Throughout the world, the trend of encrypting data on end-user systems with malicious software (such as Cryptolocker) and then attempting to profit by selling the decryption key to users continues unabated. Occasionally, security researchers are able to decrypt the data that has been encrypted by malware due to flaws in the encryption algorithms being used. However, in most cases, users are often forced to pay the high ransom demanded by malicious individuals in order to regain access to their files. With each incident, the value of data backups becomes more evident. However, as long as there are users who act on impulse rather than heeding advice, it seems unlikely that malicious actors will easily give up on this lucrative avenue in the near future.
Indeed, with the rapid increase in cyber attacks, the ability to detect threats and respond to them promptly has become of great importance for organizations. In fact, visionary companies have started embracing the practice of cyber threat hunting, aiming to identify threats that can bypass existing security technologies within their networks and systems. When looking at the technologies that enable threat hunting, you will often find that many of them support Yara, a tool that allows you to write your own signatures. Yara provides the capability to create custom rules and signatures that can be used to search for specific patterns or indicators of compromise, enhancing the detection capabilities of organizations in the ever-evolving threat landscape.
When you look at the blog post published by Halil ÖZTÜRKCİ in 2014 regarding Yara, you can see that Yara was predominantly used in digital forensics and memory analysis, particularly with the Volatility tool. However, today you can see that Yara is widely used in various fields, ranging from threat hunting to malware analysis, from commercial products like FireEye NX to open-source and free tools like x64dbg, and even in technologies such as full packet capture. This allows security professionals to define their own rules and signatures that can be used in security systems and devices with Yara support, independent of security vendors. While the idea of writing signatures may not be pleasant for security experts who have had challenging experiences with different security technologies in the past, the situation changes when it comes to Yara because writing rules with Yara is quite simple, yet it provides significant added value, as confirmed by experience.
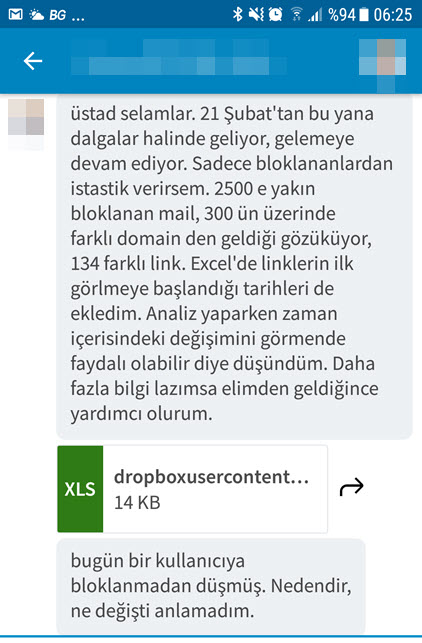
During the recent resurgence of the Cryptolocker outbreak, I noticed on social media platforms and the NetSec email list that some security systems and technologies were inadequate in detecting and preventing such outbreaks. In light of this situation, I wanted to draw attention to how defensive security experts can use a simple signature written with Yara to detect similar threats with modified content when faced with such a situation.
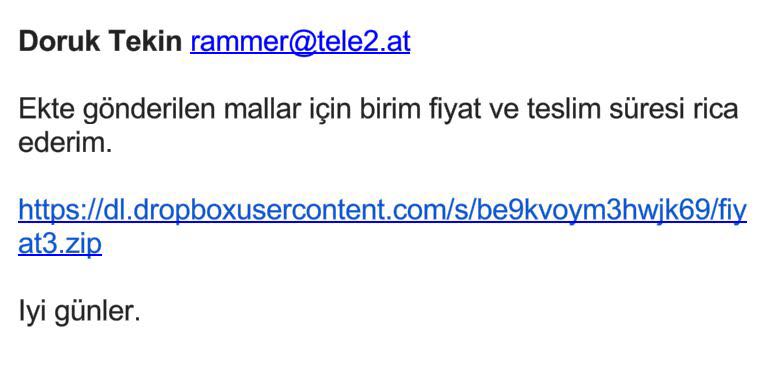
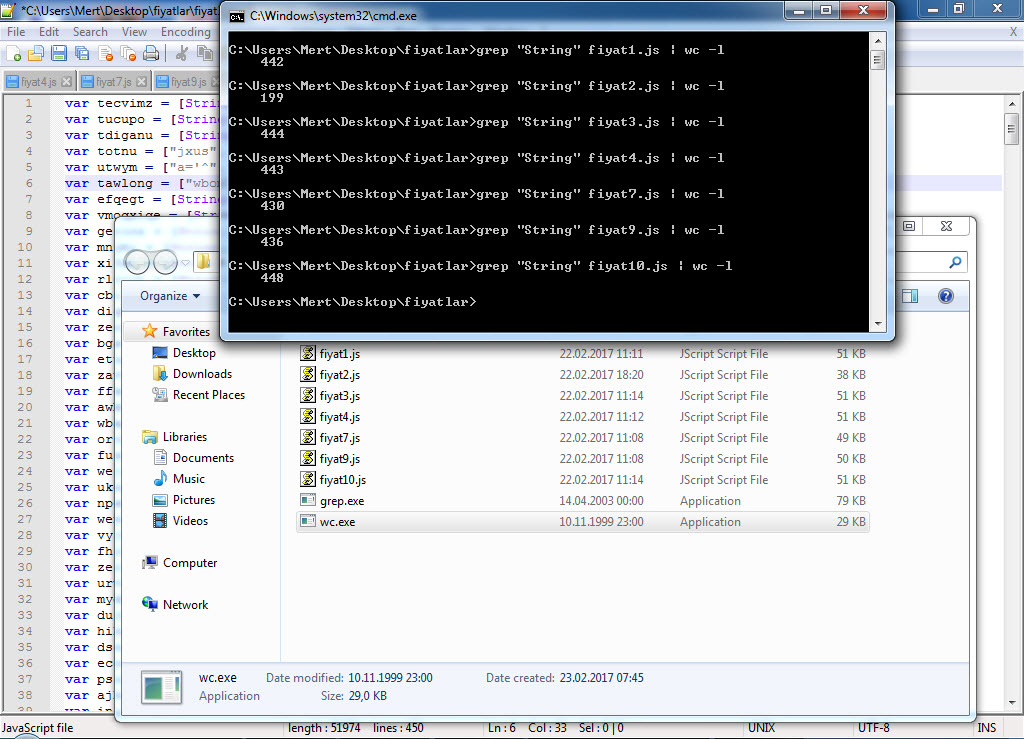
When we look at the Cryptolocker outbreak, we observe that numerous variants of Cryptolocker were being sent from different email addresses under the name “priceX.zip” within a span of 24 hours. Each zip file contained a downloader with obfuscated JavaScript code, which, when executed, would download and run the encryption malware on the system.
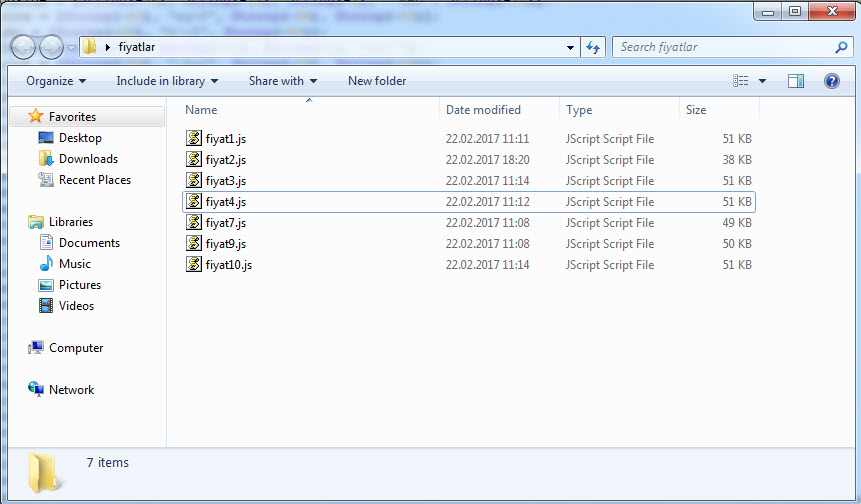
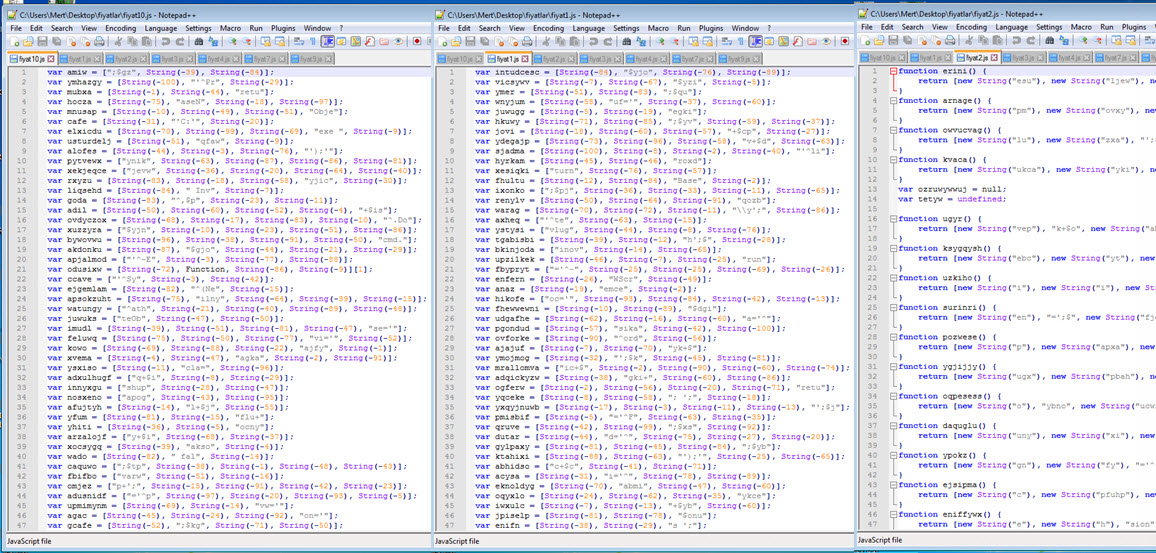
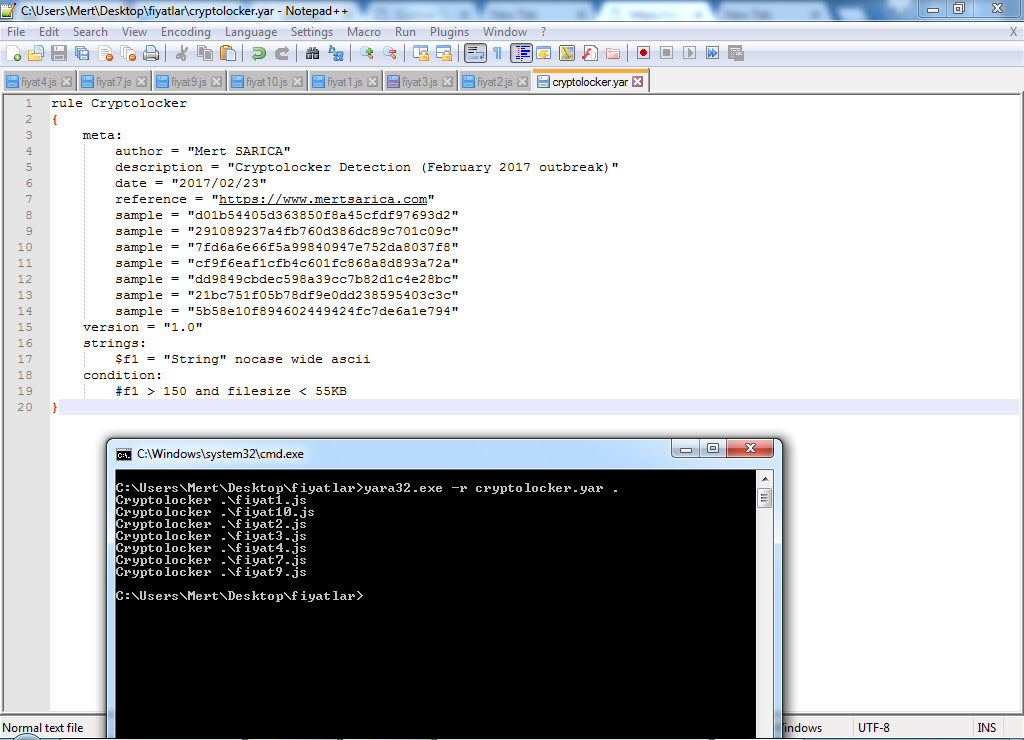
When it comes to detecting variants that differ in size, dimensions, and content, you can easily achieve this using Yara. First, when we list the sizes, we see that all variants except one are smaller than 55 KB. When examining the content of the files, although the content is completely different, we can proceed by analyzing the complex code using the String function to extract the domain name and the downloaded file.
Under normal circumstances, assuming that the number of occurrences of the String function in a file smaller than 55 KB would be less than 150 unless the file is suspicious, we can create a Yara signature using Yara keywords as follows. After confirming the correct functioning of our signature “cryptolocker.yar” and verifying that it can detect all the variants using the Yara tool, we can upload our signature to all security systems and technologies that support Yara. By doing so, we make significant progress in detecting new outbreaks and threats.
Hope to see you in the following articles.