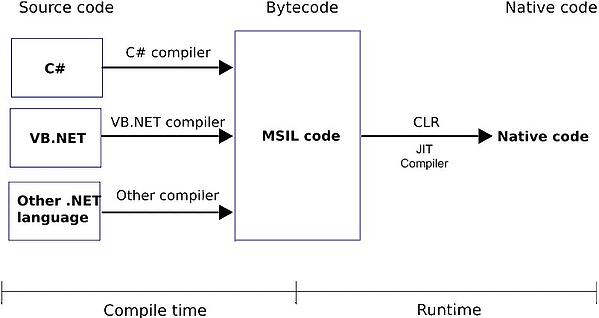
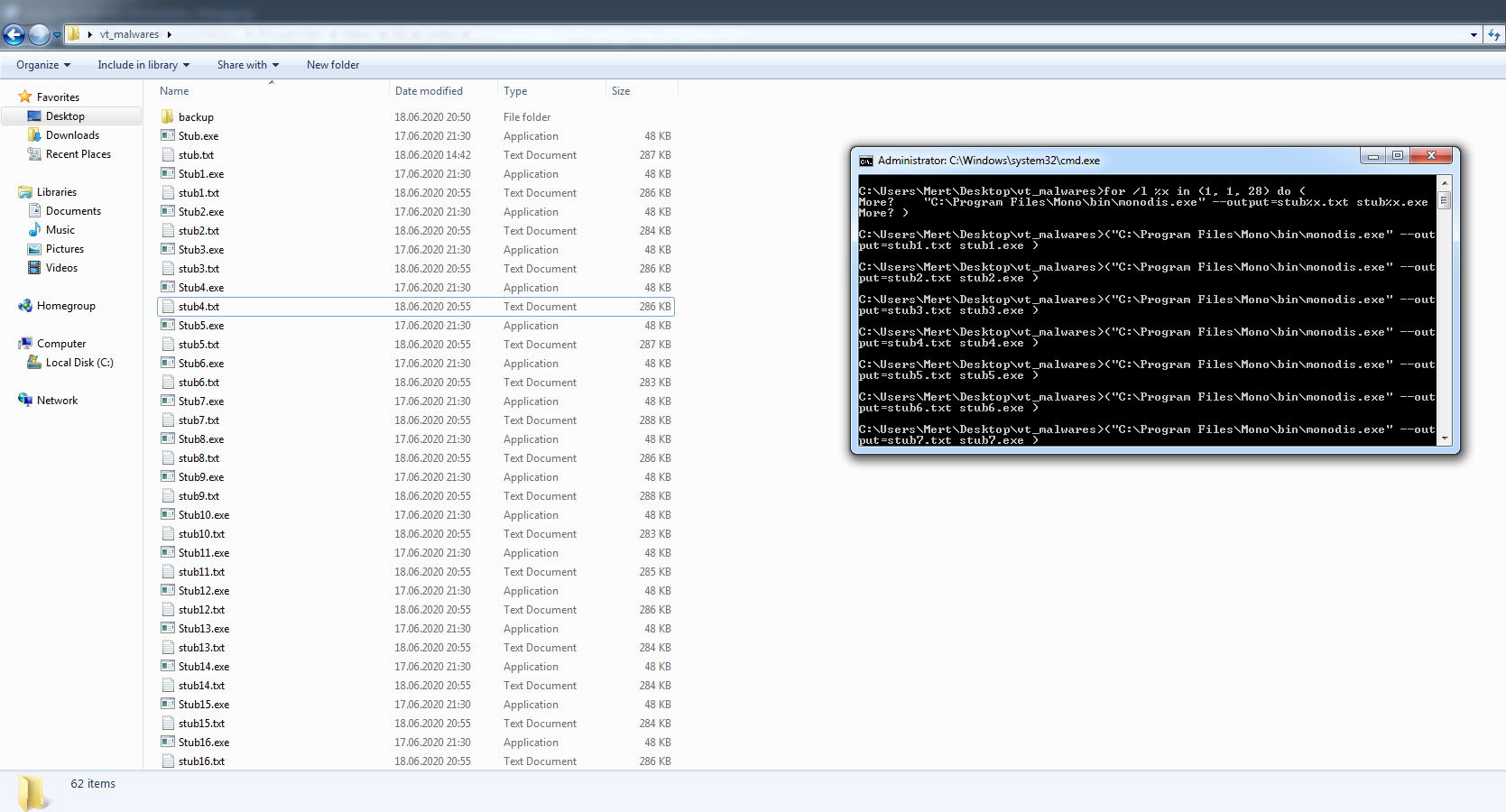
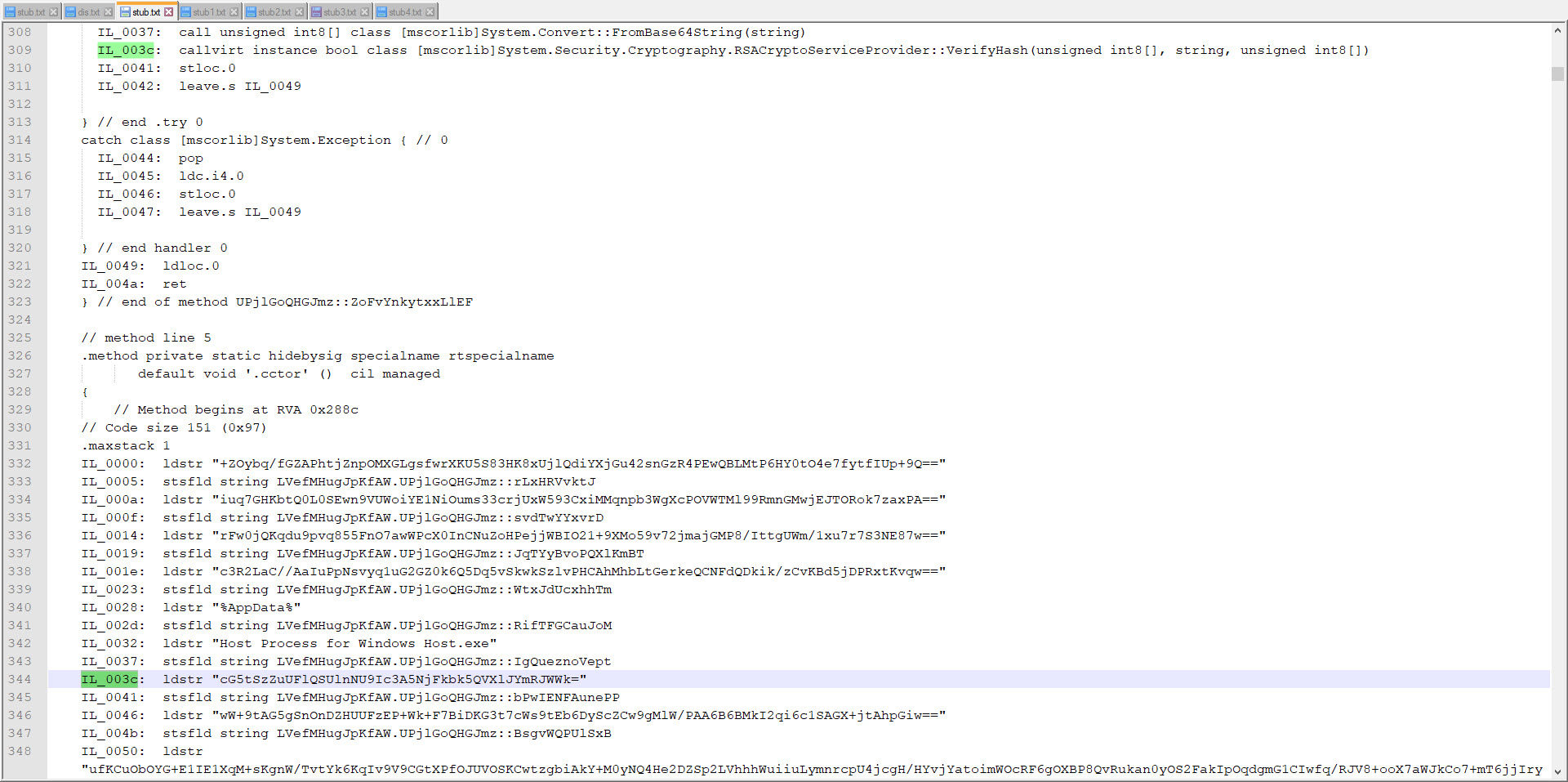
For this, I decided to take advantage of the Mono Disassembler (monodis) tool, which is part of the famous Mono project. Using the monodis tool, I converted all Stub.exe examples to code, and I found out that the AES encryption key is always after the 0x288c value, and the IL_003c value. And using this information, I developed the AsyncRAT Configuration Extractor tool in Python. When I run the tool on all examples, I found that the information in the configuration of each one of them was different from the malware I analyzed, so I learned that the malware I analyzed was not a part of a common campaign.
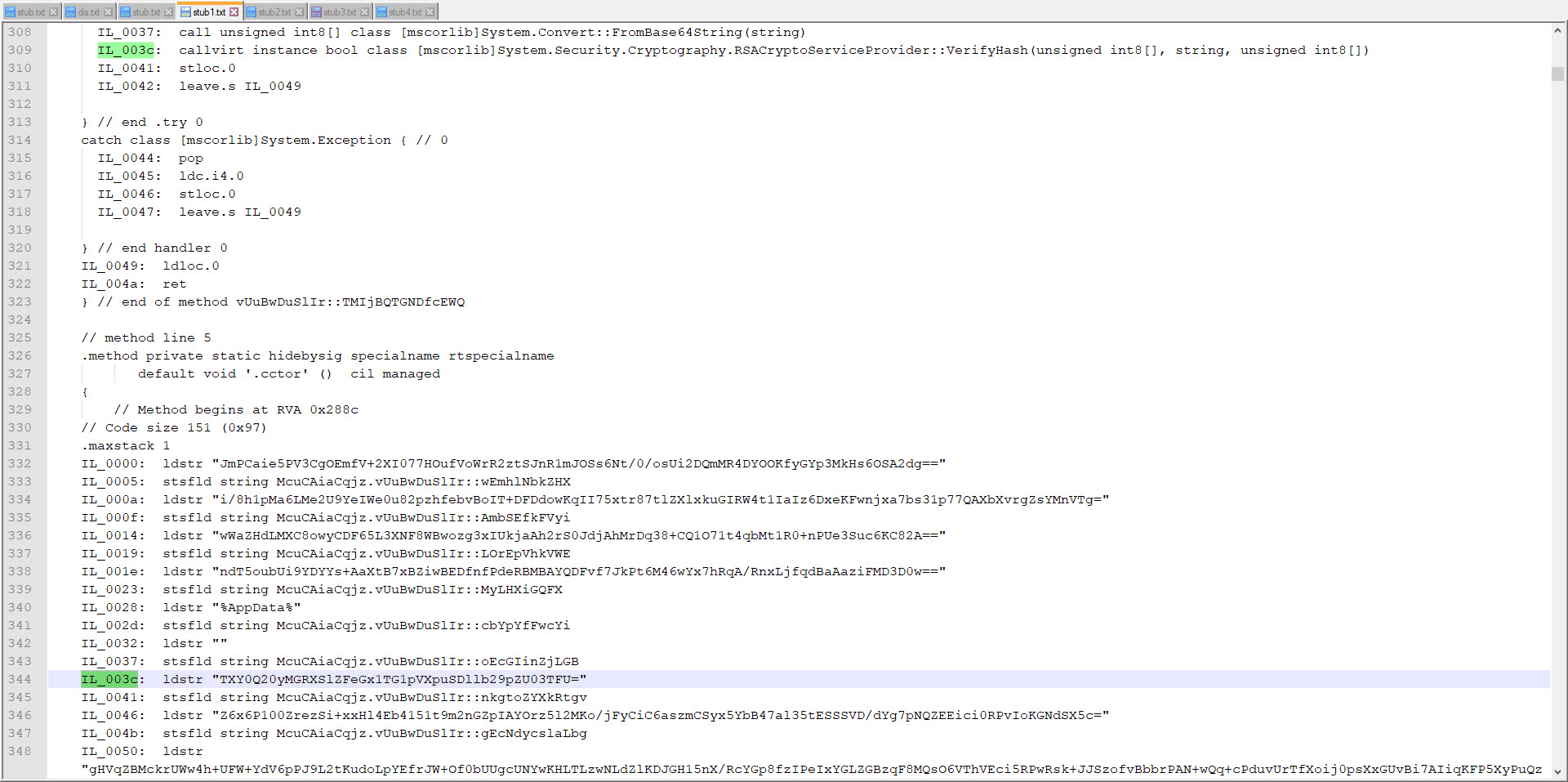
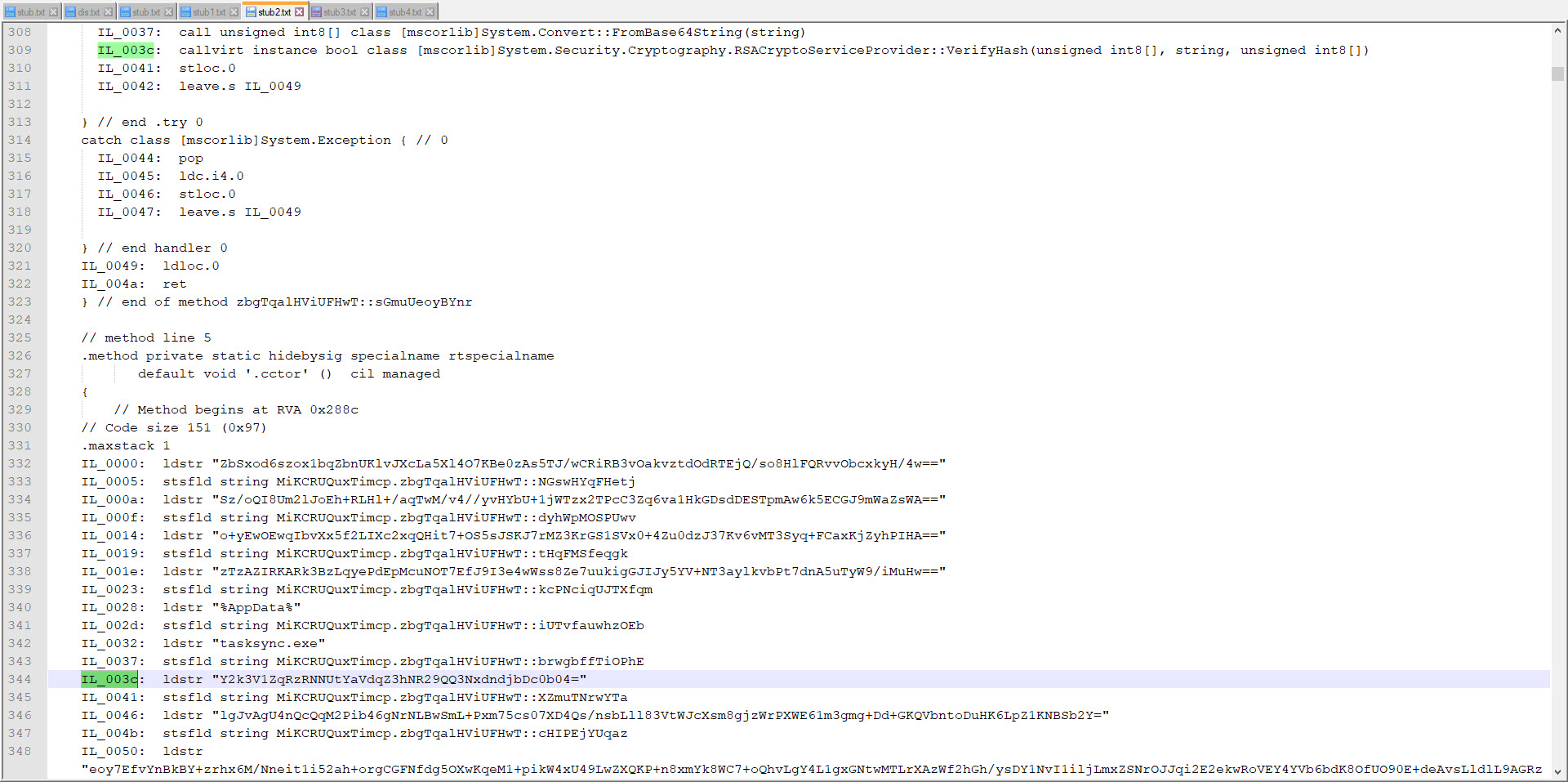
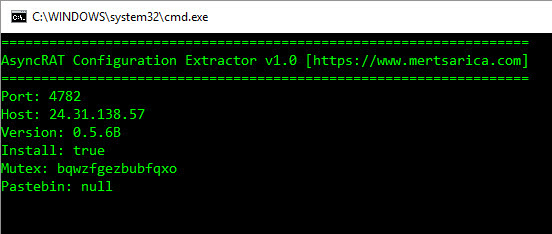
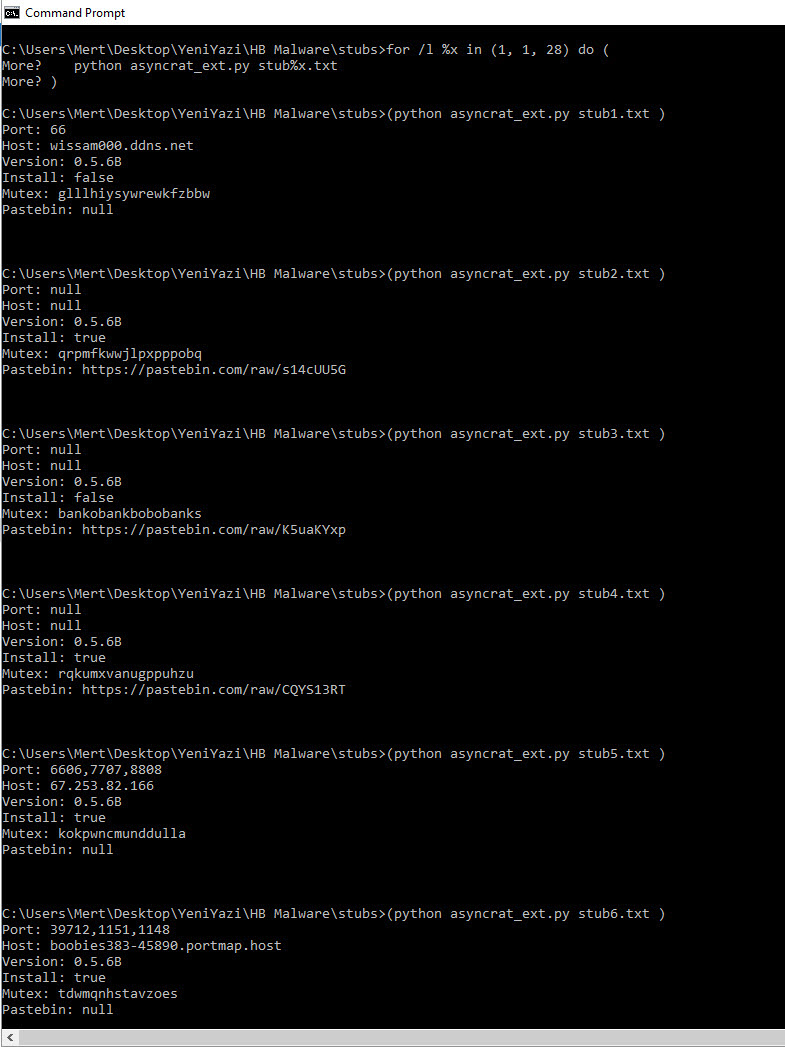
In conclusion, after compiling and collecting all this information, it appears that while this cyber attack attempt is not an APT attack, it is part of a targeted attack (Spear Phishing). Especially in light of the increase in such targeted cyber attack attempts after the Covid-19 pandemic, I recommend that organizations and employees be very careful.
Hope to see you in the following articles.