About a year ago, when I was planning my Hacker Hunt with a Deception System project, I was faced with the dilemma of whether to use a low-interaction or high-interaction honeypot system. When looking at the fundamental difference between them, we can say that a low-interaction honeypot, which simulates a real system or service, is relatively easier to set up, manage, and secure. On the other hand, a high-interaction honeypot involves a real, live system, making its installation, management, and security more challenging due to isolation.
From a management perspective, the use of low-interaction honeypot systems may sound more practical. However, the main purpose of using honeypots is to attract and learn about the tactics, techniques, and procedures (TTP) used by cyber attackers. In practice, it can be much more difficult for attackers to detect high-interaction honeypots. When I observed the behaviors of numerous cyber attackers who attempted to hack my honeypot system for six months, most of them did not perform specific checks to determine if the system was a trap. Therefore, you may not need to exert much effort to harden high-interaction local honeypot systems.
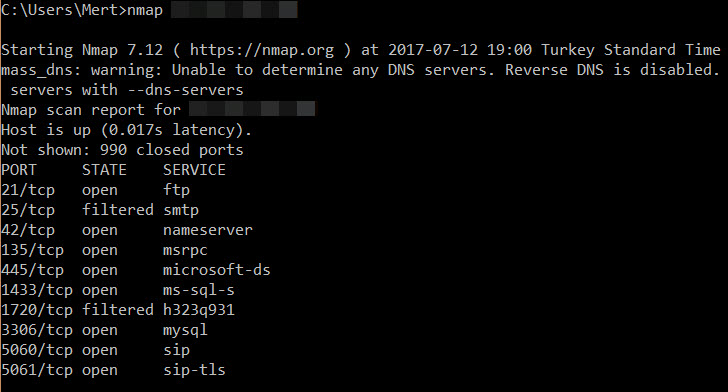
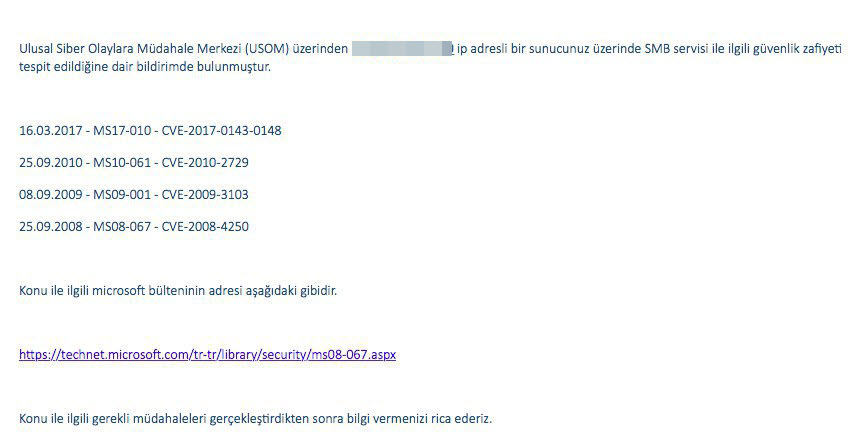
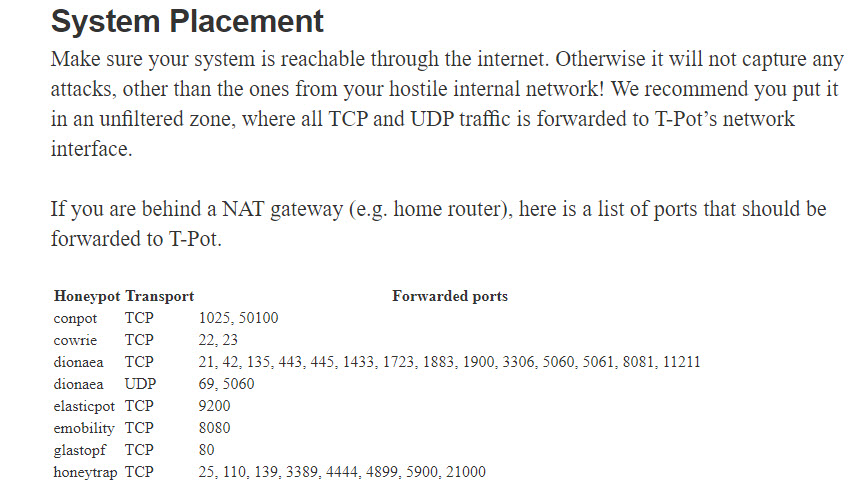
Indeed, when it comes to detecting low-interaction honeypot systems, attackers can often perform a simple scan using tools like Nmap. This is why it is crucial for individuals and organizations that use honeypots to make them appear undetectable before placing them alongside live systems. In some cases, even before cyber attackers, the National Cybersecurity Intervention Center (USOM) may contact the internet service provider regarding this system, citing its vulnerability. :)
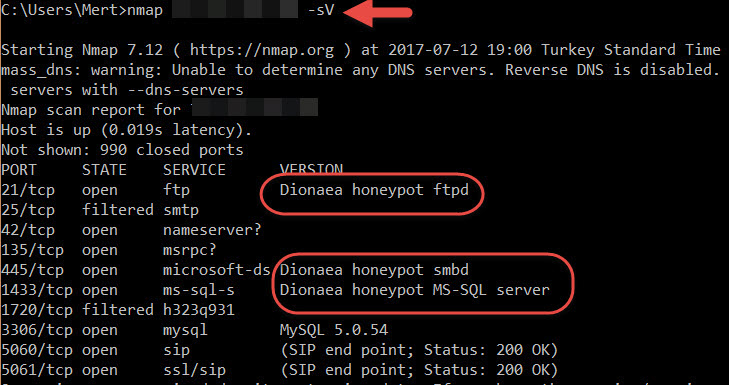
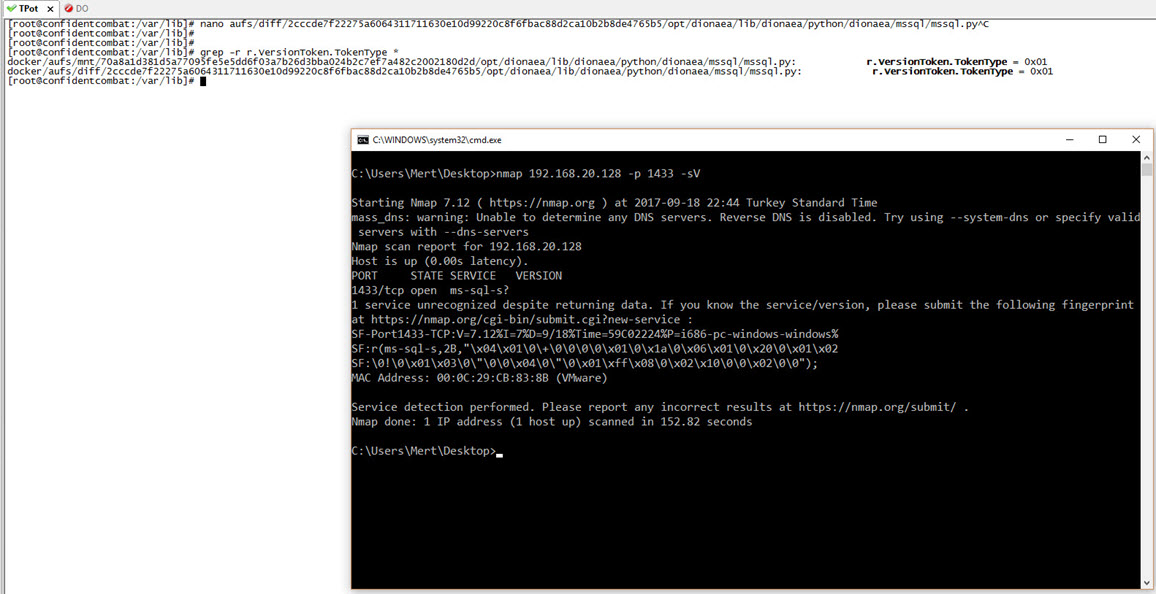
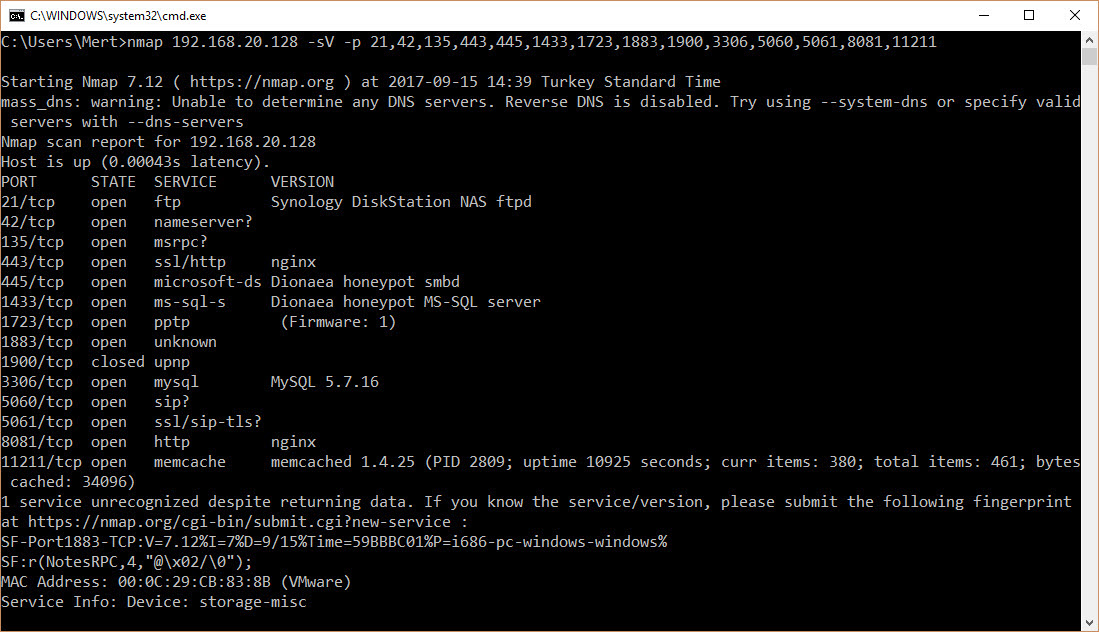
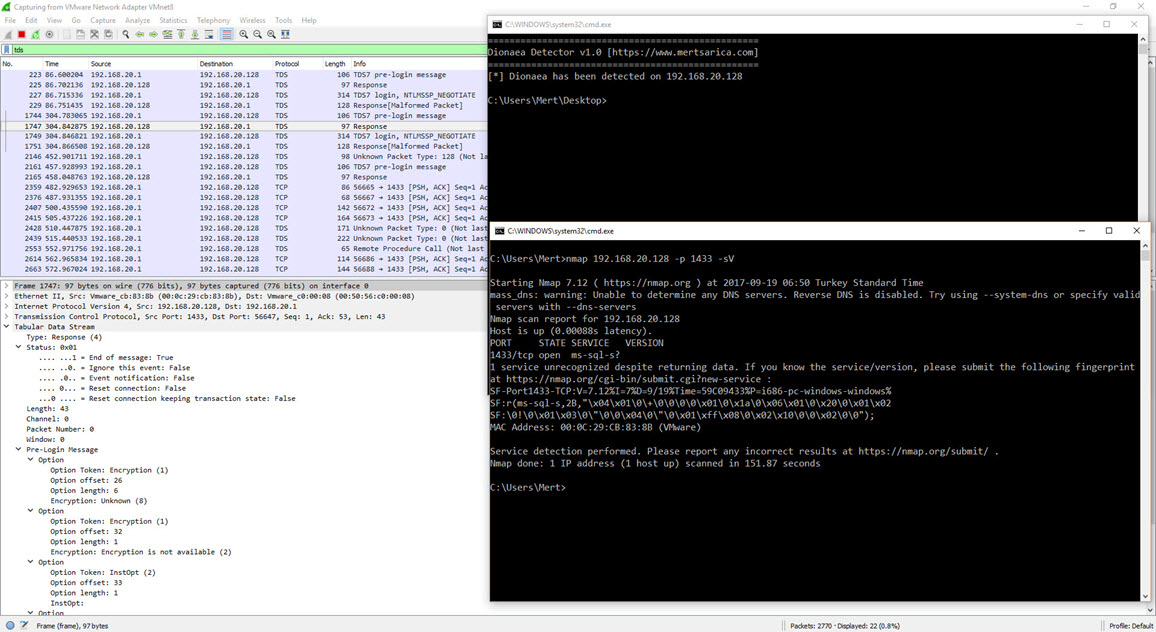
When it comes to honeypot systems, many people think of Dionaea. As seen in the screenshot above, Dionaea can be easily detected by Nmap when installed with the default settings. However, a quick search on the internet reveals numerous resources (#1, #2, #3) on how to make Dionaea appear undetectable. For example, by changing the “r.VersionToken.TokenType” parameter in the “/dionaea/mssql/mssql.py” file from 0x00 to 0x01, which simulates the MSSQL service, Nmap can no longer detect Dionaea running on port 1433. Since Dionaea simulates vulnerable services (low interaction), making it appear undetectable based on the information found in these resources can make it quite easy to identify Dionaea from the perspective of a cyber attacker. This sparked my interest in researching how easy it actually is to detect an “undetectable” Dionaea.
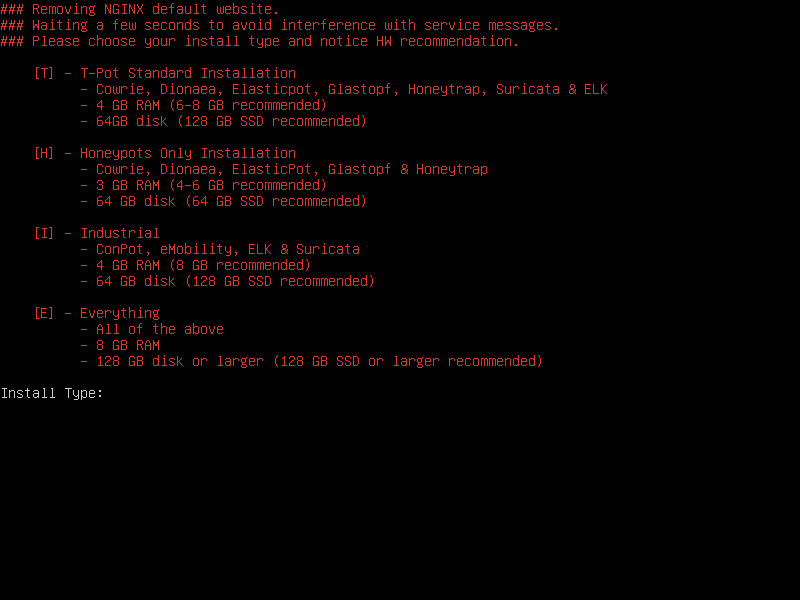
To avoid the hassle of setting up Dionaea, I opted to install T-Pot, a honeypot virtual system developed by Deutsche Telekom that includes numerous honeypot systems, including Dionaea. Considering that a small honeypot system like Dionaea may not fully simulate the MSSQL service (TDS protocol), I decided to start with port 1433.
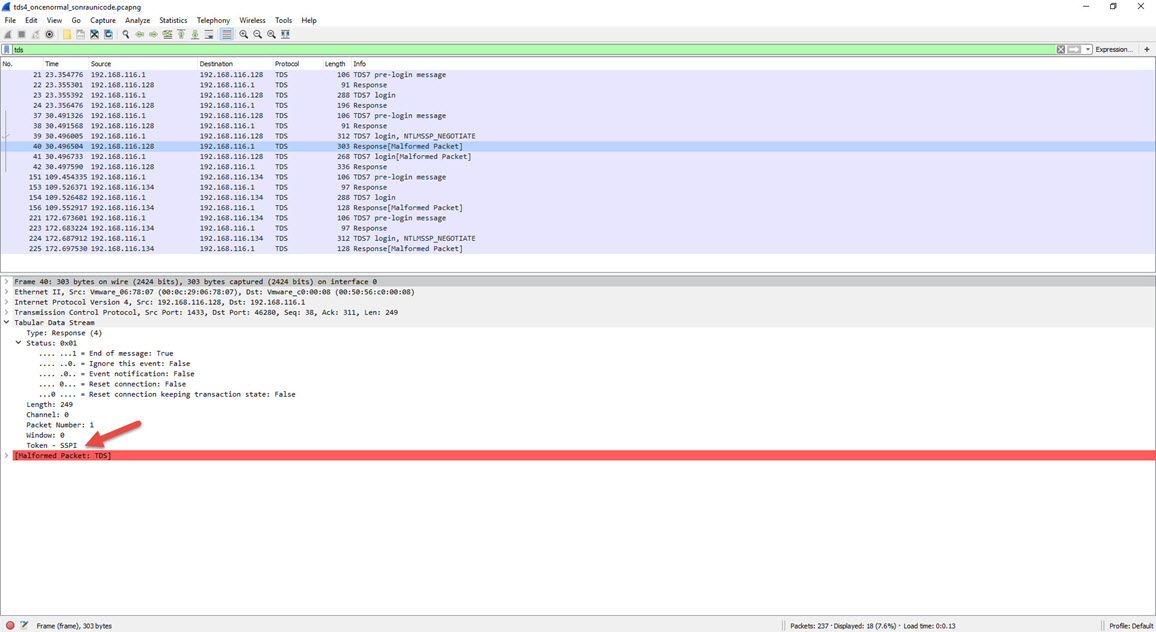
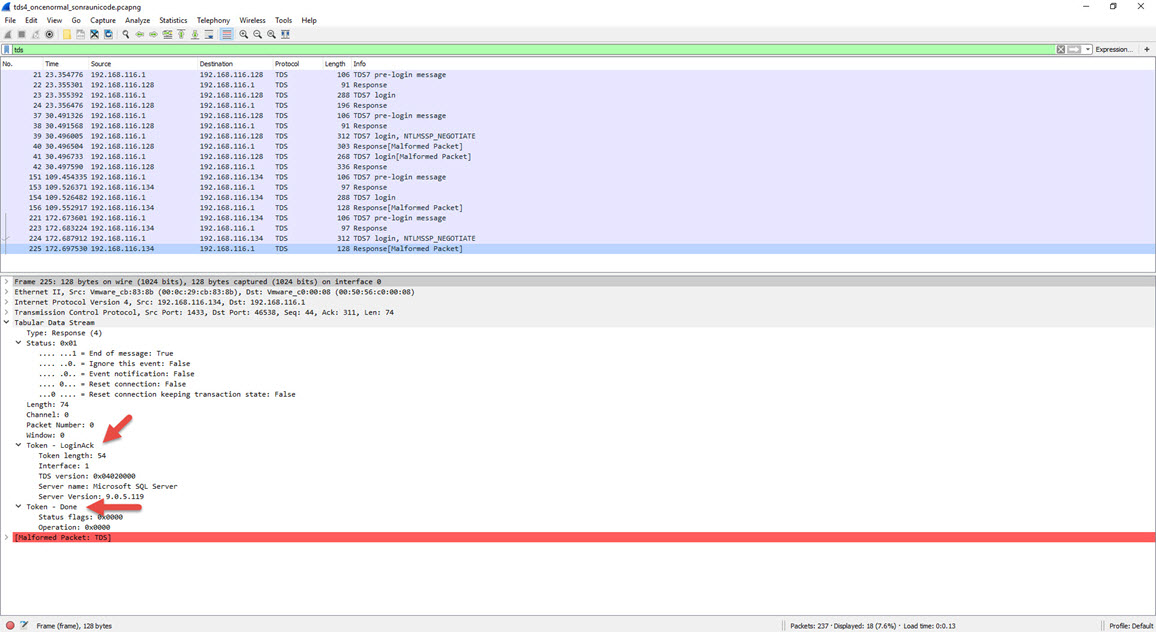
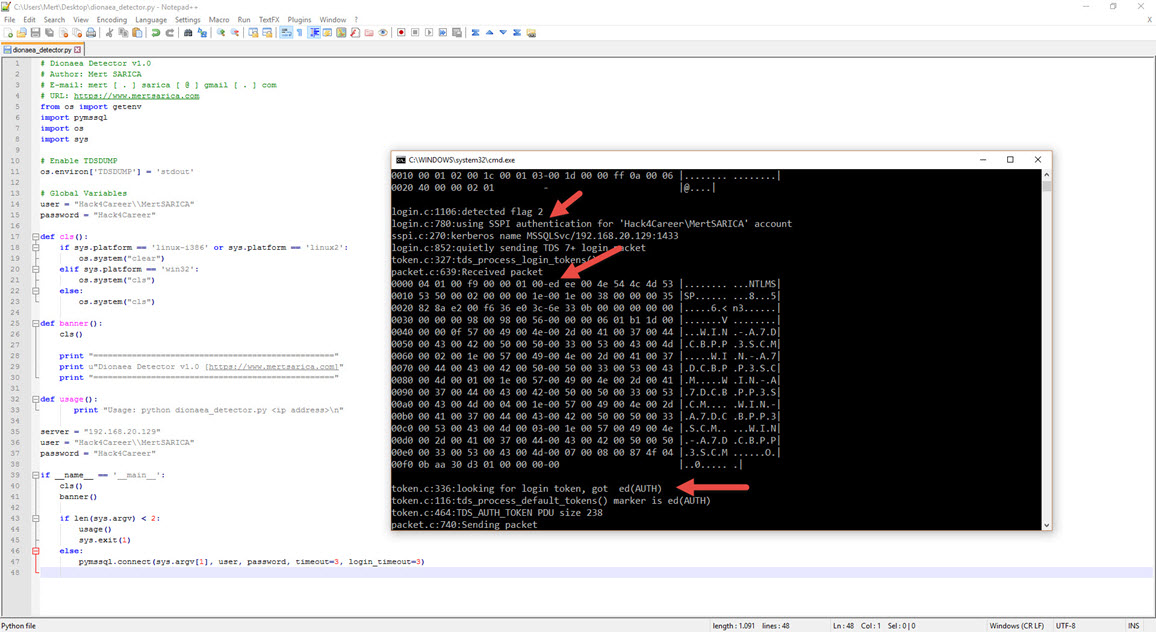
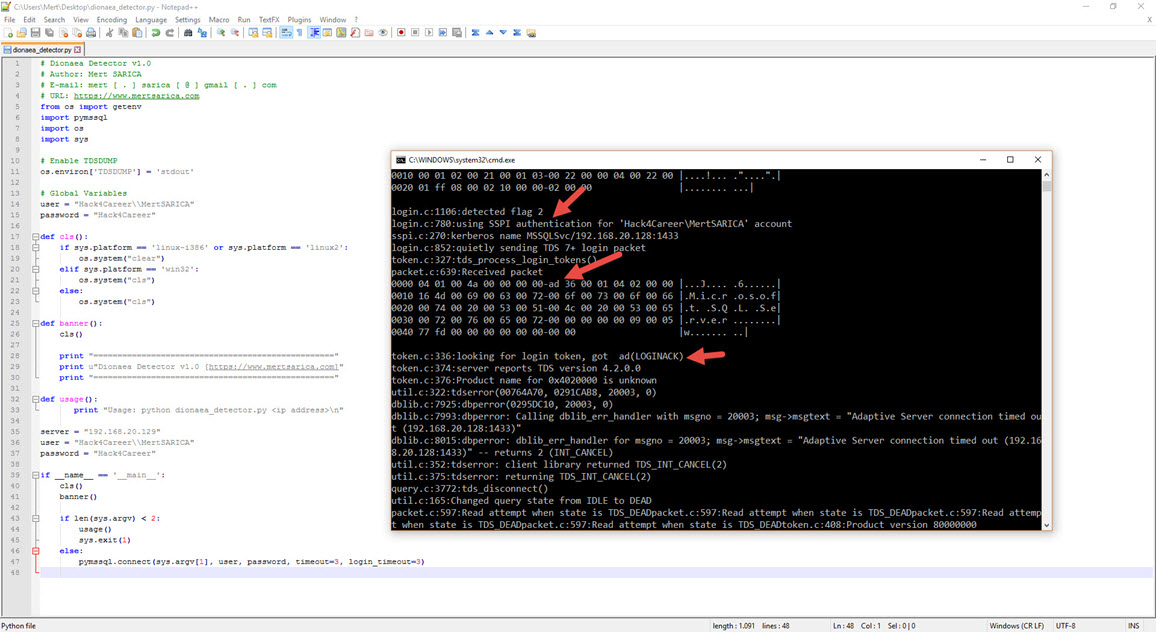
To establish communication between an MSSQL server and a client at the application level, the TDS (Tabular Data Stream) protocol must be used. The TDS protocol supports two types of login methods that have been available since the beginning. The first is login using a username and password, and the second is login using Windows authentication (NTLM). Normally, when attempting to log in with a username and password using the TDS protocol, the response from the MSSQL server should include the LOGINACK_TOKEN (0xAD) token, and when attempting to log in with Windows authentication, it should include the SSPI TOKEN (0xED) token. However, Dionaea returns the same result for both types of requests. :)
Response from Microsoft SQL 2008 Server Express version to a Windows authentication request
Response from Dionaea to a Windows authentication request
In such a situation, I quickly prepared a simple tool named “dionaea_detector.py” using the pymssql library in Python, which can detect this difference. With this tool, I was able to identify the Dionaea honeypot system, which Nmap couldn’t detect, through a simple check. By doing this, I learned how easily malicious individuals can practically detect it.
Exactly, before using a honeypot system, it is important to thoroughly evaluate the advantages and disadvantages of high and low interaction honeypots. Choosing the one that is difficult to detect by cyber attackers or making modifications to existing systems to make it more challenging can be beneficial for you or your organization. By considering these factors and implementing the appropriate measures, you can enhance your security and gain valuable insights into the tactics and techniques used by malicious actors.
Hope to see you in the following articles.
Note: Although the screenshots belong to T-Pot version 16.10, it has been confirmed that the dionaea_detector.py tool can successfully detect Dionaea in the latest version of T-Pot, which is version 17.10 sürümü.