Stolen Credit Card Hunt
As a cybersecurity researcher who uses social media very effectively, you know that I have turned messages I have received through social networks and emails into security research, and then into articles and presentations. In this story, which has the same starting point as others, you can see how I benefited from a cyber threat intelligence received through a social network for the purpose of ensuring customer security.
As usual, on the morning of July 17, 2020, as soon as I woke up, I picked up my phone and started looking at my social media accounts to check cyber security news. A message from a person named Ebubekir BASTAMA on LinkedIn caught my attention, in which he tagged me in addition to banks. The message contained a video showing credit card information in plain sight and asked if they were canceled for customer security.
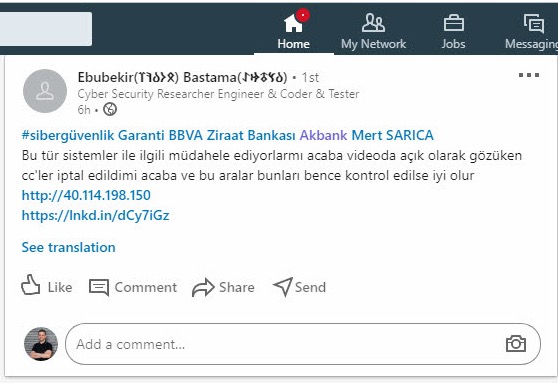
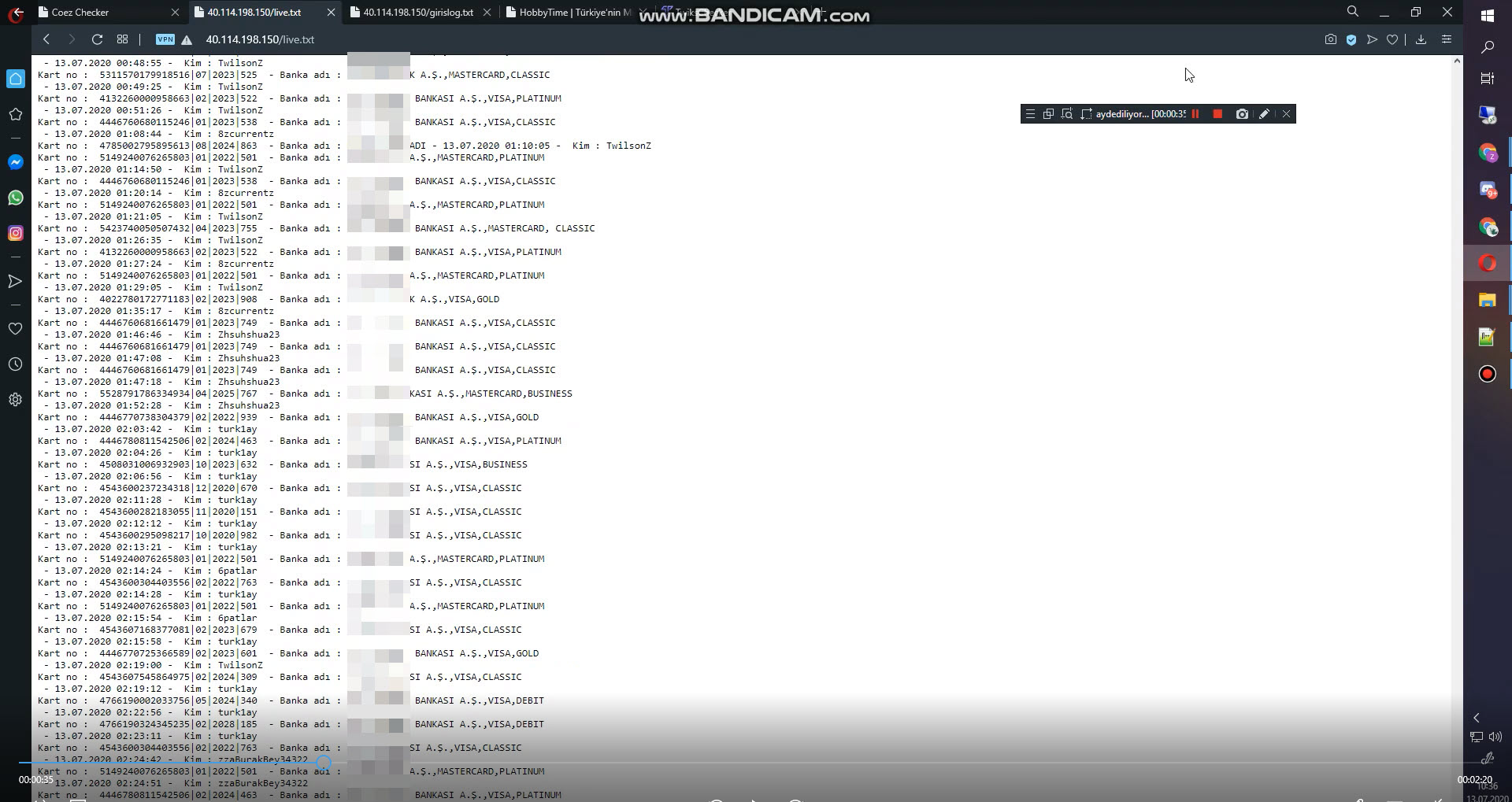
As I started watching the video, it seemed that a service called Coez Checker, which is used to check stolen cards, was hacked by scammers to message other scammers. The scammer showed the stolen card information registered on the system on July 13 for about 30 seconds of the approximately 3-minute video, and then ended the video recording after sending his message to other scammers. When I tried to access the address http://40[.]114.198.150/live.txt, where the stolen card information seen in the video is located, as I expected, the file had already been removed from the broadcast and I was left with only this video.
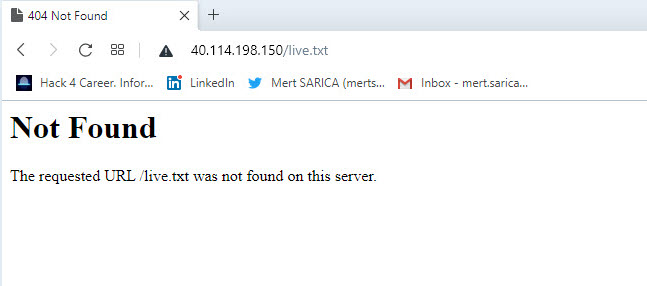
Thinking about how I could share the card information in this video with banks, including Banking Regulation and Supervision Agency (BRSA), in order to prevent citizens from being victimized by scammers, I decided to split the video file into frames, and then analyze the image files with OCR, as I did in my blog post titled “Sponsored Scamming”, to reveal the card information. I remembered doing a similar study for the blog post titled “X Financial Institution – Animated Captcha (GIF)” in 2009.
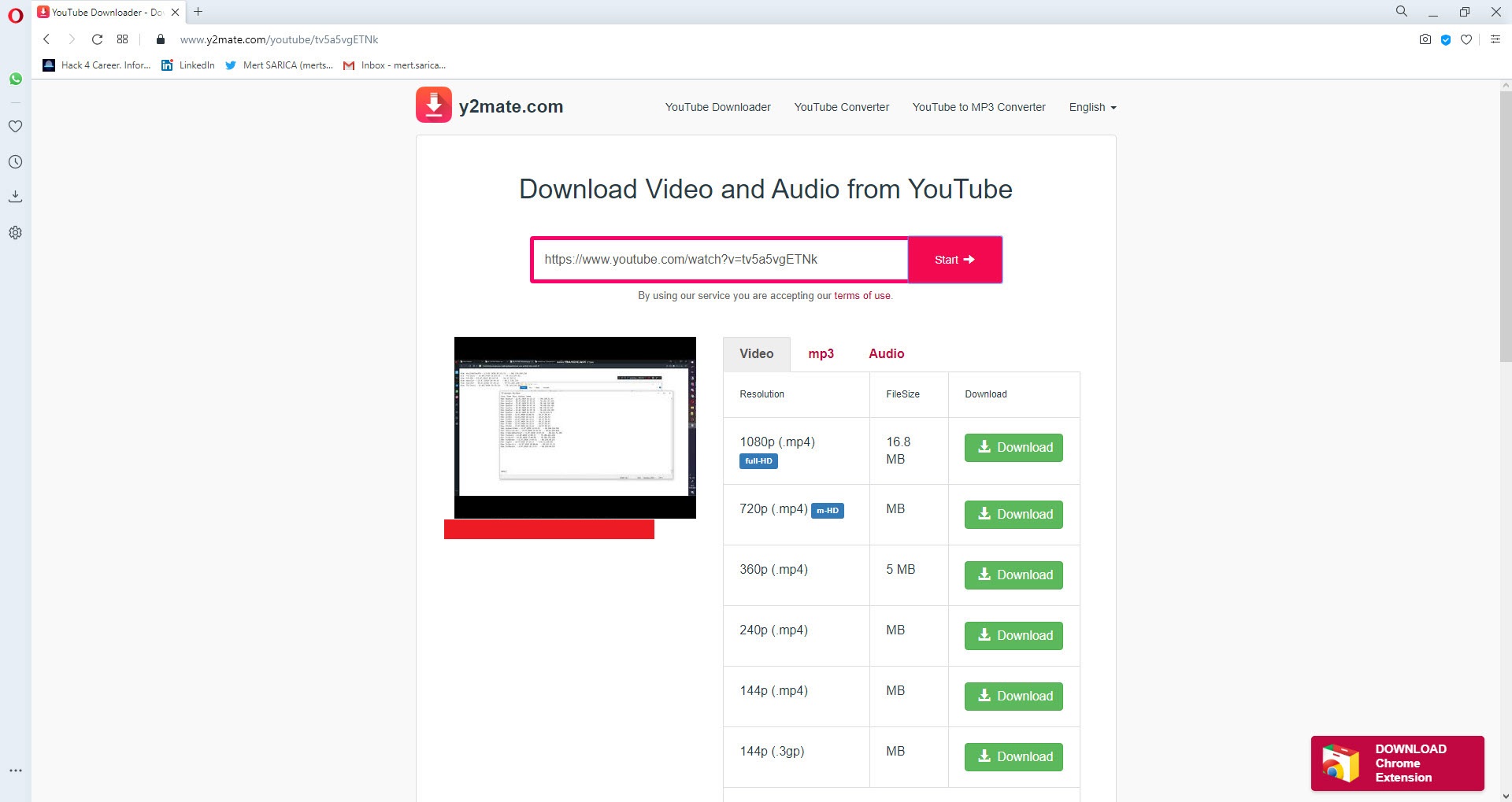
First, I used the Y2mate YouTube Downloader website to download the relevant video file from YouTube.
I developed and downloaded a tool called Cam2Jpg that splits the specified video file into frames and saves them in JPEG format, and when I ran it on the downloaded video file, it produced more than 5000 image files.
This time, using Python and the Python-tesseract project, I developed another tool called Jpg2Ocr (I decided not to publish the tool to prevent it from being misused) that analyzes the image files and detects credit card numbers. When I ran this tool on the image files, it produced more than 1000 credit card numbers in a short time.
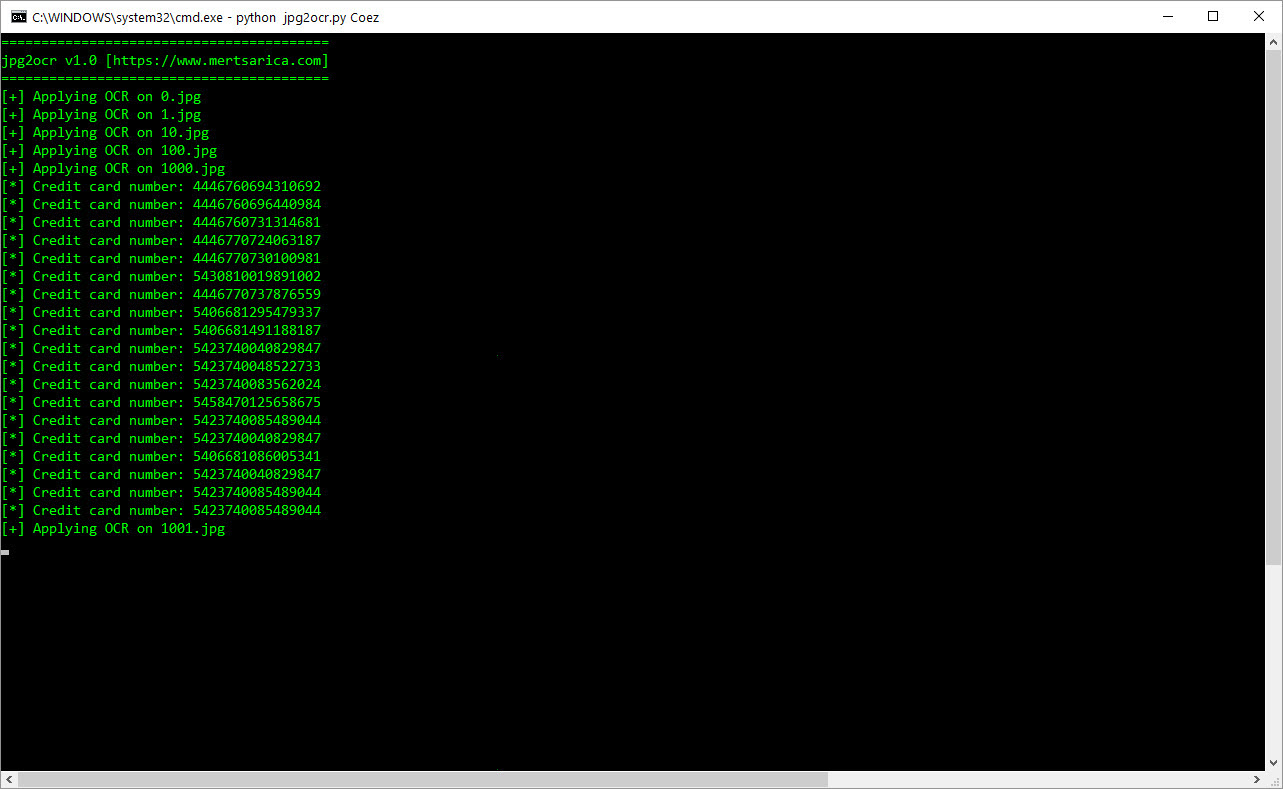
Feeling a sense of responsibility and happiness for preventing more of our citizens from being victimized by sharing all of the credit card information I obtained with the authorities on the same day, I completed another security research.
It is always useful to closely monitor social networks on your own, even if you benefit from one or more cyber threat intelligence services, in case the intelligence does not arrive or arrives late.
Hope to see you in the following articles.